-
ISC Stormcast For Wednesday, June 11th, 2025 https://isc.sans.edu/podcastdetail/9488, (Wed, Jun 11th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
Microsoft Patch Tuesday June 2025, (Tue, Jun 10th)
Microsoft today released patches for 67 vulnerabilities. 10 of these vulnerabilities are rated critical. One vulnerability has already been exploited and another vulnerability has been publicly disclosed before today. Notable Vulnerabilities: CVE-2025-33053: WebDAV remote code execution vulnerability. This vulnerability has already been exploited. Microsoft rates it as important. This affects the client part of WebDAV,…
-
ISC Stormcast For Tuesday, June 10th, 2025 https://isc.sans.edu/podcastdetail/9486, (Tue, Jun 10th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-

OctoSQL & Vulnerability Data, (Sun, Jun 8th)
As an avid daily reader of TLDR Information Security I benefit twofold. First, I gain interesting insights and recommendations regarding launches and tools, where I first learned about OctoSQL. Second, concerning vulnerability details inevitably land in my inbox on a near daily basis. Aside from my recommendation to join the TLDR InfoSec mailing list, diary readers also benefit twofold…
-
ISC Stormcast For Monday, June 9th, 2025 https://isc.sans.edu/podcastdetail/9484, (Mon, Jun 9th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
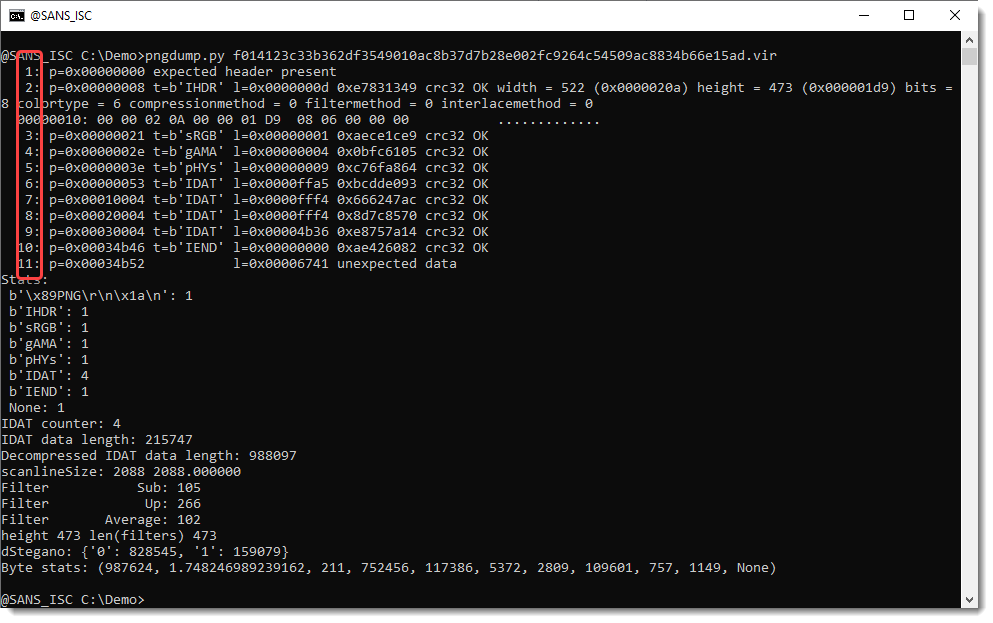
Extracting With pngdump.py, (Sun, Jun 8th)
Inspired by Xavier’s diary entry “A PNG Image With an Embedded Gift“, I updated my pngdump.py program to enable the extraction of chunks and extra data (similar to my other analysis tools, like pngdump.py). Here is the analysis of the trojanized PNG file Xavier discussed: Notice that this PNG file has 11 “items”: 10 valid…
-
Wireshark 4.4.7 Released, (Sun, Jun 8th)
Wireshark release 4.4.7 fixes 1 vulnerability (%%cve:2025-5601%%) and 8 bugs. Didier Stevens Senior handler blog.DidierStevens.com (c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
ISC Stormcast For Friday, June 6th, 2025 https://isc.sans.edu/podcastdetail/9482, (Fri, Jun 6th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
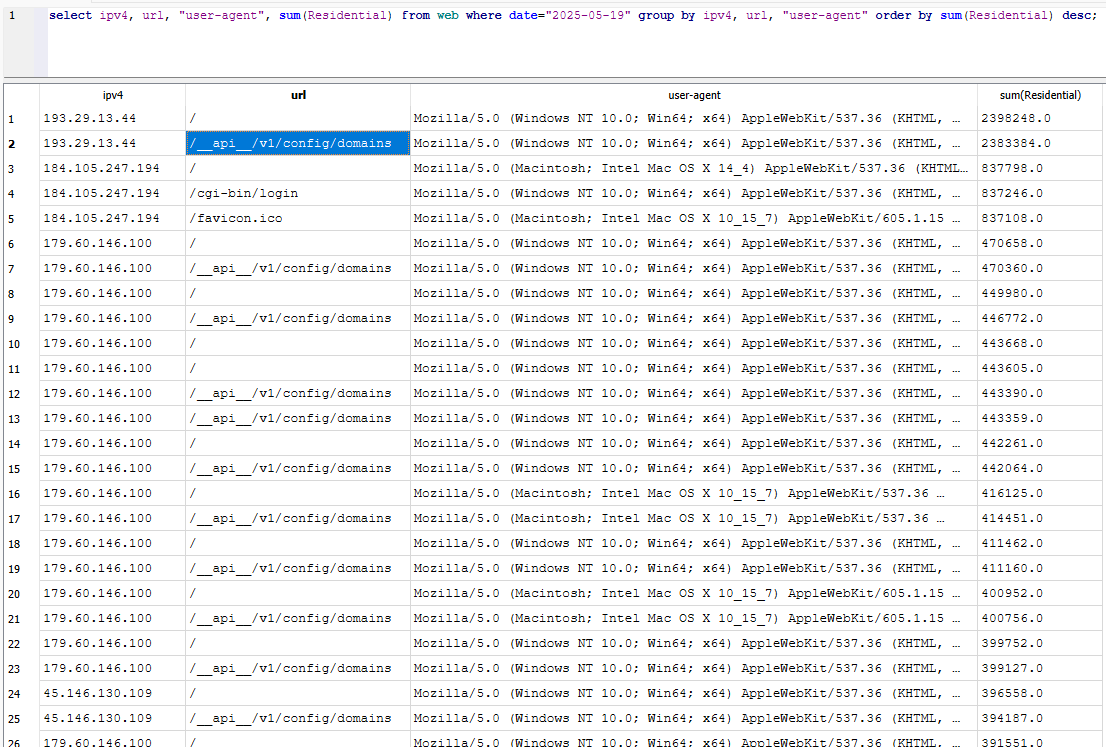
Upcoming DShield Honeypot Changes and Customizations, (Fri, Jun 6th)
There are some upcoming DShield honeypot [1] changes that introduce some opportunities for additional customization and data analysis. For most users, no additional actions are needed. A couple of those changes: dshield.ini file move from /etc/ to /srv/dshield/etc/ – A symbolic link will exist for the previous file location for backward compatibility. If you have…
-
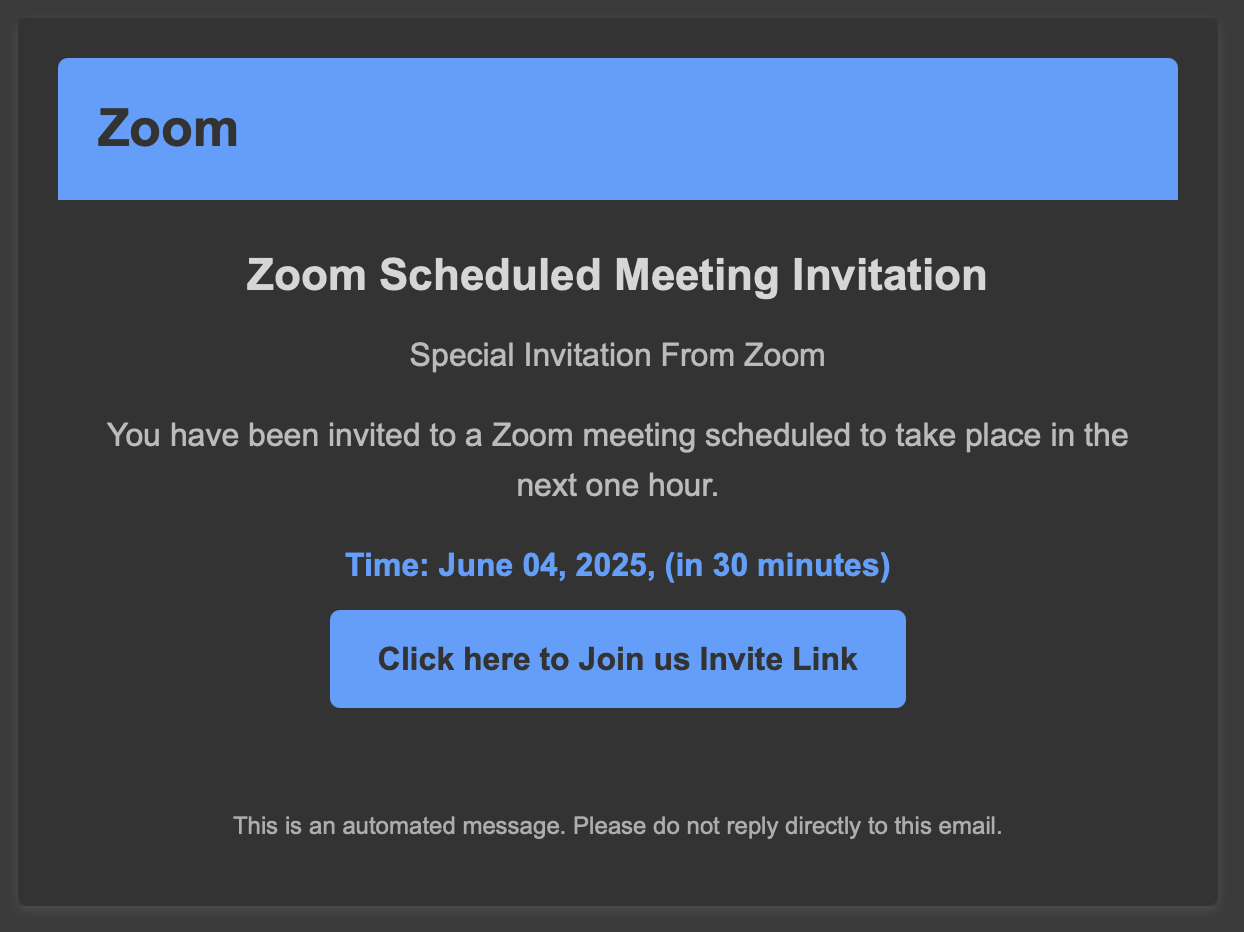
Be Careful With Fake Zoom Client Downloads, (Thu, Jun 5th)
Collaborative tools are really popular these days. Since the COVID-19 pandemic, many people switched to remote work positions and we need to collaborate with our colleagues or customers every day. Tools like Microsoft Teams, Zoom, WebEx, (name your best solution), … became popular and must be regularly updated.Yesterday, I received an interesting email with a fake…

