-
ISC Stormcast For Friday, March 28th, 2025 https://isc.sans.edu/podcastdetail/9384, (Fri, Mar 28th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
Sitecore “thumbnailsaccesstoken” Deserialization Scans (and some new reports) CVE-2025-27218, (Thu, Mar 27th)
On March 6th, Searchlight Cyber published a blog revealing details about a new deserialization vulnerability in Sitecore [1]. Sitecore calls itself a “Digital Experience Platform (CXP),” which is a fancy content management system (CMS). Sitecore itself is written in .Net and is often sold as part of a solution offered by Sitecore partners. Like other CMSs,…
-
ISC Stormcast For Thursday, March 27th, 2025 https://isc.sans.edu/podcastdetail/9382, (Thu, Mar 27th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
ISC Stormcast For Wednesday, March 26th, 2025 https://isc.sans.edu/podcastdetail/9380, (Wed, Mar 26th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
![[Guest Diary] Leveraging CNNs and Entropy-Based Feature Selection to Identify Potential Malware Artifacts of Interest, (Wed, Mar 26th)](/wp-content/uploads/2025/03/2025-3-26_Fig1-nln5wU.png)
[Guest Diary] Leveraging CNNs and Entropy-Based Feature Selection to Identify Potential Malware Artifacts of Interest, (Wed, Mar 26th)
[This is a Guest Diary by Wee Ki Joon, an ISC intern as part of the SANS.edu Bachelor’s Degree in Applied Cybersecurity (BACS) program [1].] Executive Summary This diary explores a novel methodology for classifying malware by integrating entropy-driven feature selection [2] with a specialized Convolutional Neural Network (CNN) [3]. Motivated by the increasing obfuscation…
-
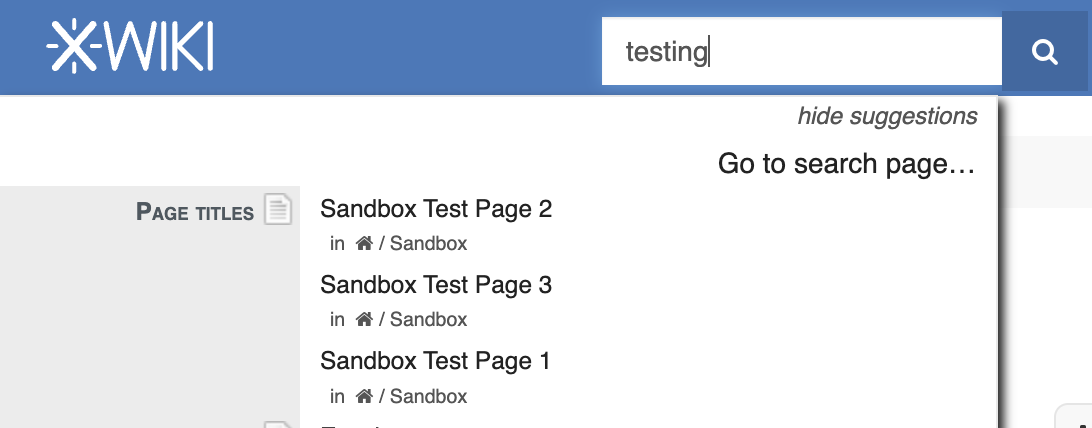
X-Wiki Search Vulnerability exploit attempts (CVE-2024-3721), (Tue, Mar 25th)
Creating a secure Wiki is hard. The purpose of a wiki is to allow “random” users to edit web pages. A good Wiki provides users with great flexibility, but with great flexibility comes an even “greater” attack surface. File uploads and markup (or markdown) are all well-known security issues affecting various Wikis in the past.…
-
ISC Stormcast For Tuesday, March 25th, 2025 https://isc.sans.edu/podcastdetail/9378, (Tue, Mar 25th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
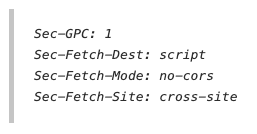
Privacy Aware Bots, (Mon, Mar 24th)
Staring long enough at honeypot logs, I am sure you will come across one or the other “oddity.” Something that at first does not make any sense, but then, in some way, does make sense. After looking at the Next.js issue yesterday, I looked through our logs for other odd headers I may spot. I…
-
ISC Stormcast For Monday, March 24th, 2025 https://isc.sans.edu/podcastdetail/9376, (Mon, Mar 24th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-

Let’s Talk About HTTP Headers., (Sun, Mar 23rd)
Walking my dog earlier, I came across the sign on the right. Having just looked at yet another middleware/HTTP header issue (the Next.js problem that became public this weekend) [1], I figured I should write something about HTTP headers. We all know HTTP headers. But it appears some do not know them well enough. Let’s…

