-
ISC Stormcast For Monday, February 3rd, 2025 https://isc.sans.edu/podcastdetail/9306, (Mon, Feb 3rd)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-

To Simulate or Replicate: Crafting Cyber Ranges, (Fri, Jan 31st)
The Good Stuff First This tool is being shared (calling it a tool is generous) due to the number of times last year I had to create fake internet domains. It adds domains and zones to Windows DNS. This was to help with the many student cyber ranges that got ‘sploited [1] in the name of…
-
ISC Stormcast For Friday, January 31st, 2025 https://isc.sans.edu/podcastdetail/9304, (Fri, Jan 31st)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
![PCAPs or It Didn?t Happen: Exposing an Old Netgear Vulnerability Still Active in 2025 [Guest Diary], (Thu, Jan 30th)](/wp-content/uploads/2025/01/David_Watson_pic1-hWAFGs.png)
PCAPs or It Didn?t Happen: Exposing an Old Netgear Vulnerability Still Active in 2025 [Guest Diary], (Thu, Jan 30th)
[This is a Guest Diary by David Watson, an ISC intern as part of the SANS.edu BACS program] One thing I’ve learned about cybersecurity, particularly during my time here at the Internet Storm Center is this: If you don’t capture detailed network data (like PCAPs), you can easily miss the full picture of an attack,…
-
ISC Stormcast For Thursday, January 30th, 2025 https://isc.sans.edu/podcastdetail/9302, (Thu, Jan 30th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-

From PowerShell to a Python Obfuscation Race!, (Wed, Jan 29th)
Attackers like to mix multiple technologies to improve the deployment of their malicious code. I spotted a small script that drops a Python malware. The file was sent on VirusTotal and got a score of 2/60![1] (SHA256:96bb0777a8e9616bc9ca22ca207cf434a947a3e4286c051ed98ddd39147b3c4f). The script starts by downloading and opening a fake Garmin document through Powershell: powershell.exe -WindowStyle Hidden -Command “[Net.ServicePointManager]::SecurityProtocol =…
-
ISC Stormcast For Wednesday, January 29th, 2025 https://isc.sans.edu/podcastdetail/9300, (Wed, Jan 29th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
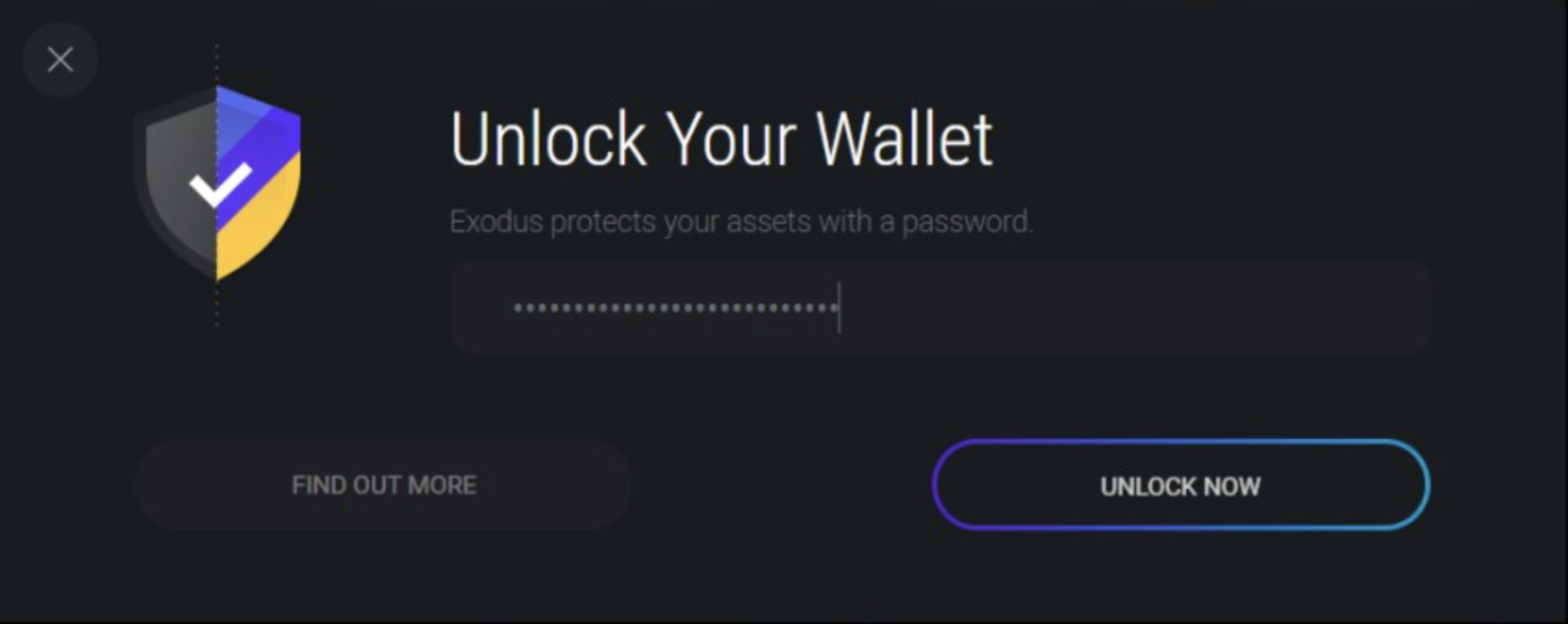
Fileless Python InfoStealer Targeting Exodus, (Tue, Jan 28th)
Exodus is a well-known crypto wallet software[1] and, when you are popular, there are chances that attackers will target you! I already wrote a diary related to this application[2]. Yesterday, I found a new one that behaves differently. My previous diary described a Python script that will patch the original Exodus software. Today, it’s a real…
-
ISC Stormcast For Tuesday, January 28th, 2025 https://isc.sans.edu/podcastdetail/9298, (Tue, Jan 28th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
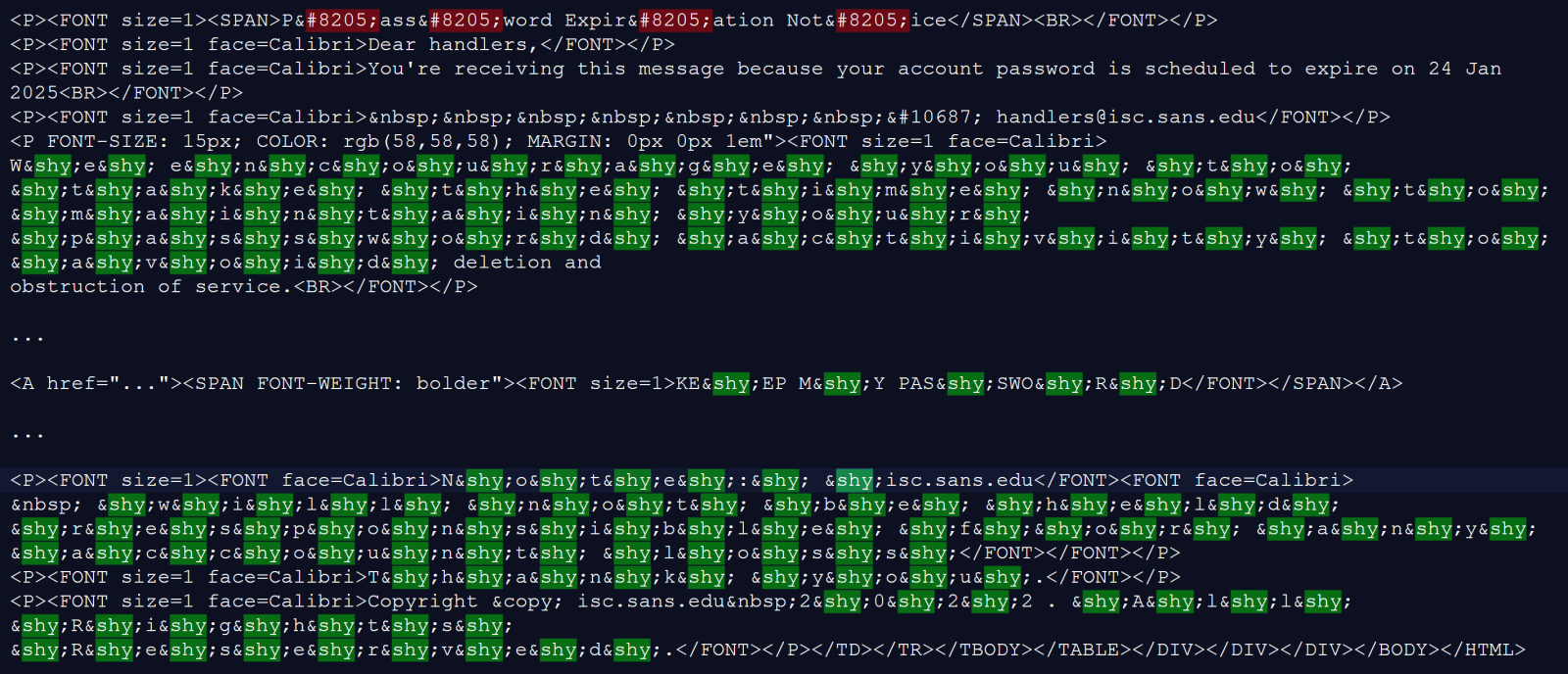
An unusual “shy z-wasp” phishing, (Mon, Jan 27th)
Threat actors who send out phishing messages have long ago learned that zero-width characters and unrendered HTML entities can be quite useful to them. Inserting a zero-width character into a hyperlink can be used to bypass some URL security checks without any negative impact on the function of the link, while any unrendered entities can…

