-
Risks of OOB Access via IP KVM Devices, (Mon, Jan 5th)
Recently, a new “breed” of IP-based KVM devices has been released. In the past, IP-based KVM devices required dedicated “server-grade” hardware using IPMI. They often cost several $100 per server, and are only available for specific systems that support the respective add-on cards. These cards are usually used to provide “Lights Out” access to servers,…
-
ISC Stormcast For Monday, January 5th, 2026 https://isc.sans.edu/podcastdetail/9752, (Mon, Jan 5th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
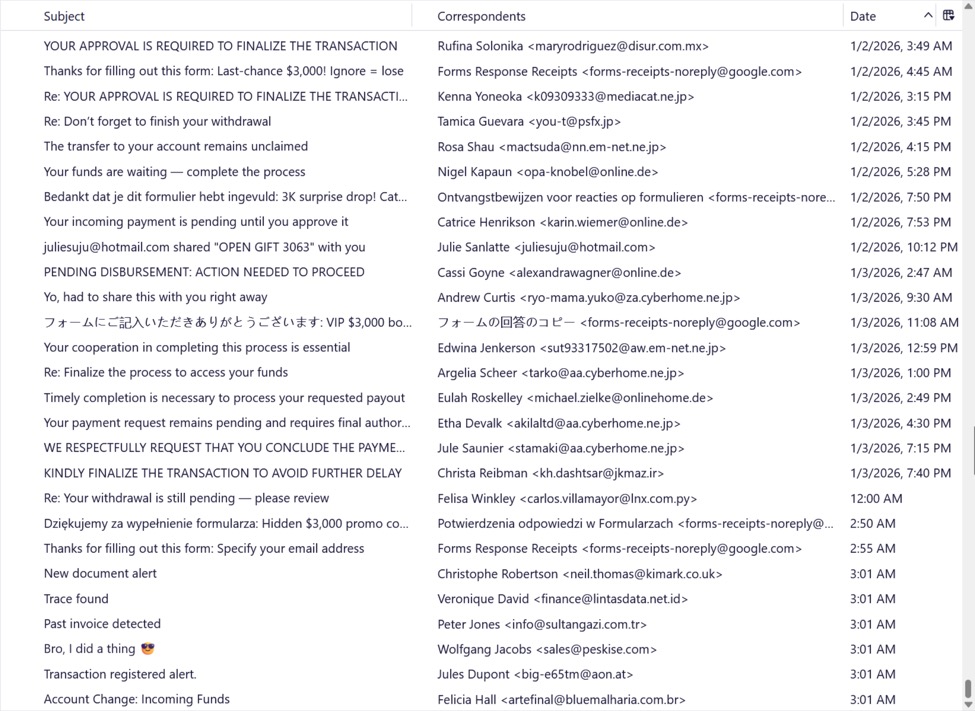
Cryptocurrency Scam Emails and Web Pages As We Enter 2026, (Sun, Jan 4th)
Introduction In October 2025, a work colleague documented a cryptocurrency scam using a fake chatbot. After investigating this, I was able to receive messages from the campaign, and these emails have continued to land in my honeypot account since then. This diary documents the cryptocurrency scam campaign as it continues in 2026. Shown above: My honeypot…
-

Debugging DNS response times with tshark, (Fri, Jan 2nd)
One of my holiday projects was to redo and optimize part of my home network. One of my homelab servers failed in November. I had only thrown the replacement in the rack to get going, but some cleanup was needed. In addition, a lot of other “layer 1” issues had to be fixed by re-crimping some…
-
ISC Stormcast For Sunday, December 28th, 2025 https://isc.sans.edu/podcastdetail/9750, (Sun, Dec 28th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
ISC Stormcast For Monday, December 22nd, 2025 https://isc.sans.edu/podcastdetail/9748, (Mon, Dec 22nd)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
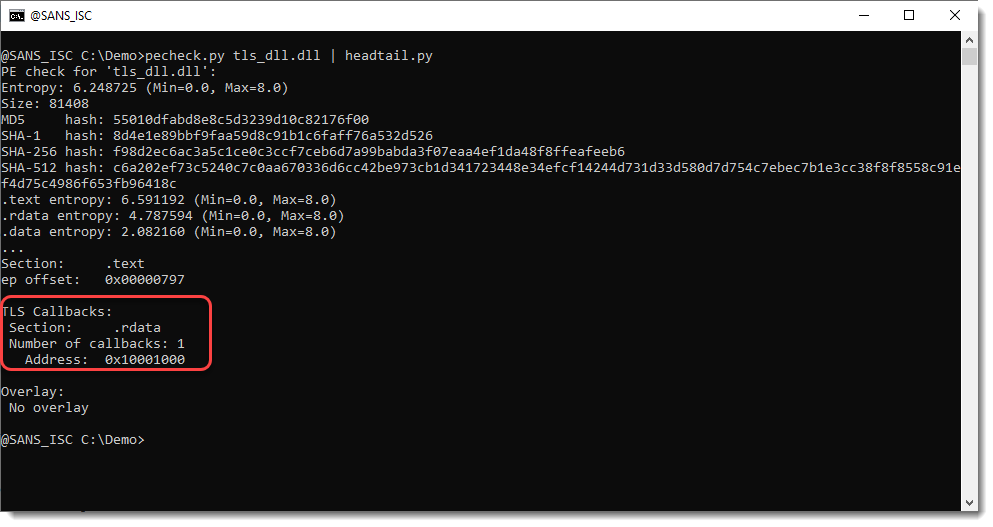
DLLs & TLS Callbacks, (Fri, Dec 19th)
Xavier’s diary entry “Abusing DLLs EntryPoint for the Fun” inspired me to do some tests with TLS Callbacks and DLLs. TLS stands for Thread Local Storage. TLS Callbacks are an execution mechanism in Windows PE files that lets code run automatically when a process or thread starts, before the program’s normal entry point is reached. I’ve…
-
ISC Stormcast For Friday, December 19th, 2025 https://isc.sans.edu/podcastdetail/9746, (Fri, Dec 19th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
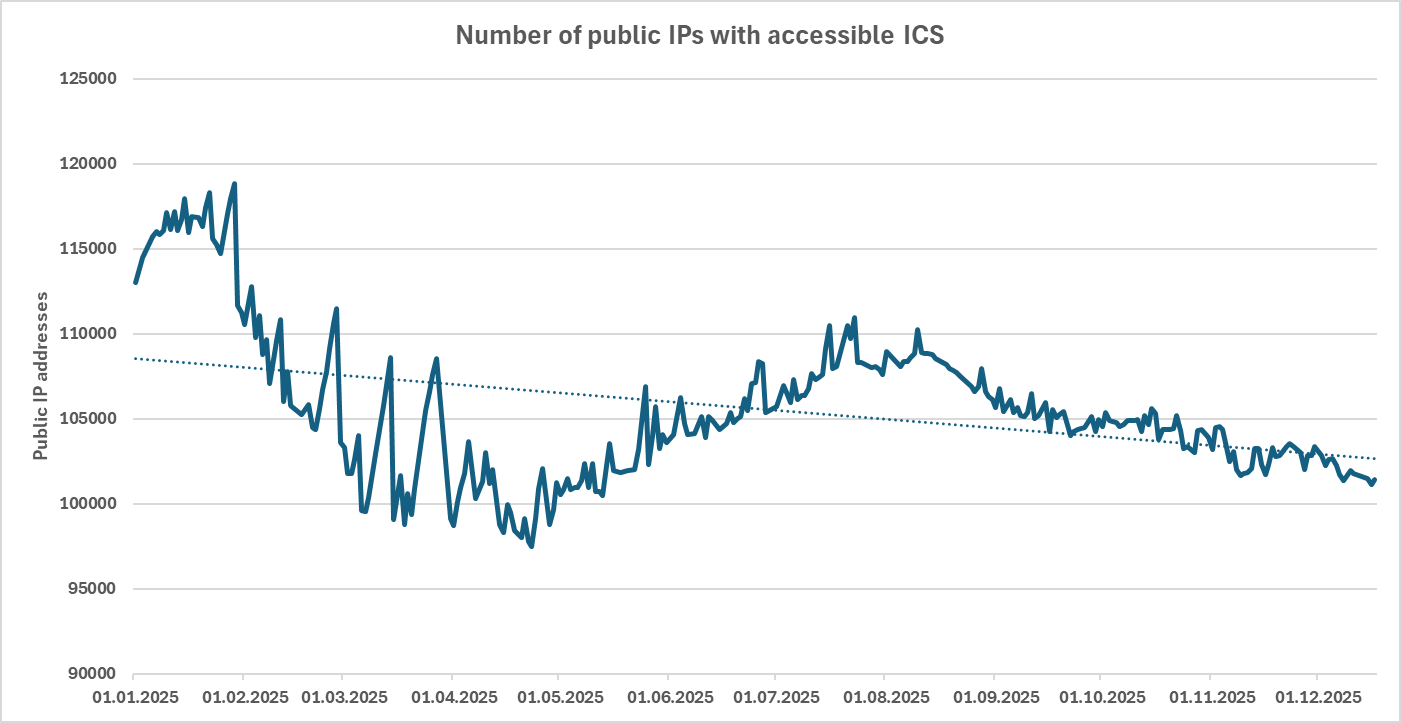
Positive trends related to public IP ranges from the year 2025, (Thu, Dec 18th)
Since the end of the year is quickly approaching, it is undoubtedly a good time to look back at what the past twelve months have brought to us… And given that the entire cyber security profession is about protecting various systems from “bad things” (and we’ve all correspondingly seen more than our share of the…
-
ISC Stormcast For Thursday, December 18th, 2025 https://isc.sans.edu/podcastdetail/9744, (Thu, Dec 18th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.

