-
ISC Stormcast For Monday, January 20th, 2025 https://isc.sans.edu/podcastdetail/9286, (Mon, Jan 20th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
Zero Trust and Entra ID Conditional Access, (Sun, Jan 19th)
Microsoft Entra ID (Formerly Azure AD) Conditional Access (CA) policies are the key components to a Zero Trust strategy, as it provides the ability to function as the front door for users and devices. CA policies use attributes, or signals, of various components as variables to be used to enforce specific access controls. Attributes include…
-

New tool: immutable.py, (Sat, Jan 18th)
When performing triage on a Linux system you suspect might be compromised, there are many aspects of the system that you may want to look at. In SANS FOR577, we talk about some existing tools and even writing your own bash script to collect triage data. In a case I worked a year or so…
-
![Leveraging Honeypot Data for Offensive Security Operations [Guest Diary], (Fri, Jan 17th)](/wp-content/uploads/2025/01/Alex_Sanders_pic1-YPqzan.png)
Leveraging Honeypot Data for Offensive Security Operations [Guest Diary], (Fri, Jan 17th)
[This is a Guest Diary by Alex Sanders, an ISC intern as part of the SANS.edu BACS program] Introduction As an offensive security professional, it is often part of my job to stand up infrastructure that is intentionally malicious and must be exposed to the internet. Examples of this could include Evilginx, Cobalt Strike, or…
-
ISC Stormcast For Friday, January 17th, 2025 https://isc.sans.edu/podcastdetail/9284, (Fri, Jan 17th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
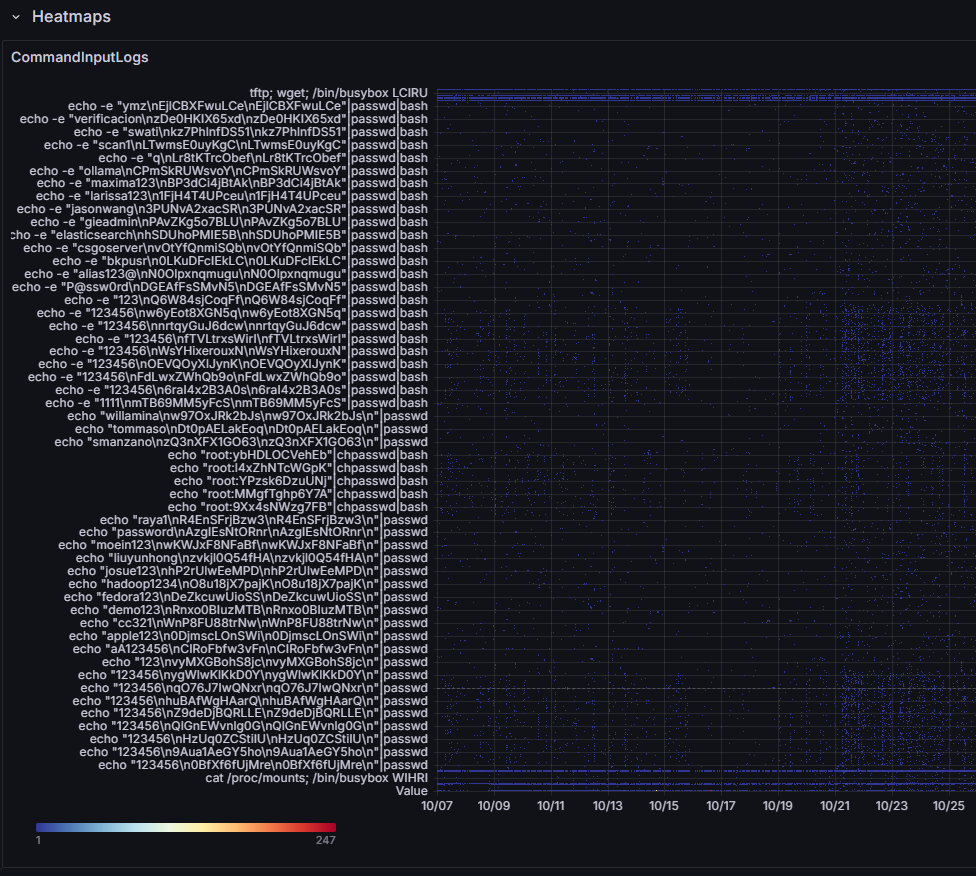
Extracting Practical Observations from Impractical Datasets, (Thu, Jan 16th)
[This is a Guest Diary by Curtis Dibble, an ISC intern as part of the SANS.edu BACS [1] program] Figure 1: A heatmap showing the date and frequency a given set of commands input to the honeypot Spoiler alert, sugar costs money, and syntactic sugar is the most expensive type. Fortunately, we live in an era…
-
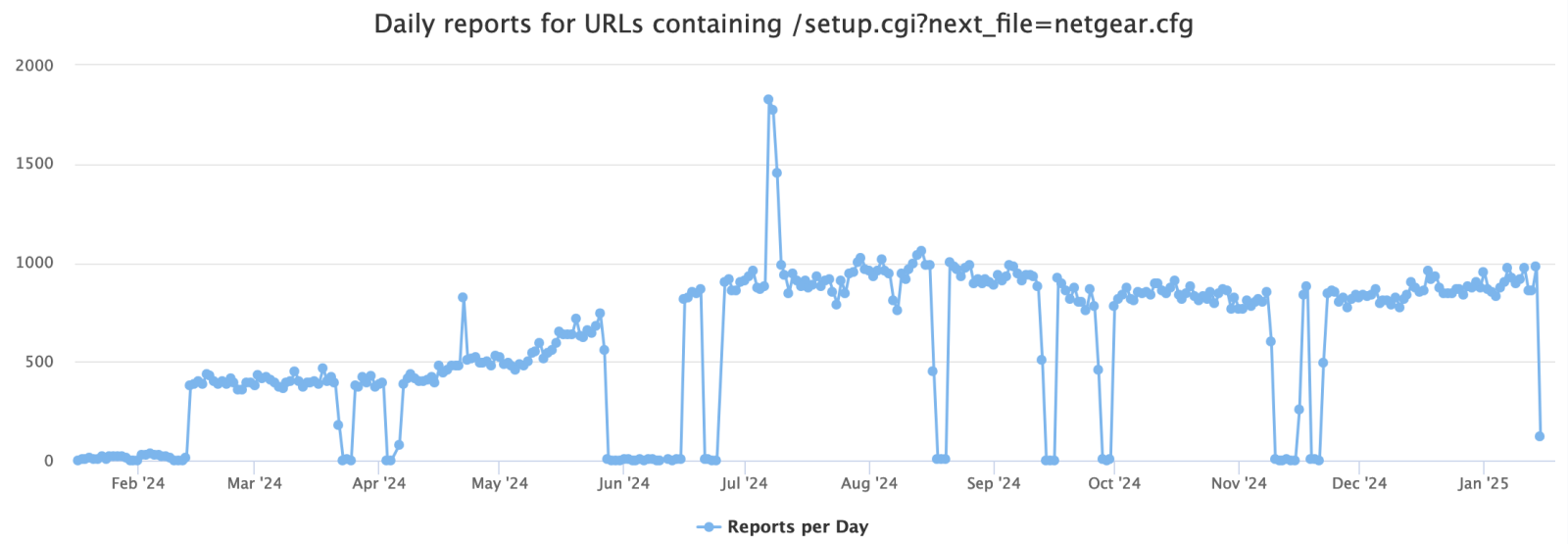
The Curious Case of a 12-Year-Old Netgear Router Vulnerability, (Wed, Jan 15th)
-
Microsoft January 2025 Patch Tuesday, (Tue, Jan 14th)
This month’s Microsoft patch update addresses a total of 209 vulnerabilities, including 12 classified as critical. Among these, 3 vulnerabilities have been actively exploited in the wild, and 5 have been disclosed prior to the patch release, marking them as zero-days. The updates span various components, with significant attention required for vulnerabilities that could lead to…
-
ISC Stormcast For Tuesday, January 14th, 2025 https://isc.sans.edu/podcastdetail/9278, (Mon, Jan 13th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
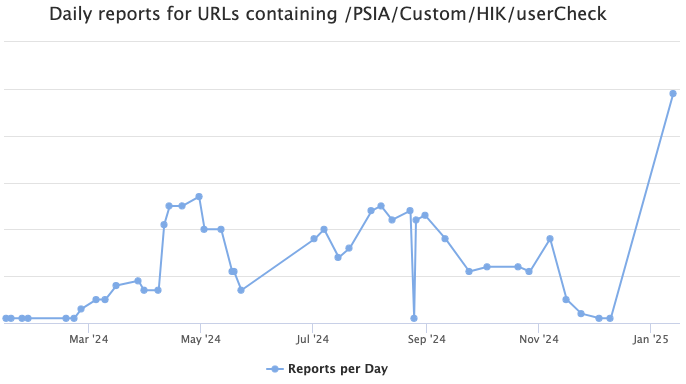
Hikvision Password Reset Brute Forcing, (Mon, Jan 13th)
One common pattern in password resets is sending a one-time password to the user to enable them to reset their password. The flow usually looks like: User Requests a password reset The user enters an e-mail address or phone number that is already registered with the application The application may ask for a password reset…

