-
Web Scanning SonicWall for CVE-2021-20016 – Update, (Wed, May 14th)
I published on the 29 Apr 2025 a diary [1] on scanning activity looking for SonicWall and since this publication this activity has grown 10-fold. Over the past 14 days, several BACS students have reported activity related to SonicWall scans all related for the same 2 URLs [4][5] previously mentioned in my last diary. My…
-
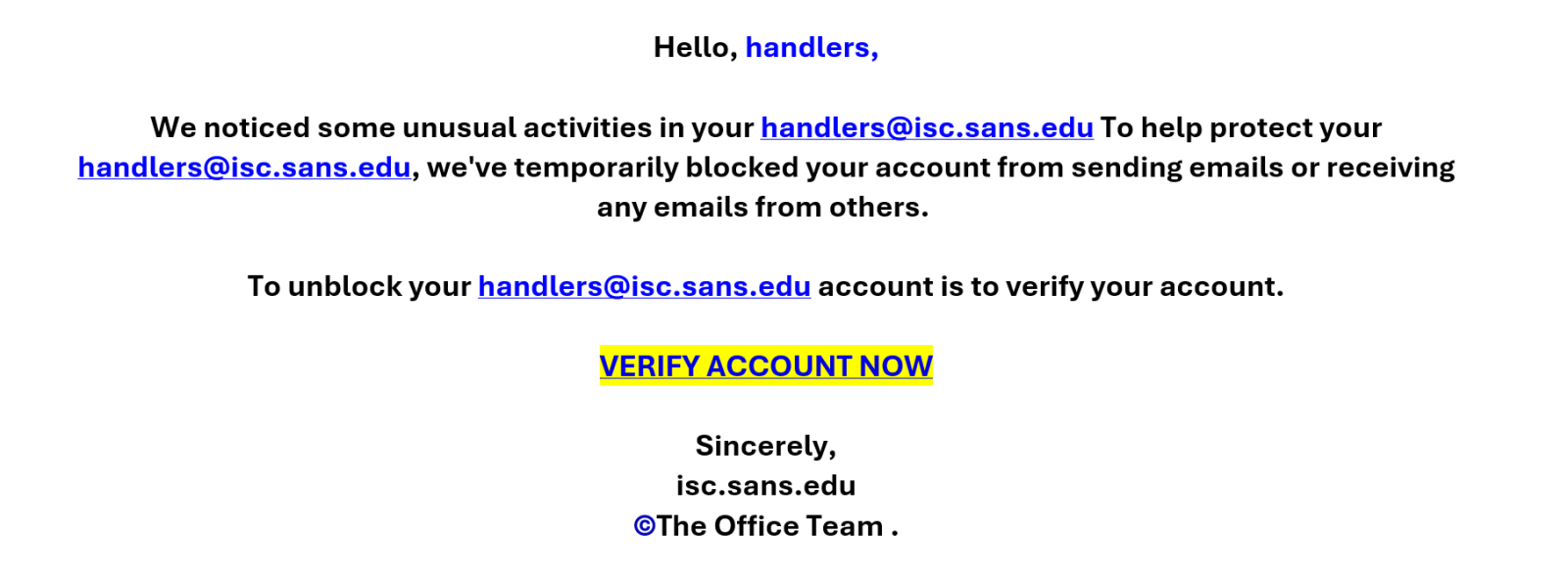
Another day, another phishing campaign abusing google.com open redirects, (Wed, May 14th)
A couple of weeks ago, I came across a phishing campaign that highlights a recurring issue with open redirect vulnerabilities in well-known and trusted services. The phishing message that was delivered to us, here at the ISC, was a variation on the “we blocked your account to keep it safe, to unblock it, login at…
-
ISC Stormcast For Wednesday, May 14th, 2025 https://isc.sans.edu/podcastdetail/9450, (Wed, May 14th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
Microsoft Patch Tuesday: May 2025, (Tue, May 13th)
Today, Microsoft released its expected update for the May patch on Tuesday. This update fixes 78 vulnerabilities. 11 are rated as critical, and 66 as important. Five of the vulnerabilities have already been exploited and two were publicly known but not yet exploited. 70 of the vulnerabilities were patched today, 8 had patches delivered earlier this…
-
ISC Stormcast For Tuesday, May 13th, 2025 https://isc.sans.edu/podcastdetail/9448, (Tue, May 13th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
Apple Updates Everything: May 2025 Edition, (Mon, May 12th)
Apple released its expected update for all its operating systems. The update, in addition to providing new features, patches 65 different vulnerabilities. Many of these vulnerabilities affect multiple operating systems within the Apple ecosystem. Of note is CVE-2025-31200. This vulnerability is already exploited in “targeted attacks”. Apple released patches for this vulnerability in mid-April for…
-
It Is 2025, And We Are Still Dealing With Default IoT Passwords And Stupid 2013 Router Vulnerabilities, (Mon, May 12th)
Unipi Technologies is a company developing programmable logic controllers for a number of different applications like home automation, building management, and industrial controls. The modules produced by Unipi are likely to appeal to a more professional audience. All modules are based on the “Marvis” platform, a customized Linux distribution maintained by Unipi. In the last…
-
ISC Stormcast For Monday, May 12th, 2025 https://isc.sans.edu/podcastdetail/9446, (Mon, May 12th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
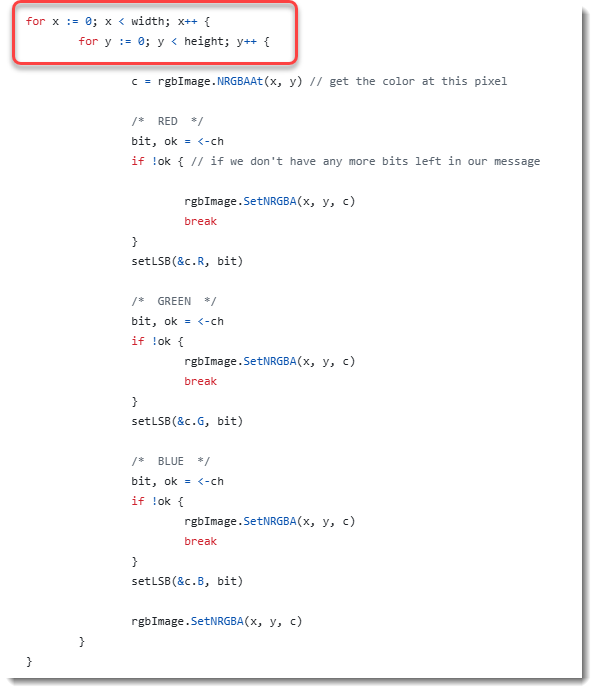
Steganography Challenge: My Solution, (Sat, May 10th)
When I tried to solve “Steganography Challenge” with the same method as I used in “Steganography Analysis With pngdump.py: Bitstreams“, I couldn’t recover the text message. So I looked into the source code of the encoding function EncodeNRGBA, and noticed this: To encode each of the pixels, there are 2 nested for loops: “for x”…
-
ISC Stormcast For Friday, May 9th, 2025 https://isc.sans.edu/podcastdetail/9444, (Fri, May 9th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.

