-
Exploring Statistical Measures to Predict URLs as Legitimate or Intrusive [Guest Diary], (Wed, Apr 2nd)
[This is a Guest Diary by Gregory Weber, an ISC intern as part of the SANS.edu BACS program] For the last 5 months, as part of my BACS internship with SANS, I have monitored two deployments of a DShield Sensor, sometimes referred to as a honeypot. The DShield sensor offers multiple attack surfaces including Telnet…
-
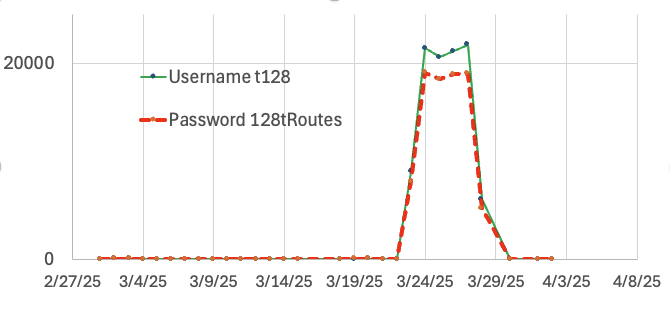
Surge in Scans for Juniper “t128” Default User, (Wed, Apr 2nd)
Last week, I noticed a surge in scans for the username “t128”. This username, accompanied by the password “128tRoutes,” is a well-known default account for Juniper’s Session Smart Networking Platform (or “SSR” for “Session Smart Routing”). The username and password are a bit “odd”. Juniper acquired a company called “128 Technologies” a few years ago,…
-
ISC Stormcast For Wednesday, April 2nd, 2025 https://isc.sans.edu/podcastdetail/9390, (Wed, Apr 2nd)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
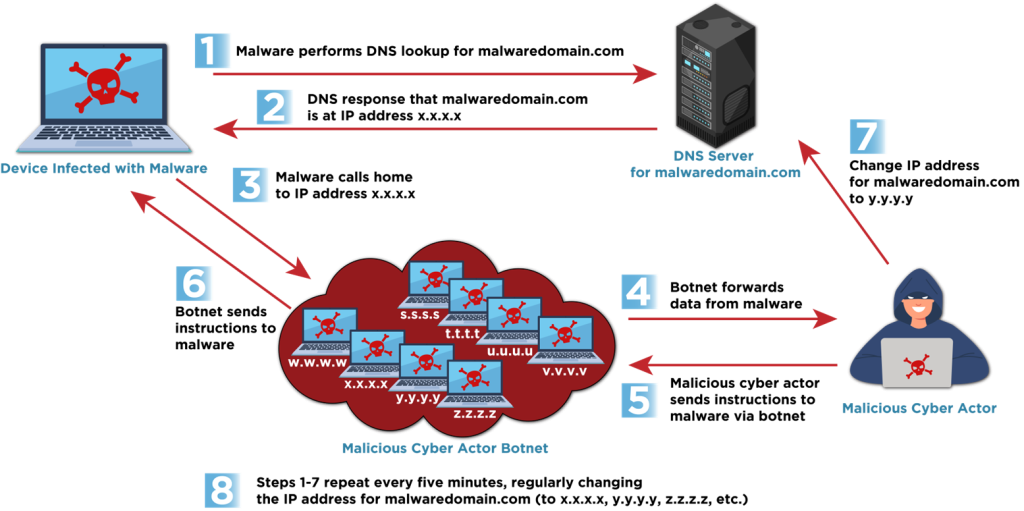
Fast Flux: A National Security Threat
Executive summary Many networks have a gap in their defenses for detecting and blocking a malicious technique known as “fast flux.” This technique poses a significant threat to national security, enabling malicious cyber actors to consistently evade detection. Malicious cyber actors, including cybercriminals and nation-state actors, use fast flux to obfuscate the locations of malicious…
-
ISC Stormcast For Tuesday, April 1st, 2025 https://isc.sans.edu/podcastdetail/9388, (Tue, Apr 1st)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
Apple Patches Everything: March 31st 2025 Edition, (Mon, Mar 31st)
Today, Apple released updates across all its products: iOS, iPadOS, macOS, tvOS, visionOS, Safari, and XCode. WatchOS was interestingly missing from the patch lineup. This is a feature update for the operating systems, but we get patches for 145 different vulnerabilities in addition to new features. This update includes a patch for CVE-2025-24200 and CVE-2025-24201, two already…
-
Apache Camel Exploit Attempt by Vulnerability Scan (CVE-2025-27636, CVE-2025-29891), (Mon, Mar 31st)
About three weeks ago, Apache patched two vulnerabilities in Apache Camel. The two vulnerabilities (CVE-2025-27636 and CVE-2025-29891) may lead to remote code execution, but not in the default configuration. The vulnerability is caused by Apache Camel using case-sensitive filters to restrict which headers may be used. However HTTP headers are not case-sensitive, and an attacker may…
-
ISC Stormcast For Monday, March 31st, 2025 https://isc.sans.edu/podcastdetail/9386, (Mon, Mar 31st)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
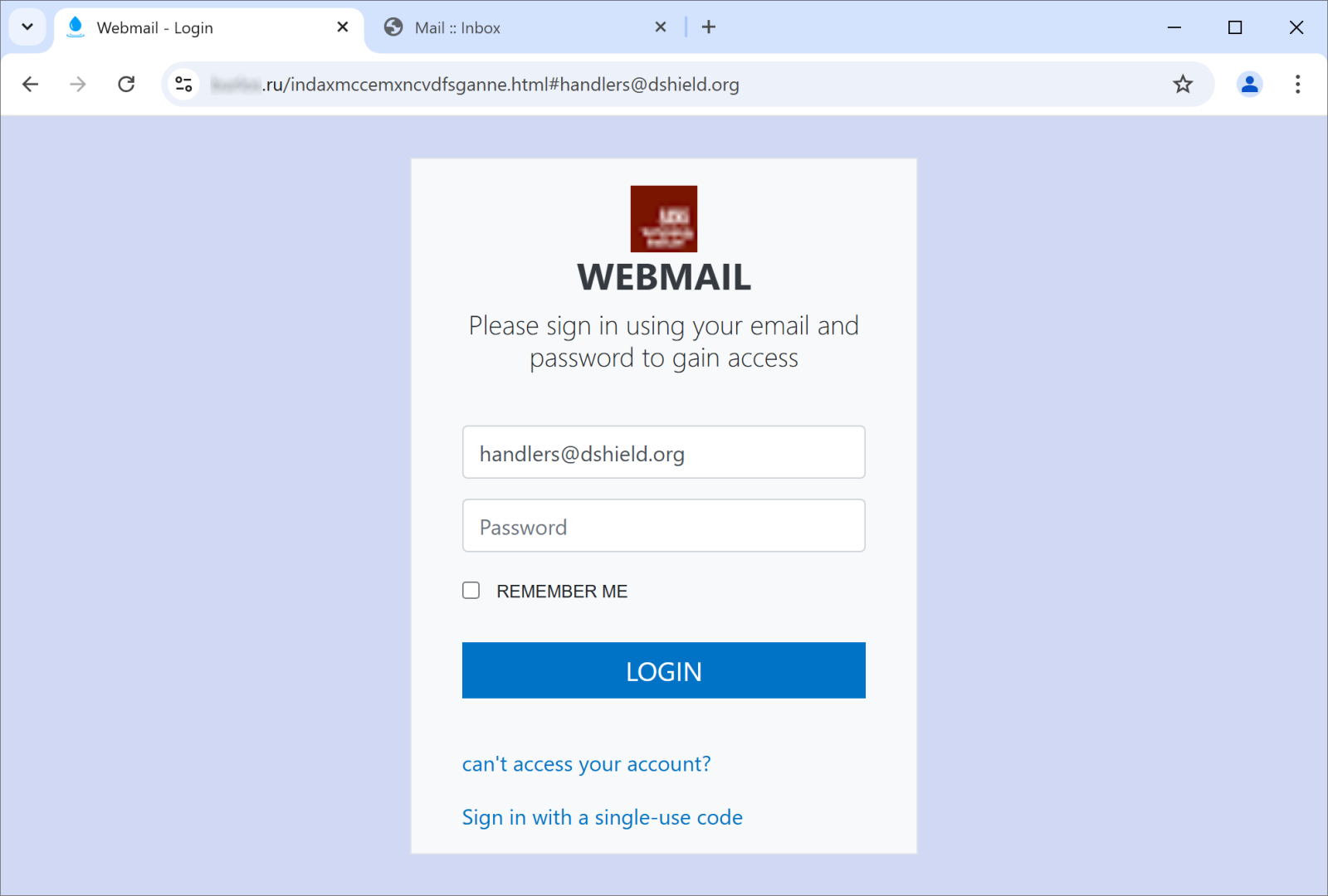
A Tale of Two Phishing Sites, (Fri, Mar 28th)
In phishing and in malspam, as in any other field, one can see certain trends develop over time. For obvious reasons, most threat actors like to use techniques and approaches that are novel and, thus, more effective. This commonly leads to adoption of the same techniques and technologies by multiple threat actors at the same…
-
ISC Stormcast For Friday, March 28th, 2025 https://isc.sans.edu/podcastdetail/9384, (Fri, Mar 28th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.

