-
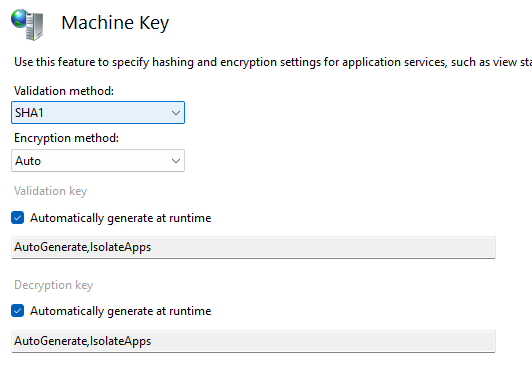
Stealing Machine Keys for fun and profit (or riding the SharePoint wave), (Tue, Aug 5th)
About 10 days ago exploits for Microsoft SharePoint (CVE-2025-53770, CVE-2025-53771) started being publicly abused – we wrote about that at here and here . The original SharePoint vulnerability is a deserialization vulnerability that allowed an attacker to execute arbitrary commands – while these could be literally anything, majority of exploits that we analyzed resulted in…
-
ISC Stormcast For Tuesday, August 5th, 2025 https://isc.sans.edu/podcastdetail/9556, (Tue, Aug 5th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
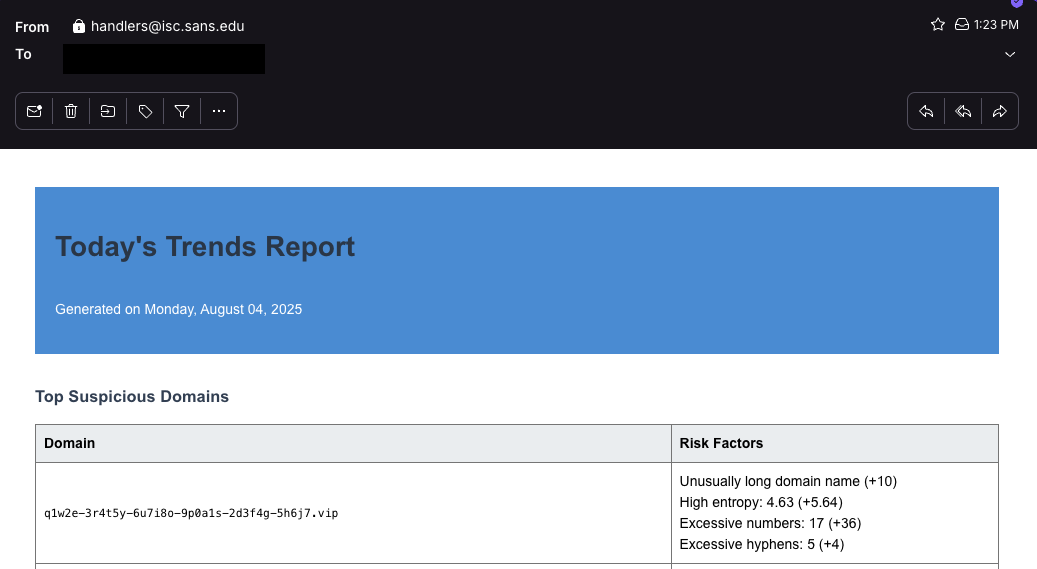
New Feature: Daily Trends Report, (Mon, Aug 4th)
I implemented a new report today, the “Daily Trends” report. It summarizes noteworthy data received from our honeypot. As with everything, it will improve if you provide feedback 🙂 There are two ways to receive the report: E-Mail: Sign up at https://isc.sans.edu/notify.html JSON/HTTP: You may also just download the raw JSON data for the report…
-
ISC Stormcast For Monday, August 4th, 2025 https://isc.sans.edu/podcastdetail/9554, (Mon, Aug 4th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
Legacy May Kill, (Sun, Aug 3rd)
Just saw something that I thought was long gone. The username “pop3user” is showing up in our telnet/ssh logs. I don’t know how long ago it was that I used POP3 to retrieve e-mail from one of my mail servers. IMAP and various webmail systems have long since replaced this classic email protocol. But at…
-
ISC Stormcast For Friday, August 1st, 2025 https://isc.sans.edu/podcastdetail/9552, (Fri, Aug 1st)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-

Scattered Spider Related Domain Names, (Thu, Jul 31st)
This week, CISA updated its advisory on Scattered Spider. Scattered Spider is a threat actor using social engineering tricks to access target networks. The techniques used by Scattered Spider replicate those used by other successful actors, such as Lapsus$. Social engineering does not require a lot of technical tools; creativity is key, and defenses have…
-
ISC Stormcast For Thursday, July 31st, 2025 https://isc.sans.edu/podcastdetail/9550, (Thu, Jul 31st)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
Securing Firebase: Lessons Re-Learned from the Tea Breach, (Wed, Jul 30th)
Today we are trying something a bit different (again). Brandon Evans, senior instructor with SANS, contributed the video below, talking a bit about the breach of the Tea App, and how to prevent and detect this vulnerability. Firebase is a very popular database developed by Google. It easily ties in with modern web and mobile…
-
ISC Stormcast For Wednesday, July 30th, 2025 https://isc.sans.edu/podcastdetail/9548, (Wed, Jul 30th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.

