-
Apple Updates Everything: July 2025, (Tue, Jul 29th)
Apple today released updates for iOS, iPadOS, macOS, watchOS, tvOS, and visionOS. This is a feature release, but it includes significant security updates. Apple patches a total of 29 different vulnerabilities. None of these vulnerabilities has been identified as exploited. Apple’s vulnerability descriptions are not very telling. Most vulnerabilities are likely DoS issues, causing a…
-
Triage is Key! Python to the Rescue!, (Tue, Jul 29th)
When you need to quickly analyze a lot of data, there is one critical step to perform: Triage. In forensic investigations, this step is critical because it allows investigators to quickly identify, prioritize, and isolate the most relevant or high value evidence from large volumes of data, ensuring that limited time and resources are focused…
-
ISC Stormcast For Tuesday, July 29th, 2025 https://isc.sans.edu/podcastdetail/9546, (Tue, Jul 29th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
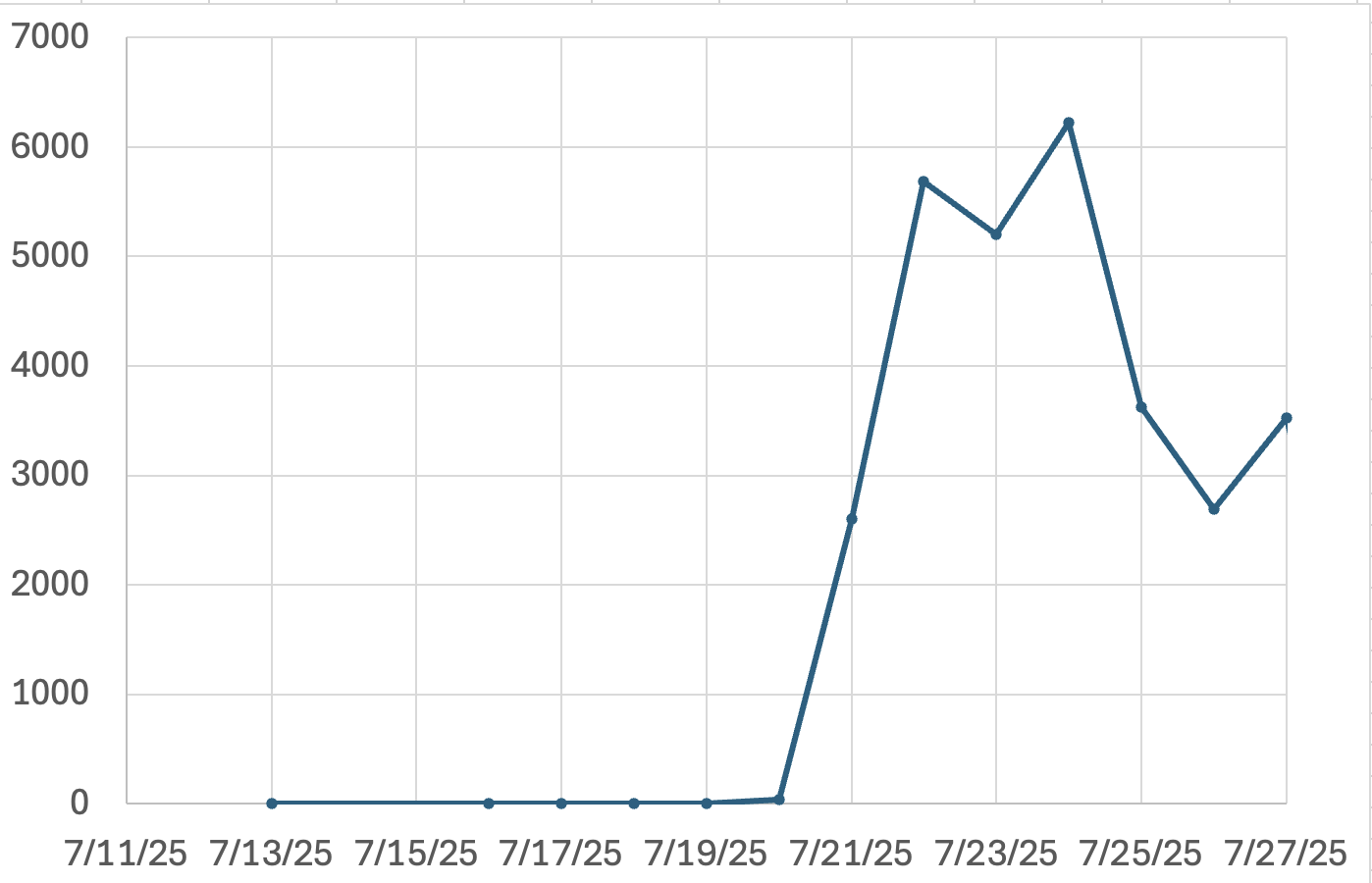
Parasitic Sharepoint Exploits, (Mon, Jul 28th)
Last week, newly exploited SharePoint vulnerabilities took a lot of our attention. It is fair to assume that last Monday (July 21st), all exposed vulnerable SharePoint installs were exploited. Of course, there is nothing to prevent multiple exploitation of the same instance, and a lot of that certainly happened. But why exploit it yourself if…
-
ISC Stormcast For Monday, July 28th, 2025 https://isc.sans.edu/podcastdetail/9544, (Mon, Jul 28th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
Sinkholing Suspicious Scripts or Executables on Linux, (Fri, Jul 25th)
When you need to analyze some suspicious pieces of code, it’s interesting to detonate them in a sandbox. If you don’t have a complete sandbox environment available or you just want to avoid generatin noise on your network, why not route the traffic to a sinkhole or NULL-route (read: packets won’t be sent across the normal…
-
ISC Stormcast For Friday, July 25th, 2025 https://isc.sans.edu/podcastdetail/9542, (Fri, Jul 25th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
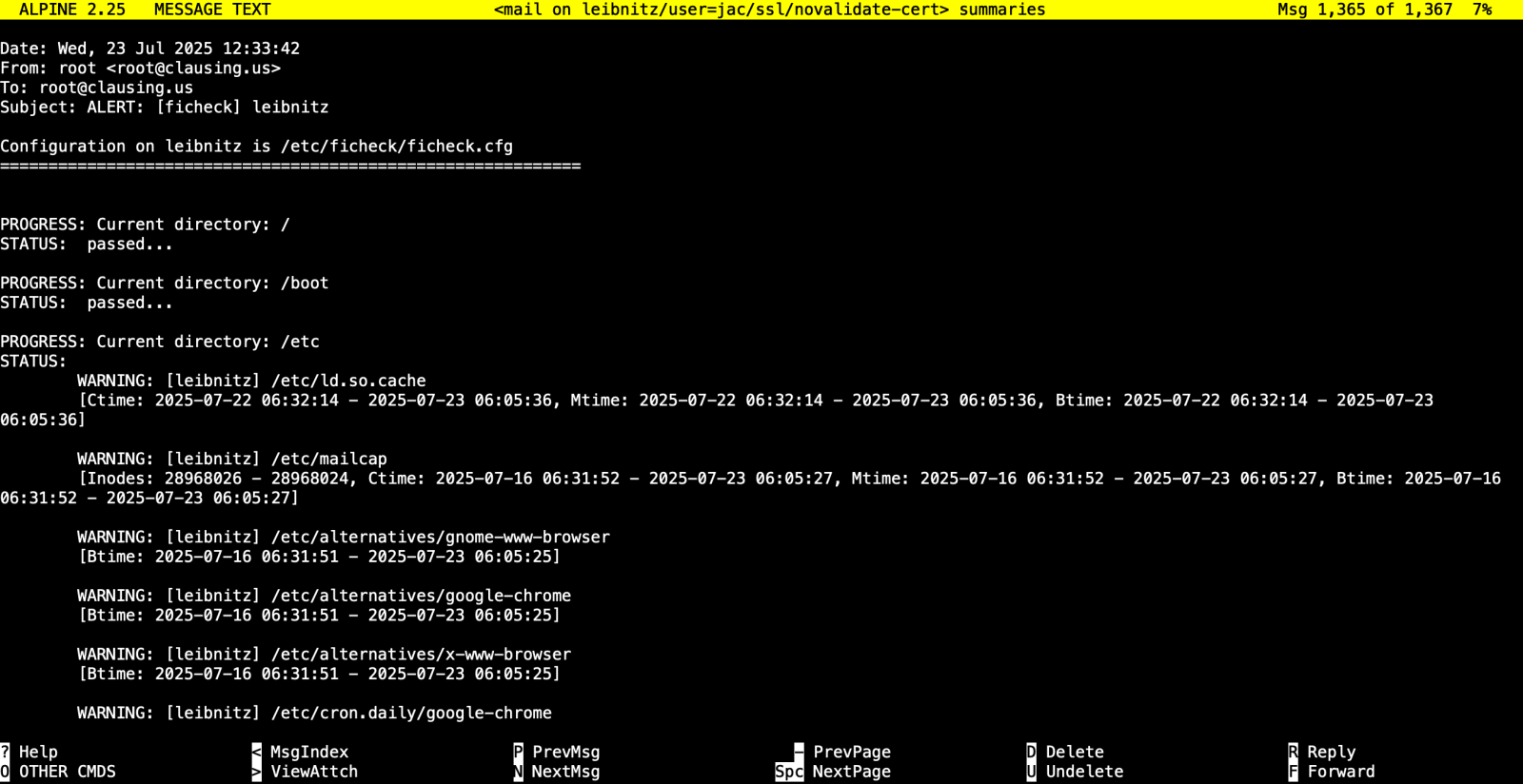
New Tool: ficheck.py, (Thu, Jul 24th)
As I mention every time I teach FOR577, I have been a big fan of file integrity monitoring tools (FIM) since Gene Kim first released Tripwire well over 30 years ago. I’ve used quite a few of them over the years including tripwire, OSSEC, samhain, and aide, just to name a few. For many years,…
-
ISC Stormcast For Thursday, July 24th, 2025 https://isc.sans.edu/podcastdetail/9540, (Thu, Jul 24th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
Analyzing Sharepoint Exploits (CVE-2025-53770, CVE-2025-53771), (Wed, Jul 23rd)
A few days after the exploit originally became widely known, there are now many different SharePoint exploit attempts in circulation. We do see some scans by researchers to identify vulnerable systems (or to scan for common artifacts of compromise), and a few variations of the “ToolPane.aspx” URL being hit. Even for our “random” honeypots, the…

