-
ISC Stormcast For Friday, April 25th, 2025 https://isc.sans.edu/podcastdetail/9424, (Fri, Apr 25th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-

Attacks against Teltonika Networks SMS Gateways, (Thu, Apr 24th)
Ever wonder where all the SMS spam comes from? If you are trying to send SMS “at scale,” there are a few options: You could sign up for a messaging provider like Twilio, the AWS SNS service, or several similar services. These services offer easily scriptable and affordable ways to send SMS messages. We have…
-
ISC Stormcast For Thursday, April 24th, 2025 https://isc.sans.edu/podcastdetail/9422, (Thu, Apr 24th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
ISC Stormcast For Wednesday, April 23rd, 2025 https://isc.sans.edu/podcastdetail/9420, (Wed, Apr 23rd)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
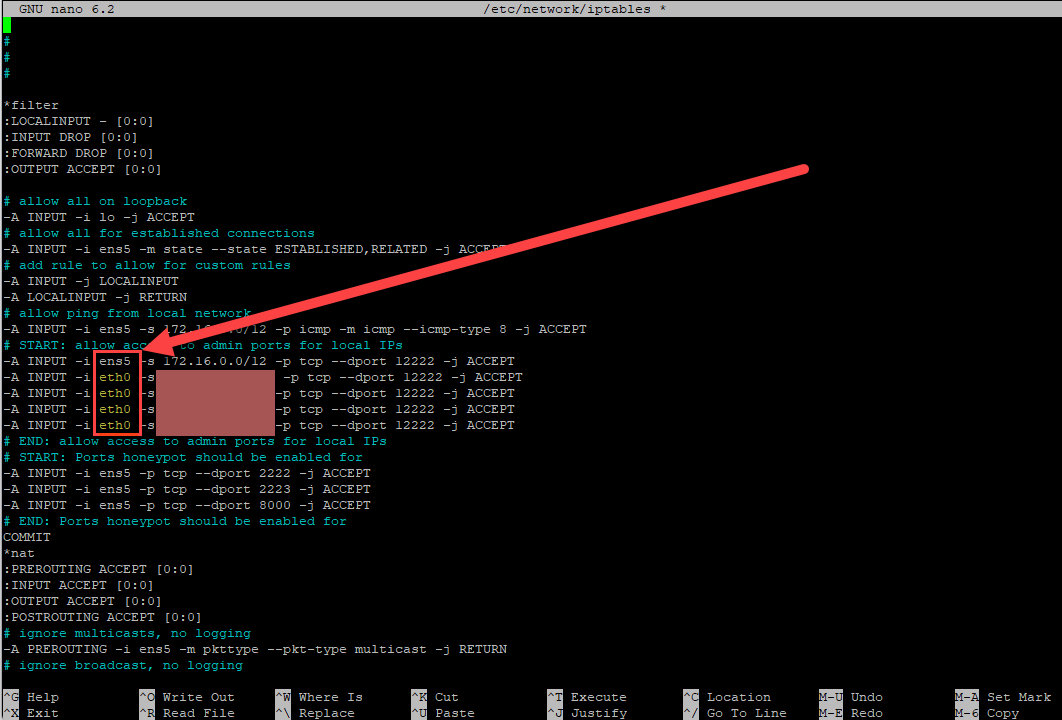
Honeypot Iptables Maintenance and DShield-SIEM Logging, (Wed, Apr 23rd)
In the last week I ran into some issues that I hadn’t anticipated: Residential IP changed, some honeypots inacessible remotely Rebuilit DShield-SIEM [1], Zeek logs not displaying Be mindful of network interface labels First, an IP address changing for a residential network is not uncommon. Some ISPs may regularly change IP addresses for homes…
-
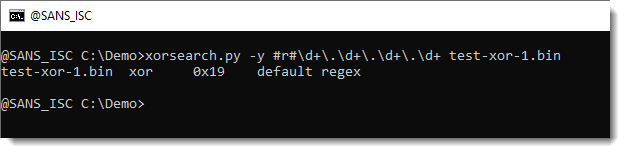
xorsearch.py: “Ad Hoc YARA Rules”, (Tue, Apr 22nd)
In diary entry “xorsearch.py: Searching With Regexes” I showed how one can let xorsearch.py generate a YARA rule with a given regular expression. This is a feature in many of my tools that support YARA, and I call it “Ad Hoc Yara Rules“: rules that are created on the spot with your input. Here is…
-
ISC Stormcast For Tuesday, April 22nd, 2025 https://isc.sans.edu/podcastdetail/9418, (Tue, Apr 22nd)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
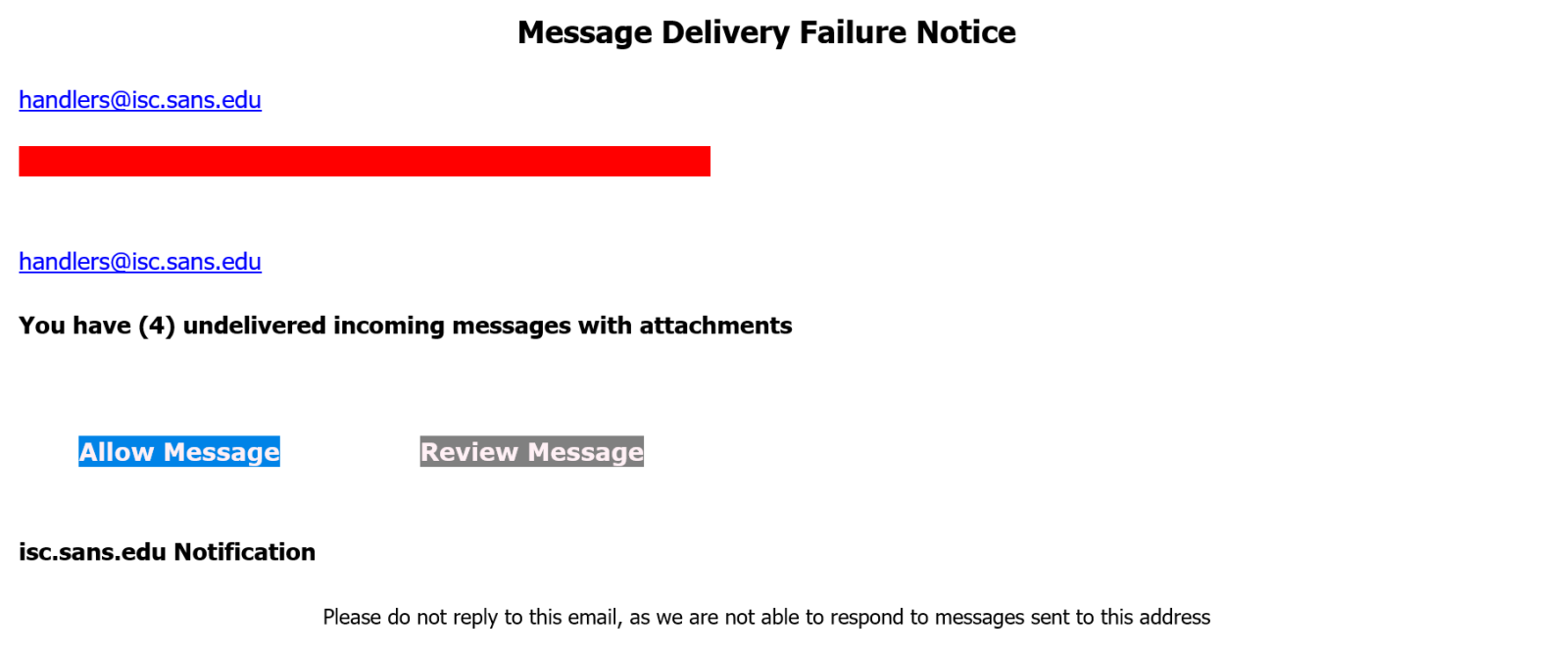
It’s 2025… so why are obviously malicious advertising URLs still going strong?, (Mon, Apr 21st)
While the old adage stating that “the human factor is the weakest link in the cyber security chain” will undoubtedly stay relevant in the near (and possibly far) future, the truth is that the tech industry could – and should – help alleviate the problem significantly more than it does today. One clear example of…
-
ISC Stormcast For Monday, April 21st, 2025 https://isc.sans.edu/podcastdetail/9416, (Mon, Apr 21st)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
Wireshark 4.4.6 Released, (Sun, Apr 20th)
Wireshark release 4.4.6 fixes 14 bugs. Didier Stevens Senior handler blog.DidierStevens.com (c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.

