-
How Long Until the Phishing Starts? About Two Weeks, (Tue, Jun 17th)
[This is a guest diary by Christopher Crowley, https://montance.com] Here’s a good reason to include security awareness training for new hires! I recently added an account to my Google Workspace domain (montance[dot]com). Friday, May 16th, 10:10 am, to be exact. Something interesting to note about the domain configuration is there’s a catchall account in place,…
-
ISC Stormcast For Tuesday, June 17th, 2025 https://isc.sans.edu/podcastdetail/9496, (Tue, Jun 17th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
A JPEG With A Payload, (Mon, Jun 16th)
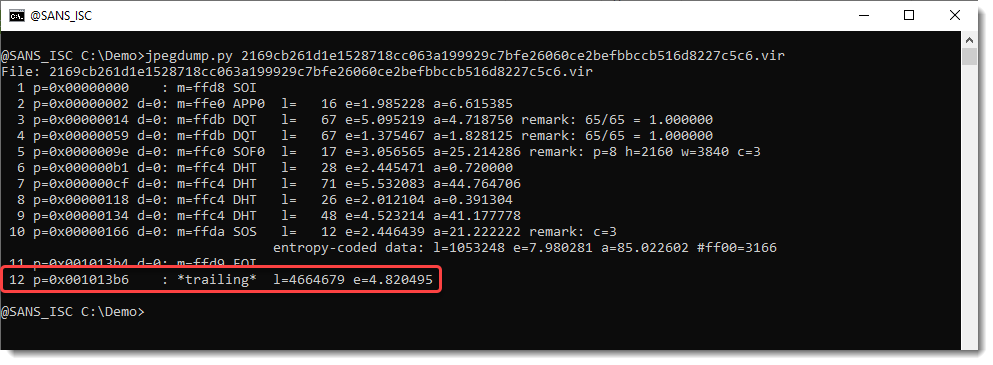
Over the weekend, Xavier posted about another image with a payload: “More Steganography!“. Xavier did a static analysis, and I want to explain how you can decode the payload if you opted for a dynamic analysis. During your dynamic analysis, you will notice the download of a JPEG image from hxxps://zynova[.]kesug[.]com/new_image.jpg. You can use my tool…
-
ISC Stormcast For Monday, June 16th, 2025 https://isc.sans.edu/podcastdetail/9494, (Mon, Jun 16th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-

More Steganography!, (Sat, Jun 14th)
I spotted another interesting file that uses, once again, steganography. It seems to be a trend (see one of my previous diaries[1]). The file is an malicious Excel sheet called blcopy.xls. Office documents are rare these days because Microsoft improved the rules to allow automatic macro execution[2]. But it does not mean that Office documents…
-
ISC Stormcast For Friday, June 13th, 2025 https://isc.sans.edu/podcastdetail/9492, (Fri, Jun 13th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
![[Guest Diary] Anatomy of a Linux SSH Honeypot Attack: Detailed Analysis of Captured Malware, (Fri, Jun 13th)](/wp-content/uploads/2025/06/2025-06-08_figure1-eUZlW5.png)
[Guest Diary] Anatomy of a Linux SSH Honeypot Attack: Detailed Analysis of Captured Malware, (Fri, Jun 13th)
[This is a Guest Diary by Michal Ambrozkiewicz, an ISC intern as part of the SANS.edu Bachelor’s Degree in Applied Cybersecurity (BACS) program [1].] On April 29, 2025, my Raspberry Pi-based Cowrie SSH honeypot captured a sophisticated attack campaign targeting Linux systems. This wasn’t just another automated scanner – the logs reveal a multi-stage attack…
-
![Automated Tools to Assist with DShield Honeypot Investigations [Guest Diary], (Wed, Jun 11th)](/wp-content/uploads/2025/06/William_Constantino_pic1-j2rlOD.png)
Automated Tools to Assist with DShield Honeypot Investigations [Guest Diary], (Wed, Jun 11th)
[This is a Guest Diary by William Constantino, an ISC intern as part of the SANS.edu BACS program] In the beginning of my Internet Storm Center (ISC) internship, I wasted too much time trying to build my SIEM from an old computer I had lying around, or a new Raspberry Pi I purchased. I keep…
-
ISC Stormcast For Thursday, June 12th, 2025 https://isc.sans.edu/podcastdetail/9490, (Thu, Jun 12th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-

Quasar RAT Delivered Through Bat Files, (Wed, Jun 11th)
RAT’s are popular malware. They are many of them in the wild, Quasar[1] being one of them. The malware has been active for a long time and new campaigns come regularly back on stage. I spotted an interesting .bat file (Windows script) that attracted my attention because it is very well obfuscated. This file is a…

