-
![SSH Tunneling in Action: direct-tcp requests [Guest Diary], (Wed, Jul 9th)](/wp-content/uploads/2025/07/Sihui_Neo_pic10-r4lgtY.png)
SSH Tunneling in Action: direct-tcp requests [Guest Diary], (Wed, Jul 9th)
[This is a Guest Diary by Sihui Neo, an ISC intern as part of the SANS.edu BACS program] As part of the SANS degree program curriculum, I had the opportunity to set up a honeypot to monitor log activities mimicking a vulnerable server. I used the AWS free tier EC2 instance to set up the…
-
Setting up Your Own Certificate Authority for Development: Why and How., (Wed, Jul 9th)
There are several reasons why one would set up an internal certificate authority. Some are configured to support strong authentication schemes, some for additional flexibility and convenience. I am going to cover the second part. In particular, it can be helpful for developers to have an internal certificate authority to issue certificates for development purposes.…
-
ISC Stormcast For Wednesday, July 9th, 2025 https://isc.sans.edu/podcastdetail/9518, (Wed, Jul 9th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
Microsoft Patch Tuesday, July 2025, (Tue, Jul 8th)
Today, Microsoft released patches for 130 Microsoft vulnerabilities and 9 additional vulnerabilities not part of Microsoft’s portfolio but distributed by Microsoft. 14 of these are rated critical. Only one of the vulnerabilities was disclosed before being patched, and none of the vulnerabilities have so far been exploited. Noteworthy Vulnerabilities: CVE-2025-49695 and CVE-2025-49696: Both vulnerabilities affect Microsoft Office,…
-
ISC Stormcast For Tuesday, July 8th, 2025 https://isc.sans.edu/podcastdetail/9516, (Tue, Jul 8th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
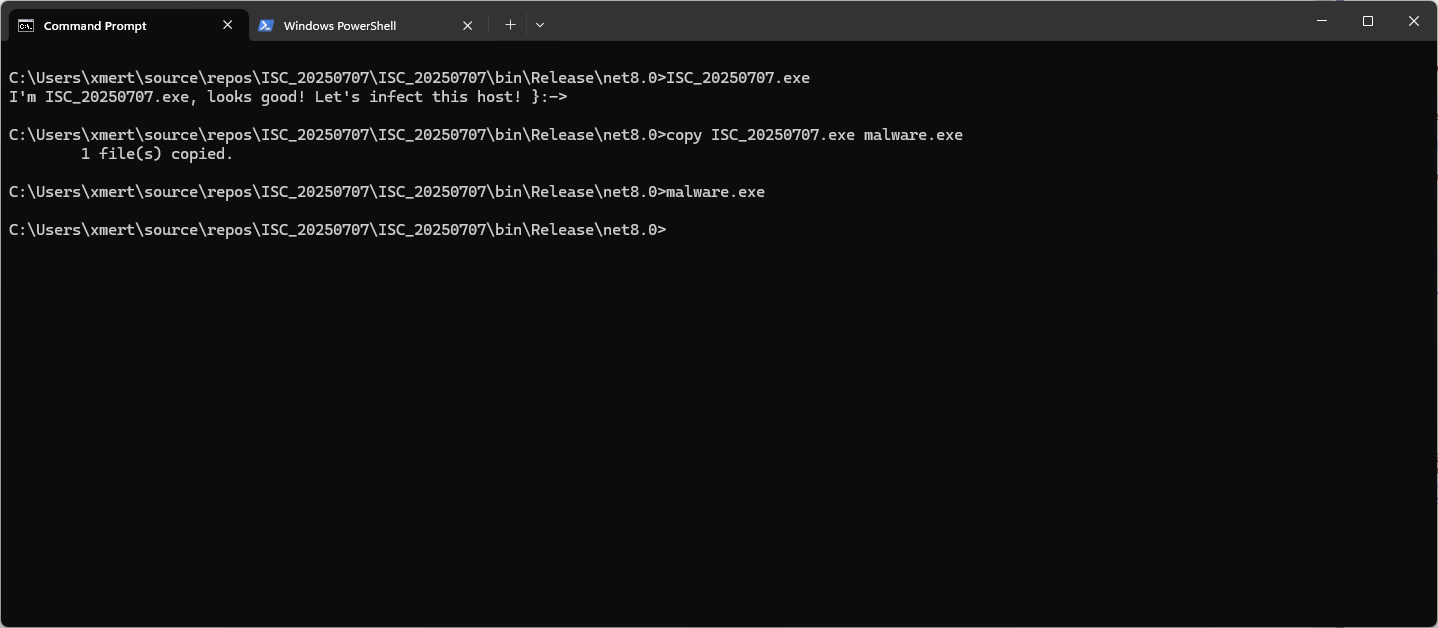
What’s My (File)Name?, (Mon, Jul 7th)
Modern malware implements a lot of anti-debugging and anti-analysis features. Today, when a malware is spread in the wild, there are chances that it will be automatically sent into a automatic analysis pipe, and a sandbox. To analyze a sample in a sandbox, it must be “copied” into the sandbox and executed. This can happen…
-
ISC Stormcast For Monday, July 7th, 2025 https://isc.sans.edu/podcastdetail/9514, (Mon, Jul 7th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
A few interesting and notable ssh/telnet usernames, (Sun, Jul 6th)
Just looked at our telnet/ssh honeypot data, and found some interesting new usernames that attackers attempted to use: “notachancethisisreal“ This username is likely used to detect Cowrie (and other) honeypots. Cowrie is often configured to accept logins randomly. No matter the username/password combination used, the login will succeed every few times. This is supposed to…
-
ISC Stormcast For Thursday, July 3rd, 2025 https://isc.sans.edu/podcastdetail/9512, (Thu, Jul 3rd)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
ISC Stormcast For Monday, June 30th, 2025 https://isc.sans.edu/podcastdetail/9510, (Mon, Jun 30th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.

