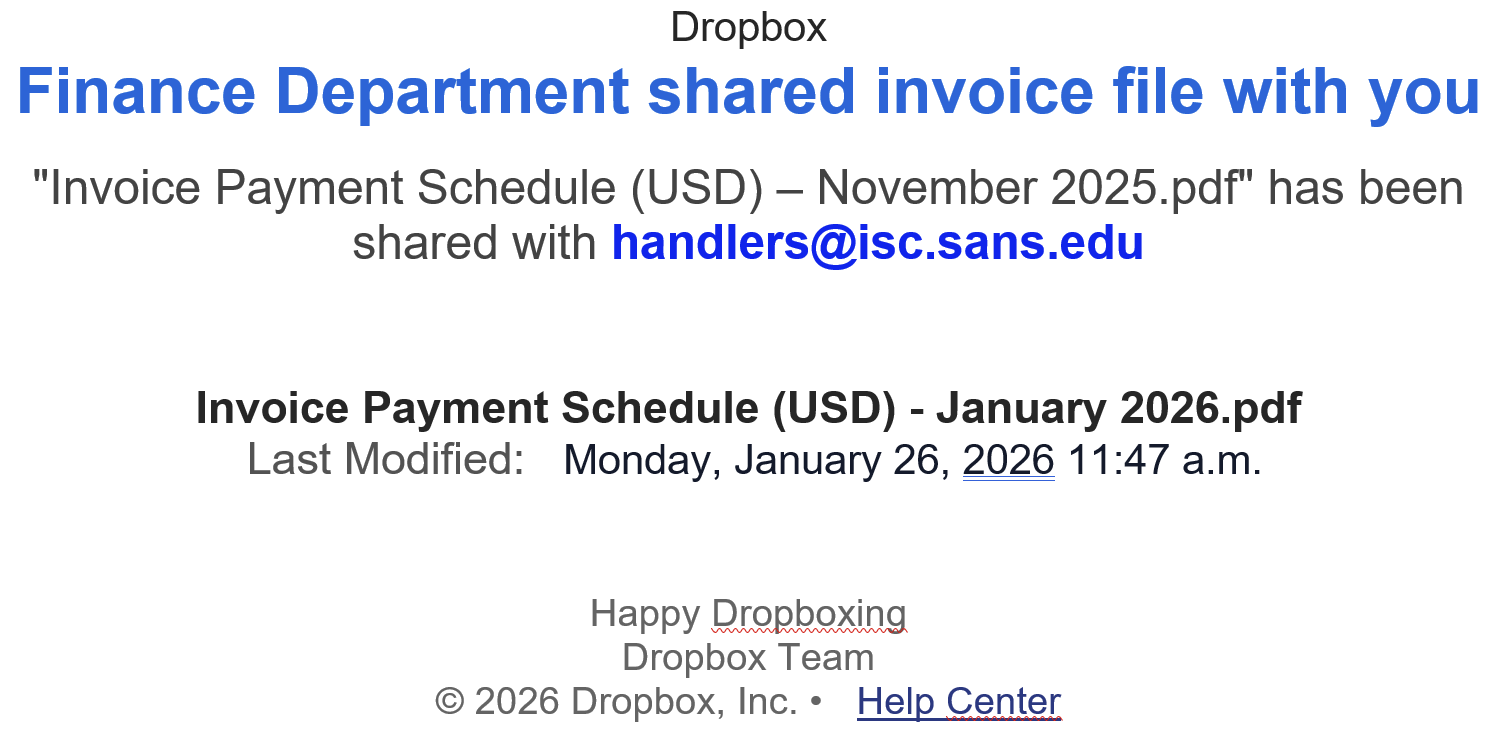
For a few days, many phishing emails that landed into my mailbox contain strange URLs. They are classic emails asking you to open a document, verify your pending emails, …
But the format of the URLs is broken! In a URL, parameters are extra pieces of information added after a question mark (?) to tell a website more details about a request; they are written as name=value pairs (for example “email=user@domain”), and multiple parameters are separated by an ampersand (&).
Here are some examples of detected URLs:
hxxps://cooha0720[.]7407cyan[.]workers[.]dev/?dC=handlers@isc[.]sans[.]edu&*(Df hxxps://calcec7[.]61minimal[.]workers[.]dev/?wia=handlers@isc[.]sans[.]edu&*(chgd hxxps://couraol-02717[.]netlify[.]app/?dP=handlers@isc[.]sans[.]edu&*(TemP hxxps://shiny-lab-a6ef[.]tcvtxt[.]workers.dev/?kpv=handlers@isc[.]sans[.]edu&*(lIi
You can see that the parameters are broken… “&*(Df” is invalid! It’s not an issue for browsers that will just ignore these malformed parameters, so the malicious website will be visited.
I did not see this for a while but it seems that the technique is back on stage. Threat actors implement this to break security controls. Many of them assume a “key=value” format. It may also break regex-based detectionn, URL normalization routines or IOC extraction pipelines…
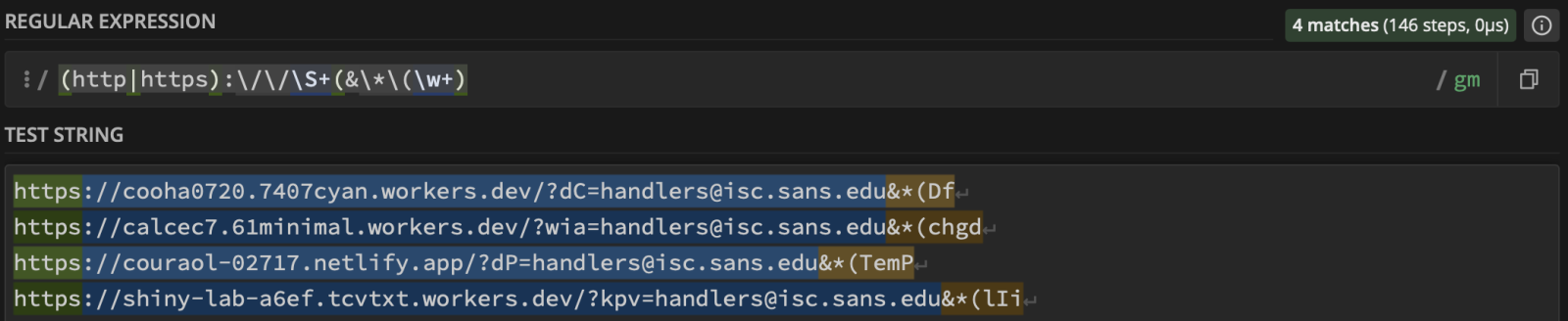
Of course, we can track such URLs using a regex to extract the last param:
Xavier Mertens (@xme)
Xameco
Senior ISC Handler – Freelance Cyber Security Consultant
PGP Key
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.