-

Webshells Hiding in .well-known Places, (Thu, Sep 25th)
Ever so often, I see requests for files in .well-known recorded by our honeypots. As an example: GET /.well-known/xin1.php?p Host: [honeypot host name] The file names indicate that they are likely looking for webshells. In my opinion, the reason they are looking in .well-known is that this makes a decent place to hide webshells without…
-
ISC Stormcast For Thursday, September 25th, 2025 https://isc.sans.edu/podcastdetail/9628, (Thu, Sep 25th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
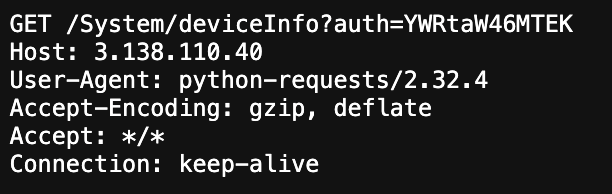
Exploit Attempts Against Older Hikvision Camera Vulnerability, (Wed, Sep 24th)
I notice a new URL showing up in our web honeypot logs, which looked a bit interesting: /System/deviceInfo?auth=YWRtaW46MTEK The full request: GET /System/deviceInfo?auth=YWRtaW46MTEK Host: 3.87.70.24 User-Agent: python-requests/2.32.4 Accept-Encoding: gzip, deflate Accept: */* Connection: keep-alive The “auth” string caught my attention, in particular as it was followed by a base64 encoded string. The string decodes to…
-
ISC Stormcast For Wednesday, September 24th, 2025 https://isc.sans.edu/podcastdetail/9626, (Wed, Sep 24th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
![[Guest Diary] Distracting the Analyst for Fun and Profit, (Tue, Sep 23rd)](/wp-content/uploads/2025/09/2025-09-23_figure1-5vKbCt.png)
[Guest Diary] Distracting the Analyst for Fun and Profit, (Tue, Sep 23rd)
[This is a Guest Diary by Taylor House, an ISC intern as part of the SANS.edu Bachelor’s Degree in Applied Cybersecurity (BACS) program [1].] Distributed denial of service (DDoS) attacks are a type of cyber-attack where the threat actor attempts to disrupt a service by flooding the target with a ton of requests to overload…
-
ISC Stormcast For Tuesday, September 23rd, 2025 https://isc.sans.edu/podcastdetail/9624, (Tue, Sep 23rd)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
ISC Stormcast For Monday, September 22nd, 2025 https://isc.sans.edu/podcastdetail/9622, (Mon, Sep 22nd)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
Help Wanted: What are these odd reuqests about?, (Sun, Sep 21st)
Looking at our web honeypot data, I came across an odd new request header I hadn’t seen before: “X-Forwarded-App”. My first guess was that this is yet another issue with a proxy-server bucket brigade spilling secrets when a particular “App” is connecting to it. So I dove in a bit deeper, and found requests like…
-
ISC Stormcast For Friday, September 19th, 2025 https://isc.sans.edu/podcastdetail/9620, (Fri, Sep 19th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
ISC Stormcast For Thursday, September 18th, 2025 https://isc.sans.edu/podcastdetail/9618, (Thu, Sep 18th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.

