-
ISC Stormcast For Friday, April 11th, 2025 https://isc.sans.edu/podcastdetail/9404, (Fri, Apr 11th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
ISC Stormcast For Thursday, April 10th, 2025 https://isc.sans.edu/podcastdetail/9402, (Thu, Apr 10th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
![Network Infraxploit [Guest Diary], (Wed, Apr 9th)](/wp-content/uploads/2025/04/Matthew_Gorman_pic1-guOZ2Q.png)
Network Infraxploit [Guest Diary], (Wed, Apr 9th)
[This is a Guest Diary by Matthew Gorman, an ISC intern as part of the SANS.edu BACS program] Background I recently had the opportunity to get hands on with some Cisco networking devices. Due to being a network engineer prior to my current job as a network forensics analyst, I have a relatively solid understanding…
-
ISC Stormcast For Wednesday, April 9th, 2025 https://isc.sans.edu/podcastdetail/9400, (Wed, Apr 9th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
Obfuscated Malicious Python Scripts with PyArmor, (Wed, Apr 9th)
Obfuscation is very important for many developers. They may protect their code for multiple reasons like copyright, anti-cheat (games), or to protect their code from being reused. If an obfuscated program does not mean automatically that it is malicious, it’s often a good sign. For malware developers, obfuscation helps bypass many static security controls and…
-
Microsoft April 2024 Patch Tuesday, (Tue, Apr 8th)
This month, Microsoft has released patches addressing a total of 125 vulnerabilities. Among these, 11 are classified as critical, highlighting the potential for significant impact if exploited. Notably, one vulnerability is currently being exploited in the wild, underscoring the importance of timely updates. While no vulnerabilities were disclosed prior to this patch release, the comprehensive…
-
ISC Stormcast For Tuesday, April 8th, 2025 https://isc.sans.edu/podcastdetail/9398, (Tue, Apr 8th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-

XORsearch: Searching With Regexes, (Mon, Apr 7th)
Xavier asked me a question from one of his FOR610 students: “how can you perform a regex search with XORsearch”? XORsearch is a tool like grep but it performs a brute-force attack on the input file, trying out different encodings like XOR. You can give it a string to search for, but not a regular…
-
ISC Stormcast For Monday, April 7th, 2025 https://isc.sans.edu/podcastdetail/9396, (Mon, Apr 7th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
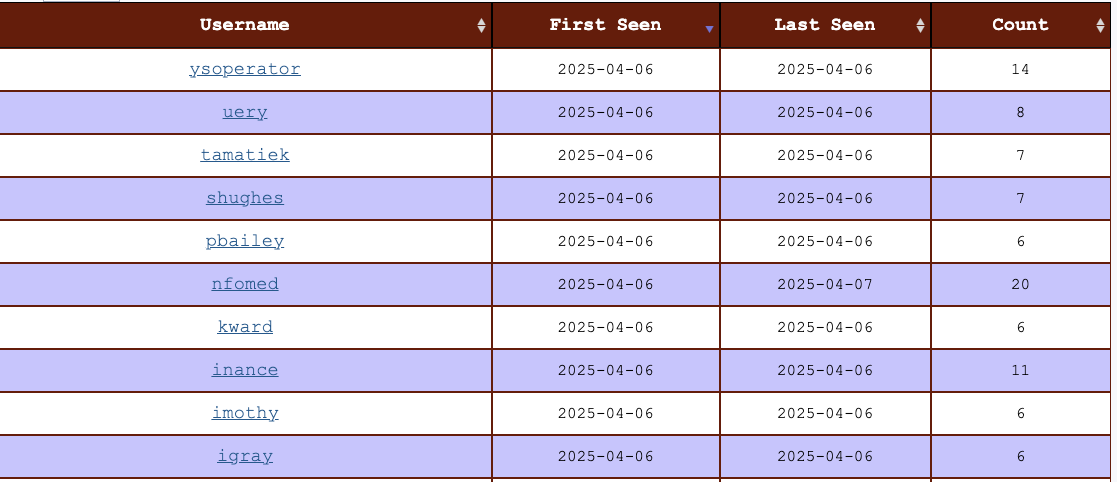
New SSH Username Report, (Sun, Apr 6th)
As you may have noticed by some of my recent diaries, I have spent a bit more time on ssh and telnet credentials. These credentials are collected by Cowrie, the amazing full features SSH and Telnet honeypot maintained by Michel Oosterhof. Cowrie is installed as a component if you install our DShield honeypot. One very simple…

