-
ISC Stormcast For Wednesday, August 20th, 2025 https://isc.sans.edu/podcastdetail/9578, (Wed, Aug 20th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
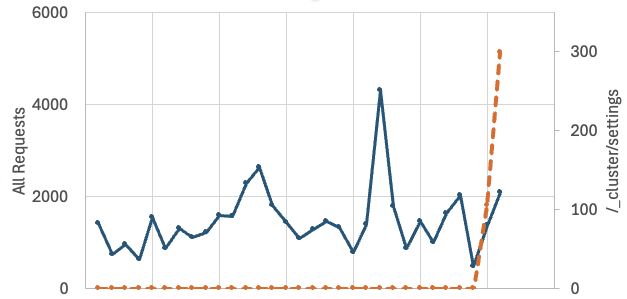
Increased Elasticsearch Recognizance Scans, (Tue, Aug 19th)
I noticed an increase in scans that appear to try to identify Elasticsearch instances. Elasticsearch is not a new target. Its ability to easily store and manage JSON data, combined with a simple HTTP API, makes it a convenient tool to store data that is directly accessible from the browser via JavaScript. Elasticsearch has, in…
-
ISC Stormcast For Tuesday, August 19th, 2025 https://isc.sans.edu/podcastdetail/9576, (Tue, Aug 19th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
Keeping an Eye on MFA-Bombing Attacks, (Mon, Aug 18th)
I recently woke up (as one does each day, hopefully) and saw a few Microsoft MFA prompts had pinged me overnight. Since I had just awakened, I just deleted them, then two minutes later clued in – this means that one of my passwords was compromised, and I had no idea which site the compromised…
-
ISC Stormcast For Monday, August 18th, 2025 https://isc.sans.edu/podcastdetail/9574, (Mon, Aug 18th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
ISC Stormcast For Friday, August 15th, 2025 https://isc.sans.edu/podcastdetail/9572, (Fri, Aug 15th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
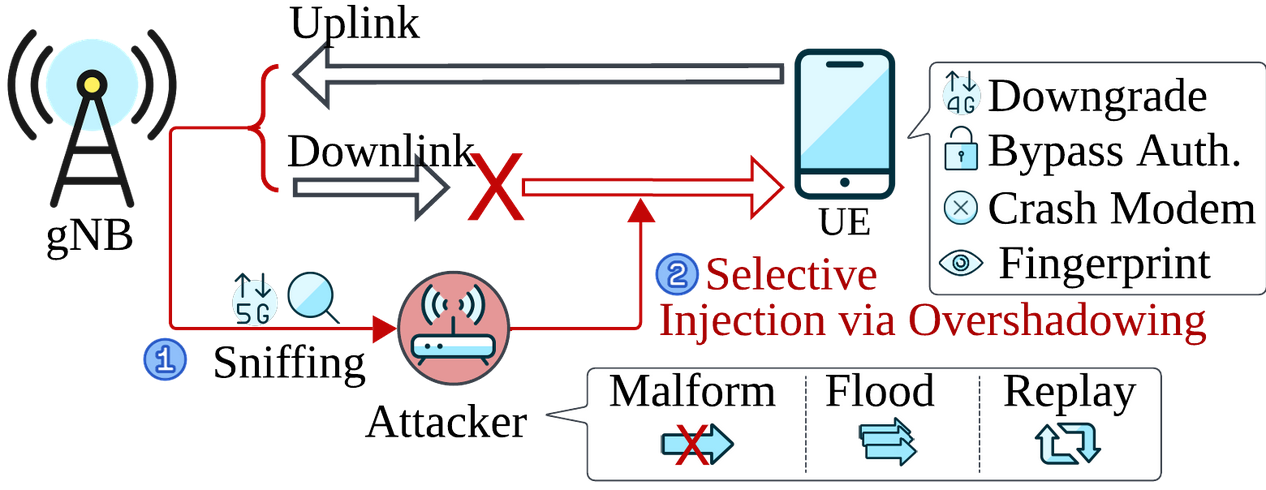
SNI5GECT: Sniffing and Injecting 5G Traffic Without Rogue Base Stations, (Thu, Aug 14th)
As the world gradually adopts and transitions to using 5G for mobile, operational technology (OT), automation and Internet-of-Things (IoT) devices, a secure 5G network infrastructure remains critical. Recently, the Automated Systems SEcuriTy (ASSET) Research Group have released a new framework named SNI5GECT [pronounced as Sni-f-Gect (sniff + 5G + inject)] that enables users of the…
-
ISC Stormcast For Thursday, August 14th, 2025 https://isc.sans.edu/podcastdetail/9570, (Thu, Aug 14th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
![AI and Faster Attack Analysis [Guest Diary], (Wed, Aug 13th)](/wp-content/uploads/2025/08/Joseph_Noa_Picture1-oV8EJm.png)
AI and Faster Attack Analysis [Guest Diary], (Wed, Aug 13th)
[This is a Guest Diary by Joseph Noa, an ISC intern as part of the SANS.edu BACS program] Introduction Time is of the essence when it comes to attacks and understanding what you’re seeing can be tricky when under pressure. As security professionals, we need to use every tool available to us so we can…
-
CVE-2017-11882 Will Never Die, (Wed, Aug 13th)
One of the key messages broadcasted by security professionals is: “Patch, patch and patch again!”. But they are nasty vulnerabilities that remain exploited by attackers even if they are pretty old. %%cve:2017-11882%% is one of them: this remote code execution affects Microsoft Office and, more precisely, the good old “Equation Editor”. This tool was even killed…

