-
ISC Stormcast For Friday, March 14th, 2025 https://isc.sans.edu/podcastdetail/9364, (Fri, Mar 14th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
ISC Stormcast For Thursday, March 13th, 2025 https://isc.sans.edu/podcastdetail/9362, (Thu, Mar 13th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
File Hashes Analysis with Power BI from Data Stored in DShield SIEM, (Wed, Mar 12th)
I previously used Power BI [2] to analyze DShield sensor data and this time I wanted to show how it could be used by selecting certain type of data as a large dataset and export it for analysis. This time, I ran a query in Elastic Discover and exported that data to analyze it in…
-
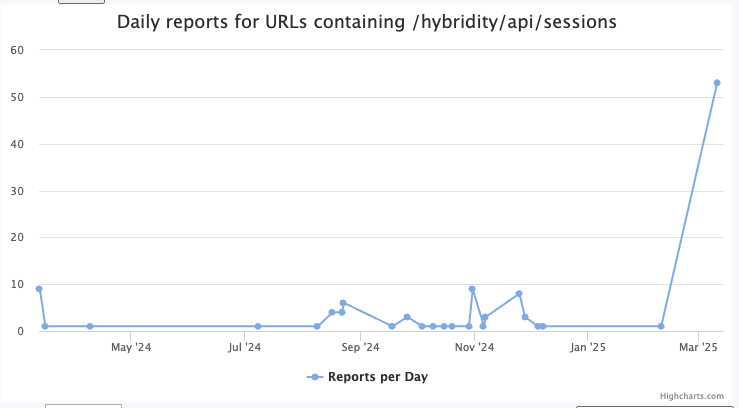
Scans for VMWare Hybrid Cloud Extension (HCX) API (Brutefording Credentials?), (Wed, Mar 12th)
Today, I noticed increased scans for the VMWare Hyprid Cloud Extension (HCX) “sessions” endpoint. These endpoints are sometimes associated with exploit attempts for various VMWare vulnerabilities to determine if the system is running the extensions or to gather additional information to aid exploitation. The specific URL seen above is /hybridity/api/sessions This particular request is likely…
-
ISC Stormcast For Wednesday, March 12th, 2025 https://isc.sans.edu/podcastdetail/9360, (Wed, Mar 12th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
Microsoft Patch Tuesday: March 2025, (Tue, Mar 11th)
The March patch Tuesday looks like a fairly light affair, with only 51 vulnerabilities total and only six rated as critical. However, this patch Tuesday also includes six patches for already exploited, aka “0-Day” vulnerabilities. None of the already exploited vulnerabilities are rated as critical. Today’s most interesting vulnerability is a not-yet exploited critical vulnerability…
-
ISC Stormcast For Tuesday, March 11th, 2025 https://isc.sans.edu/podcastdetail/9358, (Tue, Mar 11th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
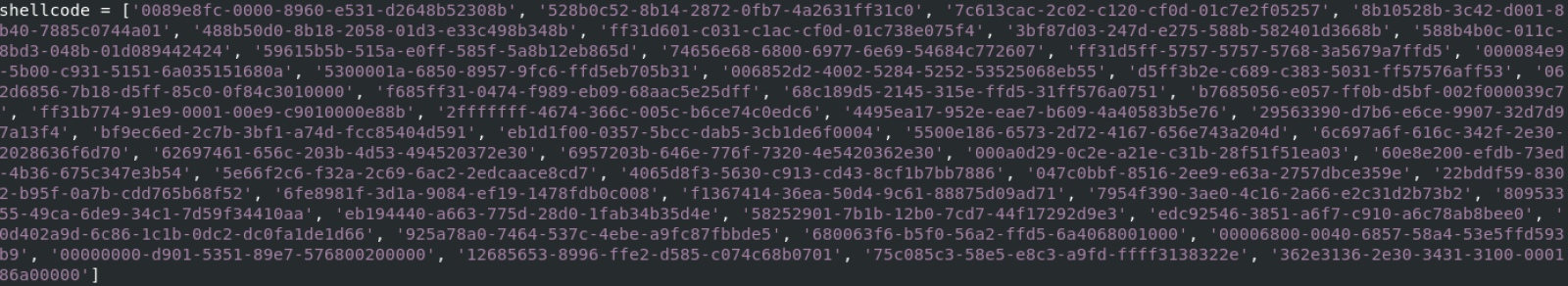
Shellcode Encoded in UUIDs, (Mon, Mar 10th)
I returned from another FOR610[1] class last week in London. One key tip I give to my students is to keep an eye on “strange” API calls. In the Windows ecosystem, Microsoft offers tons of API calls to developers. The fact that an API is used in a program does not always mean we are…
-
ISC Stormcast For Monday, March 10th, 2025 https://isc.sans.edu/podcastdetail/9356, (Mon, Mar 10th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
Commonly Probed Webshell URLs, (Sun, Mar 9th)
Looking over some weblogs on my way back from class in Baltimore, I feel a reminder is appropriate that (a) weblogs are still a thing and (b) what some of the common webshells are that attackers are looking for. Attackers often deploy web shells via file upload or remote code execution vulnerabilities. Standard webshells are…

