-
ISC Stormcast For Friday, March 7th, 2025 https://isc.sans.edu/podcastdetail/9354, (Fri, Mar 7th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
ISC Stormcast For Thursday, March 6th, 2025 https://isc.sans.edu/podcastdetail/9352, (Thu, Mar 6th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
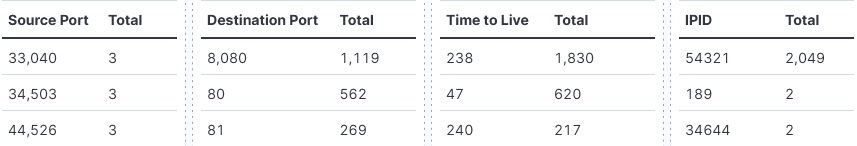
DShield Traffic Analysis using ELK, (Thu, Mar 6th)
Using the Kibana interface, sometimes it can be difficult to find traffic of interest since there can be so much of it. The 3 logs used for traffic analysis are cowrie, webhoneypot and the firewall logs. Other options to add to the honeypot are packet capture, netflow and Zeek. Using the following steps, I was…
-
ISC Stormcast For Wednesday, March 5th, 2025 https://isc.sans.edu/podcastdetail/9350, (Wed, Mar 5th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
Romanian Distillery Scanning for SMTP Credentials, (Tue, Mar 4th)
Lately, attackers have gotten more creative and aggressive in trying to find various credential files on exposed web servers. Our “First Seen” page each day shows many new versions of scans for secrets files like “.env”. Yesterday, I noted a couple of requests that stuck out a bit: /admin/smtp_keys.json /admin/smtp_tokens.json The same attacker scanned for…
-
Tool update: mac-robber.py, (Tue, Mar 4th)
Just a quick update. I fixed a big bug in my mac-robber.py script about 2 weeks ago, but realized I hadn’t published a diary about it. I didn’t go back and figure out how this one slipped in because I’m sure it worked originally, but it was generating bad output for soft/symbolic links. If. you are…
-
ISC Stormcast For Tuesday, March 4th, 2025 https://isc.sans.edu/podcastdetail/9348, (Tue, Mar 4th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
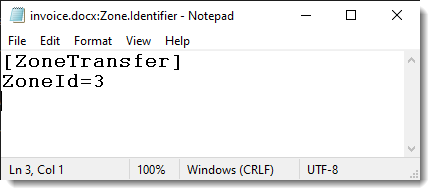
Mark of the Web: Some Technical Details, (Mon, Mar 3rd)
The Mark of the Web (MoTW) is file metadata in Windows that marks a file that was obtained from an untrusted source. When a file is downloaded from the Internet, browsers will not only write the file to disk, but also include metadata with the origin of the file. This also applies when an email…
-
ISC Stormcast For Monday, March 3rd, 2025 https://isc.sans.edu/podcastdetail/9346, (Mon, Mar 3rd)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
Wireshark 4.4.5 Released, (Sun, Mar 2nd)
Wireshark release 4.4.5 was released soon after 4.4.4 : it fixes a bug that makes Wireshark crash when clicking on a column title/header. Didier Stevens Senior handler blog.DidierStevens.com (c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.

