-
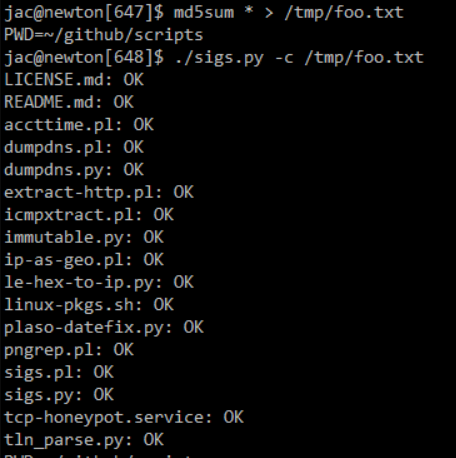
Tool update: sigs.py – added check mode, (Fri, Feb 21st)
Over the years, I’ve written a number of scripts to make my life easier. One of those tools was sigs.py (which was a rewrite of an old perl script sigs.pl) to hash files. I wanted something portable that could potentially be a drop-in replacement for things like md5sum, sha1sum, etc. (and can do hashes like…
-
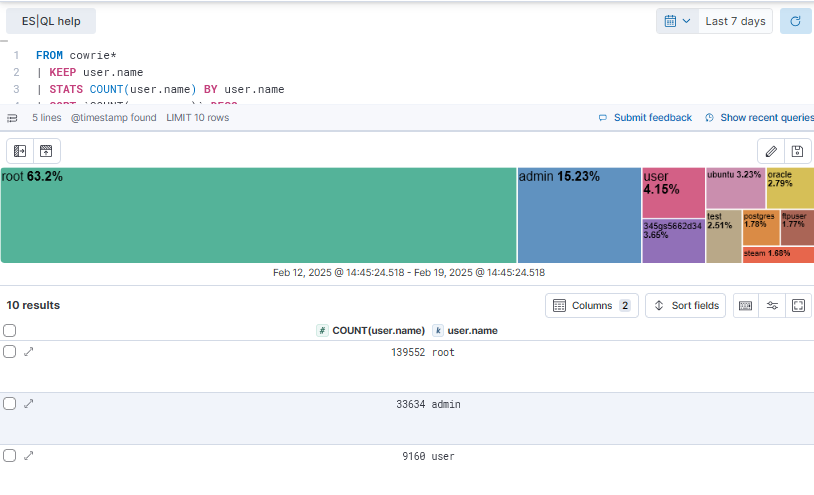
Using ES|QL in Kibana to Queries DShield Honeypot Logs, (Thu, Feb 20th)
With the Elastic released of version 8.17.0, it included “The technical preview of new MATCH and query string (QSTR) functions in ES|QL makes log searches easier and more intuitive.”[1] With this released, I started exploring some of the many options available with ES|QL in Kibana [2], enabled by default, to do various types of queries…
-
ISC Stormcast For Thursday, February 20th, 2025 https://isc.sans.edu/podcastdetail/9332, (Thu, Feb 20th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
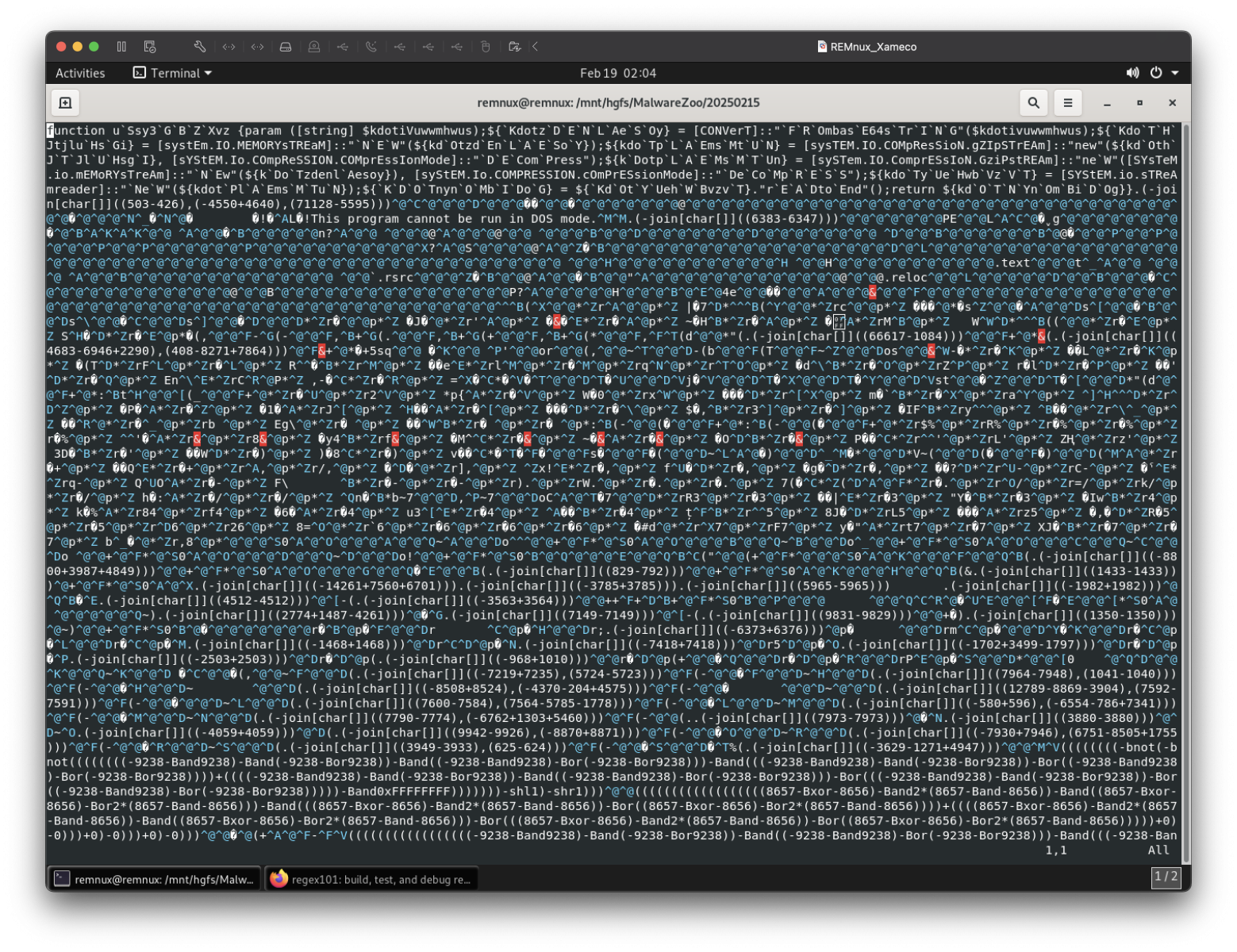
XWorm Cocktail: A Mix of PE data with PowerShell Code, (Wed, Feb 19th)
While hunting, I spent some time trying to deobfuscate a malicious file discovered on VT. It triggered my PowerShell rule. At the end, I found two files that look close together: 7c2f2a9a6078d37ee241e43f392f825630016c8ca8416bfd12cd27501b6876d1 (Score: 3/61)[1] d0b448d4de707a9fb611166278065afa2c52029234f7876158c8dd4798f08f9f (Score: 1/62)[2] They are identified as “data files,” and their upload names are, respectively, “XClient.exe” and “XingCode Unblocker 2025.exe”. XignCode…
-
ISC Stormcast For Wednesday, February 19th, 2025 https://isc.sans.edu/podcastdetail/9330, (Wed, Feb 19th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
SecTemplates.com – simplified, free open-source templates to enable engineering and smaller security teams to bootstrap security capabilities for their organizations, (Tue, Feb 18th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
ISC Stormcast For Tuesday, February 18th, 2025 https://isc.sans.edu/podcastdetail/9328, (Tue, Feb 18th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
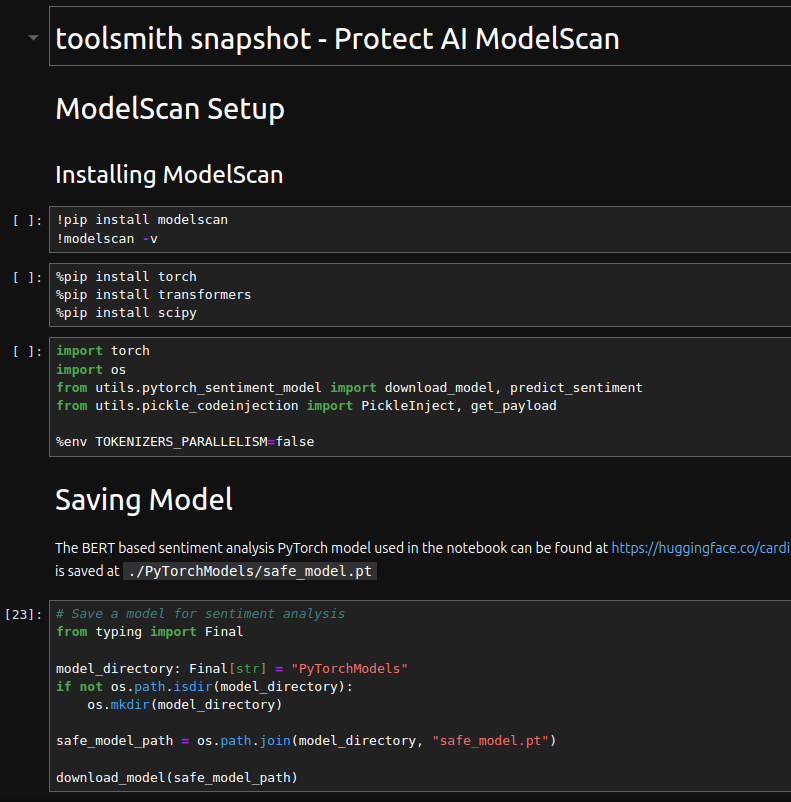
ModelScan – Protection Against Model Serialization Attacks, (Mon, Feb 17th)
Protect AI’s OSS portfolio includes tools aimed at improving security of AI/ML software. These tools are meant for a wide range of engineering, security and ML practitioners including developers, security engineers/researchers, ML engineers, LLM engineers and prompt engineers, and data scientists. Of particular interest in light of model serialization attacks is ModelScan. Headlines as recent as 6 FEB 2025 remind…
-
My Very Personal Guidance and Strategies to Protect Network Edge Devices, (Thu, Feb 6th)
Last week, CISA and other national cyber security organizations published an extensive document outlining “Guidance and Strategies to Protect Network Edge Devices.” [1] The document is good but also very corporate and “bland.” It summarizes good, well-intended advice that will help you secure edge devices. But reading it also made me think, “That’s it?” Not that…
-
ISC Stormcast For Monday, February 17th, 2025 https://isc.sans.edu/podcastdetail/9326, (Mon, Feb 17th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.

