-
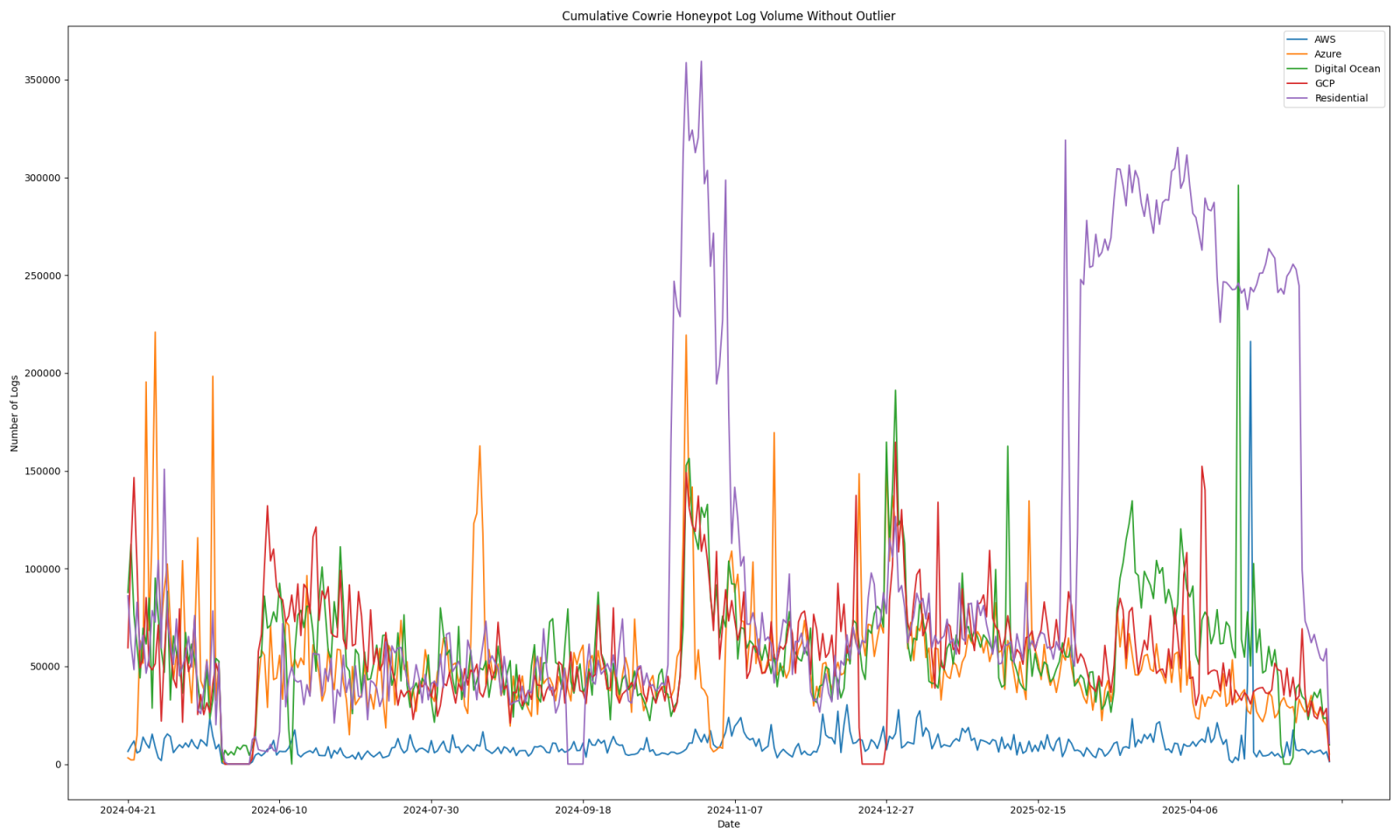
Usage of “passwd” Command in DShield Honeypots, (Fri, May 30th)
DShield honeypots [1] receive different types of attack traffic and the volume of that traffic can change over time. I’ve been collecting data from a half dozen honeypots for a little over a year to make comparisons. This data includes: Cowrie logs [2], which contain SSH and telnet attacks Web honeypot logs Firewall logs (iptables)…
-
ISC Stormcast For Thursday, May 29th, 2025 https://isc.sans.edu/podcastdetail/9470, (Thu, May 29th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
![Alternate Data Streams ? Adversary Defense Evasion and Detection [Guest Diary], (Wed, May 28th)](/wp-content/uploads/2025/05/Ehsaan_Mavani_Picture1-d3b6AK.png)
Alternate Data Streams ? Adversary Defense Evasion and Detection [Guest Diary], (Wed, May 28th)
[This is a Guest Diary by Ehsaan Mavani, an ISC intern as part of the SANS.edu BACS program] Introduction Adversaries are leveraging alternate data streams to hide malicious data with the intent of evading detection. Numerous different malicious software has been designed to read and write to alternate data streams [1]. To better assist in…
-
![[Guest Diary] Exploring a Use Case of Artificial Intelligence Assistance with Understanding an Attack, (Wed, May 28th)](/wp-content/uploads/2025/05/2025-05-30_figure1-Ge7mii.png)
[Guest Diary] Exploring a Use Case of Artificial Intelligence Assistance with Understanding an Attack, (Wed, May 28th)
[This is a Guest Diary by Jennifer Wilson, an ISC intern as part of the SANS.edu Bachelor’s Degree in Applied Cybersecurity (BACS) program [1].] As part of my BACS internship with SANS, I setup and maintained a DShield honeypot instance using a physical Raspberry Pi device. As I was putting together each of my attack…
-
ISC Stormcast For Wednesday, May 28th, 2025 https://isc.sans.edu/podcastdetail/9468, (Wed, May 28th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
Securing Your SSH authorized_keys File, (Tue, May 27th)
This is nothing “amazingly new”, but more of a reminder to secure your “authorized_keys” file for SSH. One of the first things I see even simple bots do to obtain persistent access to a UNIX system is to add a key to the authorized_keys file of whatever account they are compromising. So here are a…
-
ISC Stormcast For Tuesday, May 27th, 2025 https://isc.sans.edu/podcastdetail/9466, (Tue, May 27th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-

SVG Steganography, (Mon, May 26th)
Didier recently published several diaries related to steganography. I have to admit that steganography isn’t exactly my favorite topic. It is one of those “neat” infosec toys, but its applicability is limited. Data exfiltration usually does not require proper steganography, but just appending data to an image will usually work just fine. On the other…
-
ISC Stormcast For Friday, May 23rd, 2025 https://isc.sans.edu/podcastdetail/9464, (Fri, May 23rd)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
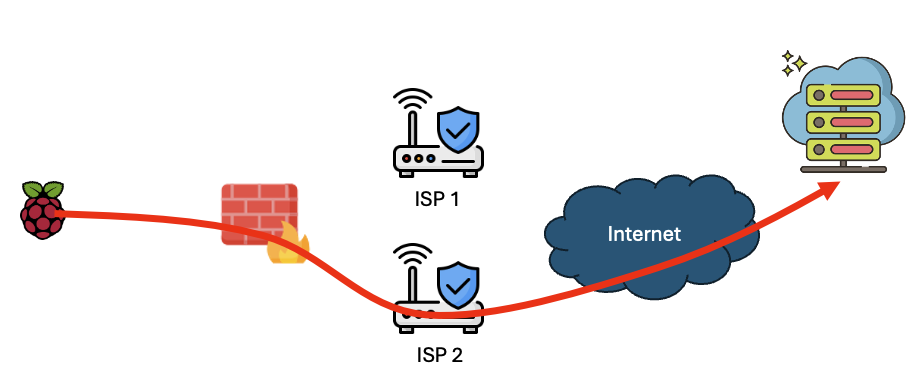
Resilient Secure Backup Connectivity for SMB/Home Users, (Thu, May 22nd)
If you are reading this, you are probably someone who will not easily go without internet connectivity for an extended amount of time. You may also have various home systems that you would like to be able to reach in case of an outage of your primary internet connection. A typical setup would include a…

