I found a sample that is a Word document with an embedded executable. I’ll explain how to extract the embedded executable with my tools.
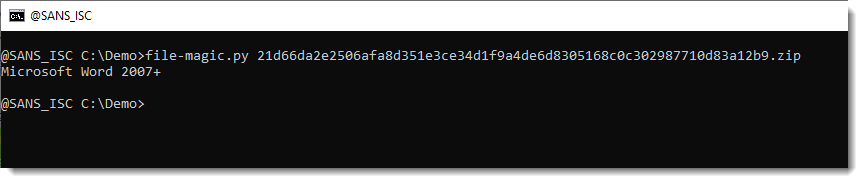
First I check with file-magic.py:
The identification says Word 2007+, so this is an OOXML document. These are ZIP containers that can be analyzed with zipdump.py to take a look inside:
Stream 6 (oleObject1.bin) is an OLE object that embeds the executable. There’s no need to extract that OLE file from the OOXML container, oledump.py can handle this:
The O indicator for stream A2 tells us that this stream is the OLE data structure embedding the executable.
Selecting this stream and using option -i gives us info about the OLE contained, and the contained file:
This metadata gives you the names of the embedded file and it hashes, allowing me to look it up directly on VirusTotal, for example: 3d5fe12c0aa783252431834ed8e370102f47df65165680824b9287faa88e088a.
The file can also be extracted with option -e:
Malicious Word documents like these don’t execute the embedded file when the document is opened: that requires social engeneering to entice the use to double-click the embedded file.
Didier Stevens
Senior handler
blog.DidierStevens.com
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.