-
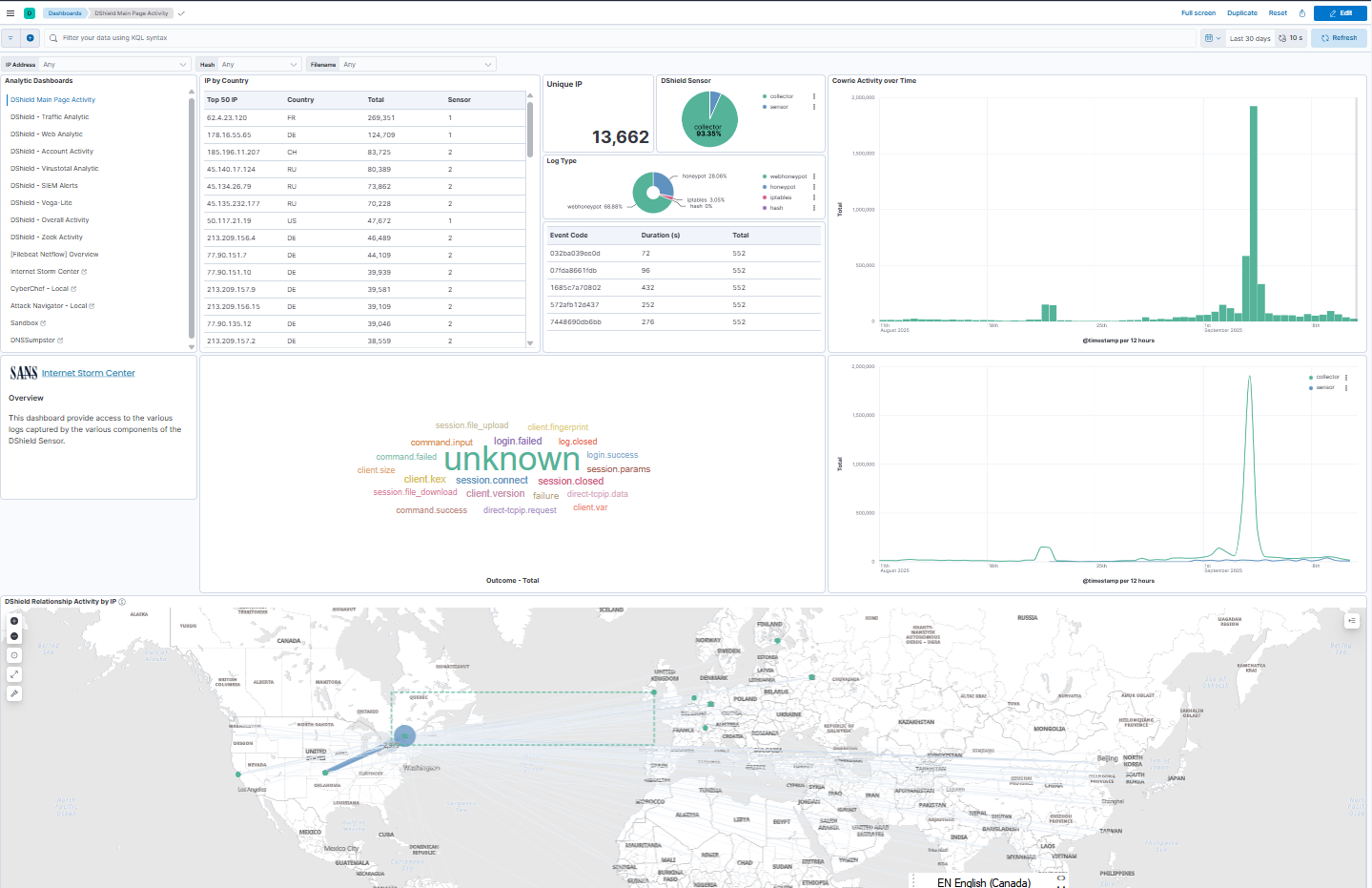
DShield SIEM Docker Updates, (Wed, Sep 10th)
Since the last update [5], over the past few months I added several enhancements to DShield SIEM and webhoneypot sensor collection that included an update to the interface to help with DShield sensor analysis. I updated the main dashboard to have all the main analytic tools listed on the left for quick access to all…
-
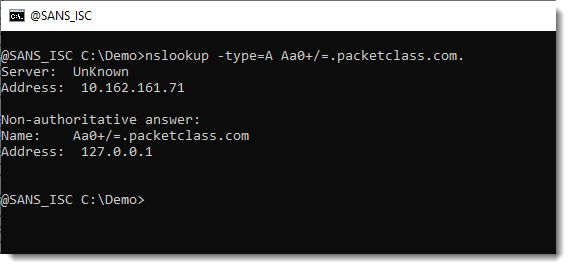
BASE64 Over DNS, (Wed, Sep 10th)
On the Stormcast, Johannes talked about BASE64 and DNS used by a backdoor. I was interested to learn more about this, because DNS labels can only contain letters, digits and a hyphen. If you make a distinction between uppercase and lowercase letters, you have exactly 63 characters to choose from. While BASE64 requires 64 characters…
-
ISC Stormcast For Wednesday, September 10th, 2025 https://isc.sans.edu/podcastdetail/9606, (Wed, Sep 10th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
Microsoft Patch Tuesday September 2025, (Tue, Sep 9th)
As part of its September patch Tuesday, Microsoft addressed 177 different vulnerabilities, 86 of which affect Microsoft products. None of the vulnerabilities has been exploited before today. Two of the vulnerabilities were already made public. Microsoft rates 13 of the vulnerabilities are critical. You will see a number of vulnerabilities without assigned severity. These vulnerabilities…
-
ISC Stormcast For Tuesday, September 9th, 2025 https://isc.sans.edu/podcastdetail/9604, (Tue, Sep 9th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
HTTP Request Signatures, (Mon, Sep 8th)
This weekend, I noticed three related headers being used in requests to some of our honeypots for the first time [1]: Signature-Input Signature-Agent Signature These headers are related to a relatively new feature, HTTP Message Signatures, which was standardized in RFC 9421 in February last year [2]. First, what is the problem that HTTP Request Signatures…
-
ISC Stormcast For Monday, September 8th, 2025 https://isc.sans.edu/podcastdetail/9602, (Mon, Sep 8th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
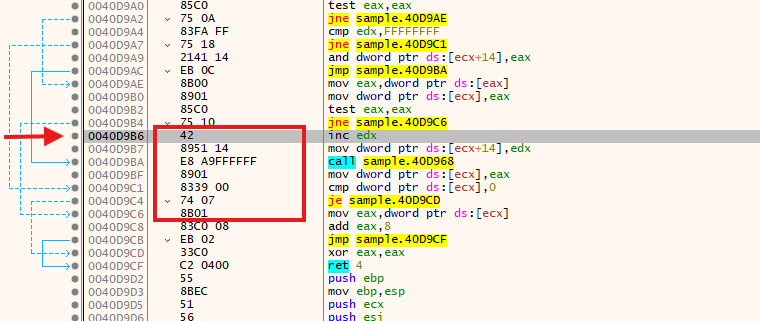
From YARA Offsets to Virtual Addresses, (Fri, Sep 5th)
YARA is an excellent tool that most of you probably already know and use daily. If you don’t, search on isc.sans.edu, we have a bunch of diaries about it[1]. YARA is very powerful because you can search for arrays of bytes that represent executable code. In this case, you provide the hexadecimal representation of the…
-
ISC Stormcast For Friday, September 5th, 2025 https://isc.sans.edu/podcastdetail/9600, (Fri, Sep 5th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
ISC Stormcast For Thursday, September 4th, 2025 https://isc.sans.edu/podcastdetail/9598, (Thu, Sep 4th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.

