-
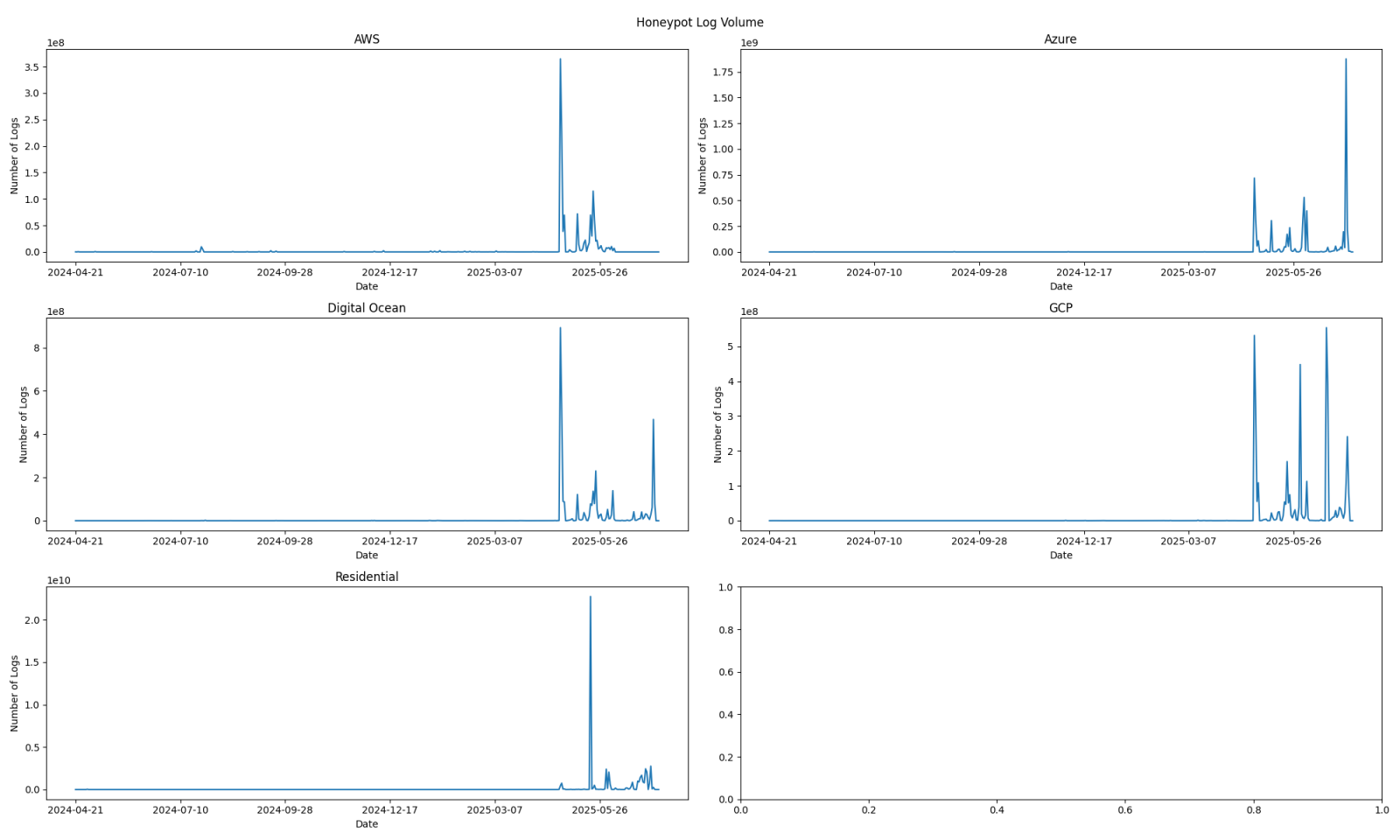
DShield Honeypot Log Volume Increase, (Mon, Jul 14th)
The volume of honeypot logs changes over time. Very rarely are honeypot logs quiet, meaning that there are no internet scans or malicious activity generating logs. Honeypots can see large increases in activity [1], but this has tended to be the exception, rather than the rule. Within the last few months, however, there has been…
-
ISC Stormcast For Monday, July 14th, 2025 https://isc.sans.edu/podcastdetail/9524, (Mon, Jul 14th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
Experimental Suspicious Domain Feed, (Sun, Jul 13th)
We have had a “newly registered domain” feed for a few years. This feed pulls data from ICANN’s centralized zone data service (https://czds.icann.org) and TLS certificate transparency logs. The ICANN CZDS is a good start, but it only offers data from top-level domains collaborating with ICANN. Missing are in particular country-level domains. Country-level zone files…
-
ISC Stormcast For Friday, July 11th, 2025 https://isc.sans.edu/podcastdetail/9522, (Fri, Jul 11th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
ISC Stormcast For Thursday, July 10th, 2025 https://isc.sans.edu/podcastdetail/9520, (Thu, Jul 10th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
![SSH Tunneling in Action: direct-tcp requests [Guest Diary], (Wed, Jul 9th)](/wp-content/uploads/2025/07/Sihui_Neo_pic10-r4lgtY.png)
SSH Tunneling in Action: direct-tcp requests [Guest Diary], (Wed, Jul 9th)
[This is a Guest Diary by Sihui Neo, an ISC intern as part of the SANS.edu BACS program] As part of the SANS degree program curriculum, I had the opportunity to set up a honeypot to monitor log activities mimicking a vulnerable server. I used the AWS free tier EC2 instance to set up the…
-
Setting up Your Own Certificate Authority for Development: Why and How., (Wed, Jul 9th)
There are several reasons why one would set up an internal certificate authority. Some are configured to support strong authentication schemes, some for additional flexibility and convenience. I am going to cover the second part. In particular, it can be helpful for developers to have an internal certificate authority to issue certificates for development purposes.…
-
ISC Stormcast For Wednesday, July 9th, 2025 https://isc.sans.edu/podcastdetail/9518, (Wed, Jul 9th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
Microsoft Patch Tuesday, July 2025, (Tue, Jul 8th)
Today, Microsoft released patches for 130 Microsoft vulnerabilities and 9 additional vulnerabilities not part of Microsoft’s portfolio but distributed by Microsoft. 14 of these are rated critical. Only one of the vulnerabilities was disclosed before being patched, and none of the vulnerabilities have so far been exploited. Noteworthy Vulnerabilities: CVE-2025-49695 and CVE-2025-49696: Both vulnerabilities affect Microsoft Office,…
-
ISC Stormcast For Tuesday, July 8th, 2025 https://isc.sans.edu/podcastdetail/9516, (Tue, Jul 8th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.

