-
ISC Stormcast For Thursday, July 17th, 2025 https://isc.sans.edu/podcastdetail/9530, (Thu, Jul 17th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
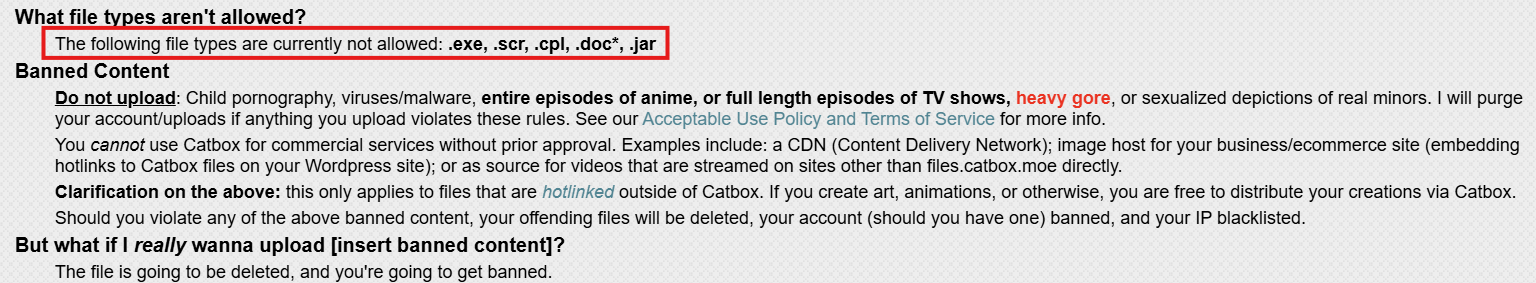
More Free File Sharing Services Abuse, (Wed, Jul 16th)
A few months ago, I wrote a diary about online services used to exfiltrate data[1]. In this diary, I mentioned some well-known services. One of them was catbox.moe[2]. Recently, I found a sample that was trying to download some payload from this website. I performed a quick research and collected more samples! I collected (and…
-
ISC Stormcast For Wednesday, July 16th, 2025 https://isc.sans.edu/podcastdetail/9528, (Wed, Jul 16th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
Keylogger Data Stored in an ADS, (Tue, Jul 15th)
If many malware samples try to be “filess” (read: they try to reduce their filesystem footprint to the bare minimum), another technique remains interesting: Alternate Data Streams or “ADS”[1]. This NTFS feature allows files to contain multiple data streams, enabling hidden or additional metadata to be stored alongside the main file content without being visible in…
-
ISC Stormcast For Tuesday, July 15th, 2025 https://isc.sans.edu/podcastdetail/9526, (Tue, Jul 15th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
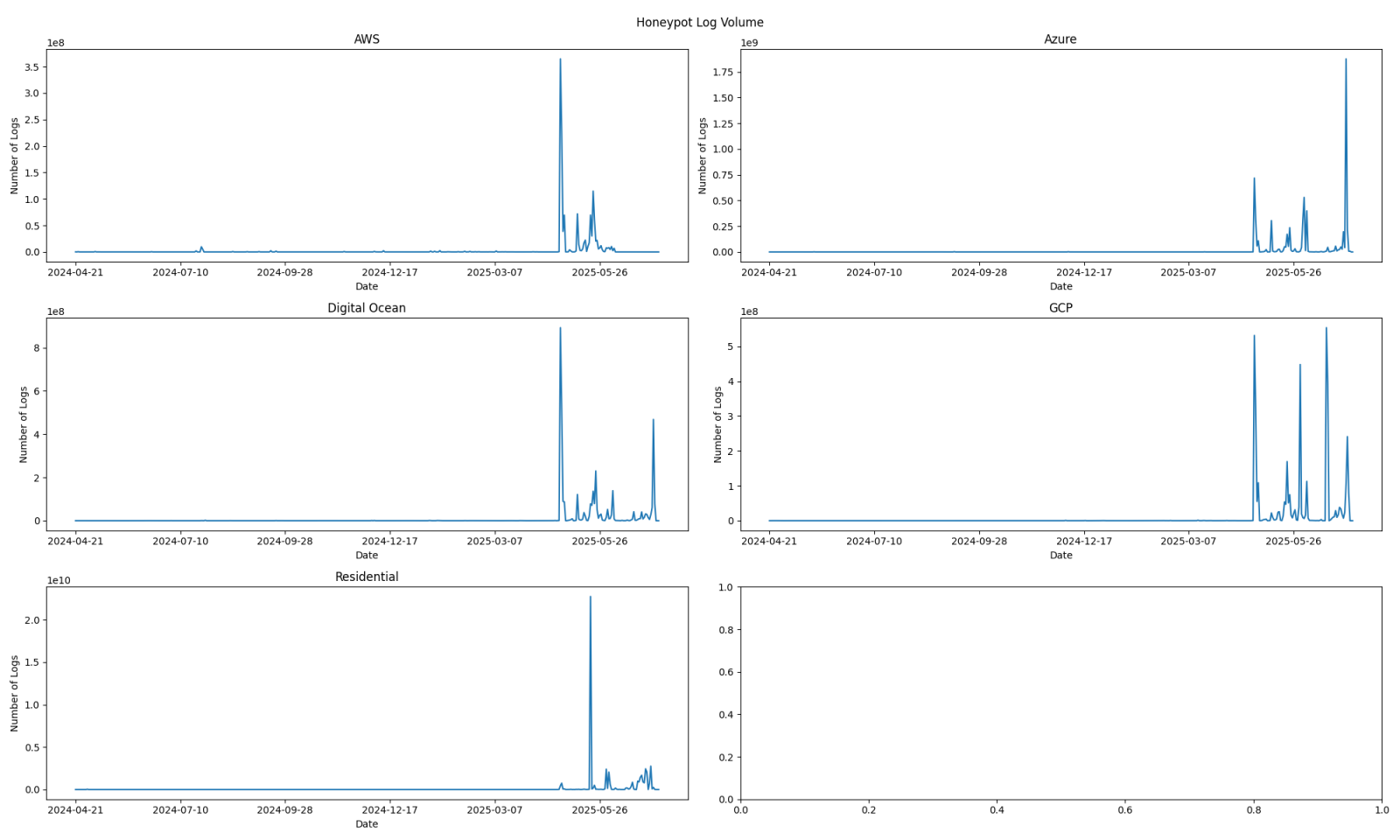
DShield Honeypot Log Volume Increase, (Mon, Jul 14th)
The volume of honeypot logs changes over time. Very rarely are honeypot logs quiet, meaning that there are no internet scans or malicious activity generating logs. Honeypots can see large increases in activity [1], but this has tended to be the exception, rather than the rule. Within the last few months, however, there has been…
-
ISC Stormcast For Monday, July 14th, 2025 https://isc.sans.edu/podcastdetail/9524, (Mon, Jul 14th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
Experimental Suspicious Domain Feed, (Sun, Jul 13th)
We have had a “newly registered domain” feed for a few years. This feed pulls data from ICANN’s centralized zone data service (https://czds.icann.org) and TLS certificate transparency logs. The ICANN CZDS is a good start, but it only offers data from top-level domains collaborating with ICANN. Missing are in particular country-level domains. Country-level zone files…
-
ISC Stormcast For Friday, July 11th, 2025 https://isc.sans.edu/podcastdetail/9522, (Fri, Jul 11th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
ISC Stormcast For Thursday, July 10th, 2025 https://isc.sans.edu/podcastdetail/9520, (Thu, Jul 10th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.

