-
Open Redirects: A Forgotten Vulnerability?, (Tue, Feb 24th)
In 2010, OWASP added “Unvalidated Redirects and Forwards” to its Top 10 list and merged it into “Sensitive Data Exposure” in 2013 [owasp1] [owasp2]. Open redirects are often overlooked, and their impact is not always well understood. At first, it does not look like a big deal. The user is receiving a 3xx status code and…
-
ISC Stormcast For Tuesday, February 24th, 2026 https://isc.sans.edu/podcastdetail/9822, (Tue, Feb 24th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
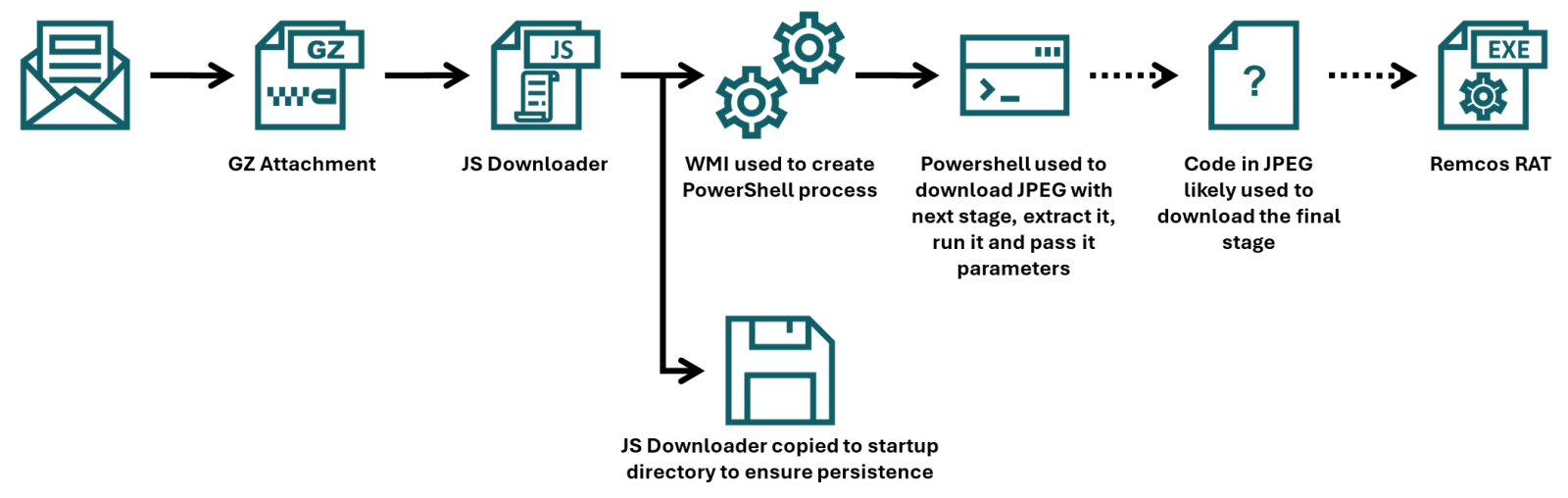
Another day, another malicious JPEG, (Mon, Feb 23rd)
In his last two diaries, Xavier discussed recent malware campaigns that download JPEG files with embedded malicious payload[1,2]. At that point in time, I’ve not come across the malicious “MSI image” myself, but while I was going over malware samples that were caught by one of my customer’s e-mail proxies during last week, I found…
-
ISC Stormcast For Monday, February 23rd, 2026 https://isc.sans.edu/podcastdetail/9820, (Mon, Feb 23rd)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
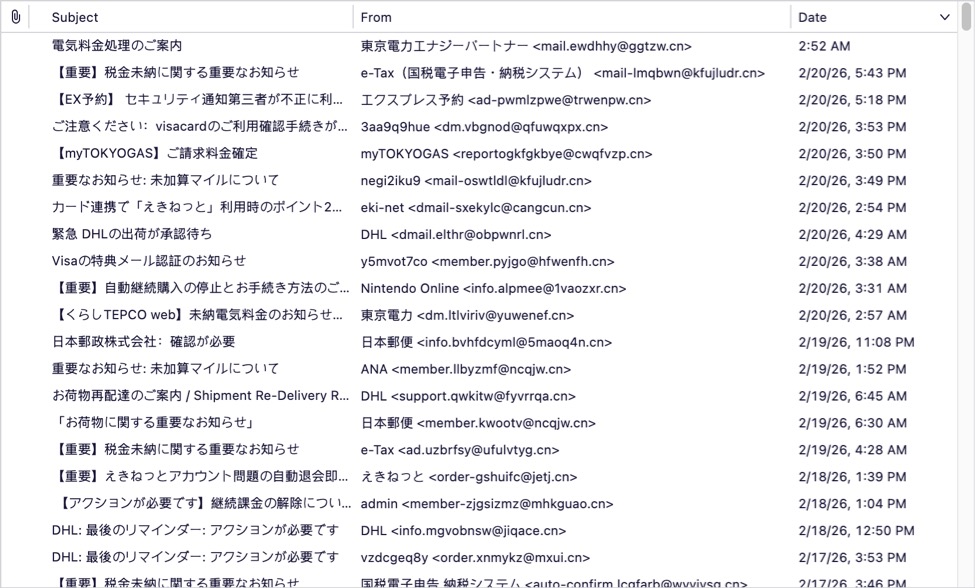
Japanese-Language Phishing Emails, (Sat, Feb 21st)
Introduction For at least the past year or so, I’ve been receiving Japanese-language phishing emails to my blog email addresses at @malware-traffic-analysis.net. I’m not Japanese, but I suppose my blog’s email addresses ended up on a list used by the group sending these emails. They’re all easily caught by my spam filters, so they’re not…
-
ISC Stormcast For Friday, February 20th, 2026 https://isc.sans.edu/podcastdetail/9818, (Fri, Feb 20th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
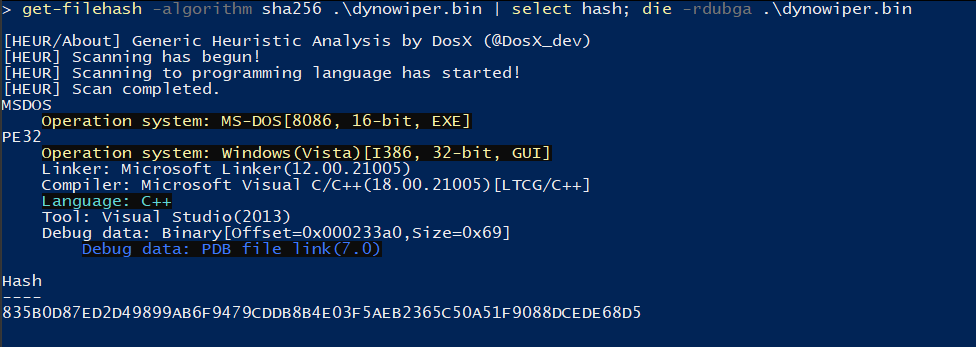
Under the Hood of DynoWiper, (Thu, Feb 19th)
[This is a Guest Diary contributed by John Moutos] Overview In this post, I’m going over my analysis of DynoWiper, a wiper family that was discovered during attacks against Polish energy companies in late December of 2025. ESET Research [1] and CERT Polska [2] have linked the activity and supporting malware to infrastructure and tradecraft…
-
ISC Stormcast For Thursday, February 19th, 2026 https://isc.sans.edu/podcastdetail/9816, (Thu, Feb 19th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
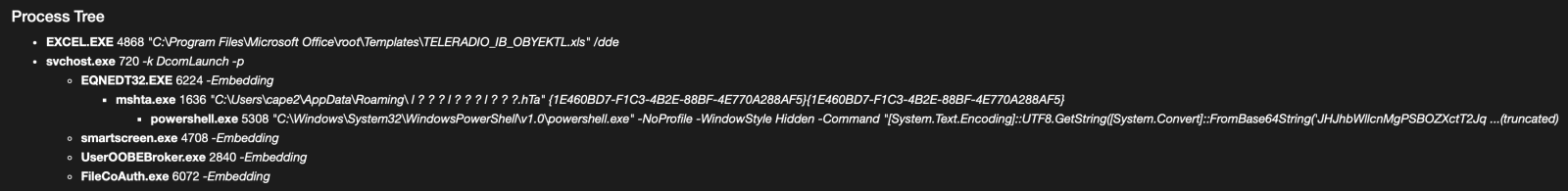
Tracking Malware Campaigns With Reused Material, (Wed, Feb 18th)
A few days ago I wrote a diary called “Malicious Script Delivering More Maliciousness”[1]. In the malware infection chain, there was a JPEG picture that embedded the last payload delimited with “BaseStart-” and “-BaseEnd” tags. Today, I discovered anoher campaign that relies exactly on the same technique. It started with an attachment called “TELERADIO_IB_OBYEKTLRIN_BURAXILIS_FORMASI.xIs” (SHA256:1bf3ec53ddd7399cdc1faf1f0796c5228adc438b6b7fa2513399cdc0cb865962).…
-
ISC Stormcast For Wednesday, February 18th, 2026 https://isc.sans.edu/podcastdetail/9814, (Wed, Feb 18th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.

