-
Decoding Binary Numeric Expressions, (Mon, Nov 17th)
In diary entry “Formbook Delivered Through Multiple Scripts“, Xavier mentions that the following line: Nestlers= array(79+1,79,80+7,60+9,82,83,72,69,76,76) decodes to the string POWERSHELL. My tool numbers-to-hex.py is a tool that extracts numbers from text files, and converts them to hexadecimal. Like this: I can then use another tool, hex-to-bin.py to convert the hexadecimal numbers to binary, and…
-
ISC Stormcast For Monday, November 17th, 2025 https://isc.sans.edu/podcastdetail/9702, (Mon, Nov 17th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
Finger.exe & ClickFix, (Sun, Nov 16th)
The finger.exe command is used in ClickFix attacks. finger is a very old UNIX command, that was converted to a Windows executable years ago, and is part of Windows since then. In the ClickFix attacks, it is used to retrieve a malicious script via the finger protocol. We wrote about finger.exe about 3 years ago:…
-
SANS Holiday Hack Challenge 2025, (Sun, Nov 16th)
The SANS Holiday Hack Challenge™ 2025 is available. (c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
Honeypot: FortiWeb CVE-2025-64446 Exploits, (Sat, Nov 15th)
Like many have reported, we too noticed exploit attempts for CVE-2025-64446 in our honeypots. These are POST requests to this path: With this User Agent String: And this is the data of the POST request: This creates a new admin user (profile: prof_admin). You can find this JSON data back in this PoC. Didier Stevens…
-
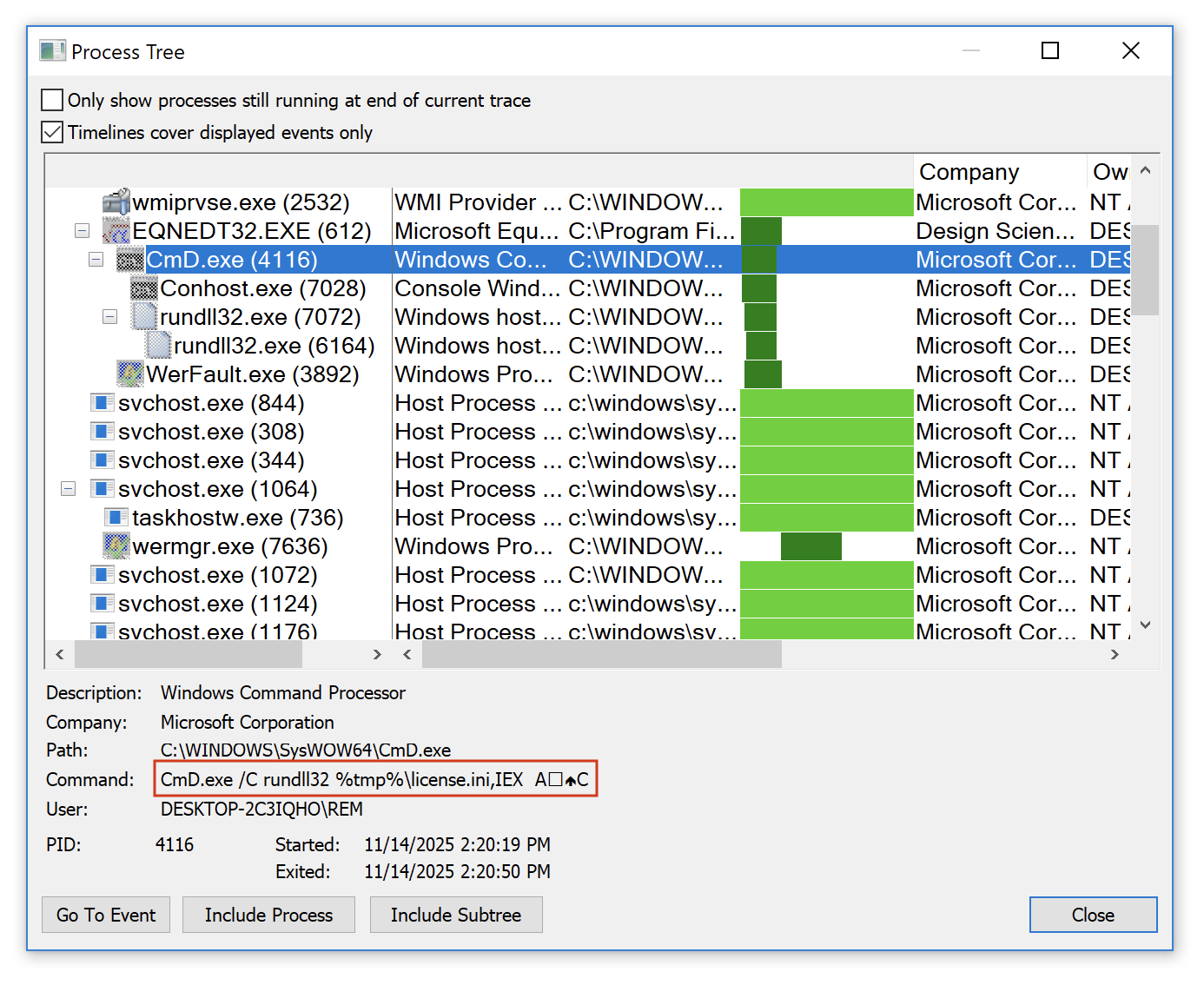
Microsoft Office Russian Dolls, (Fri, Nov 14th)
You probably know what are the Russian or Matryoshka dolls. It’s a set of wooden dolls of decreasing size placed one inside another[1]. I found an interesting Microsoft Office document that behaves like this. There was a big decrease in malicious Office documents due to the new Microsoft rules to prevent automatic VBA macros execution. But they remain used, especially RTF…
-
ISC Stormcast For Friday, November 14th, 2025 https://isc.sans.edu/podcastdetail/9700, (Fri, Nov 14th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
Formbook Delivered Through Multiple Scripts, (Thu, Nov 13th)
When I’m teachning FOR610[1], I always say to my students that reverse engineering does not only apply to “executable files” (read: PE or ELF files). Most of the time, the infection path involves many stages to defeat the Security Analyst or security controls. Here is an example that I found yesterday. An email was received…
-
ISC Stormcast For Thursday, November 13th, 2025 https://isc.sans.edu/podcastdetail/9698, (Thu, Nov 13th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
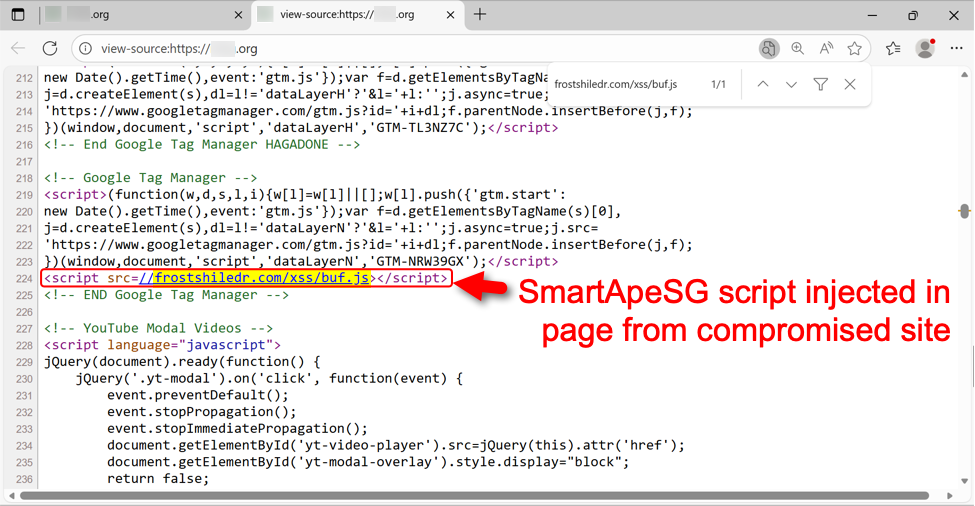
SmartApeSG campaign uses ClickFix page to push NetSupport RAT, (Wed, Nov 12th)
Introduction This diary describes a NetSupport RAT infection I generated in my lab from the SmartApeSG campaign that used a ClickFix-style fake CAPTCHA page. Known as ZPHP or HANEYMANEY, SmartApeSG is a campaign reported as early as June 2024. When it started, this campaign used fake browser update pages. But it currently uses the ClickFix method of fake…

