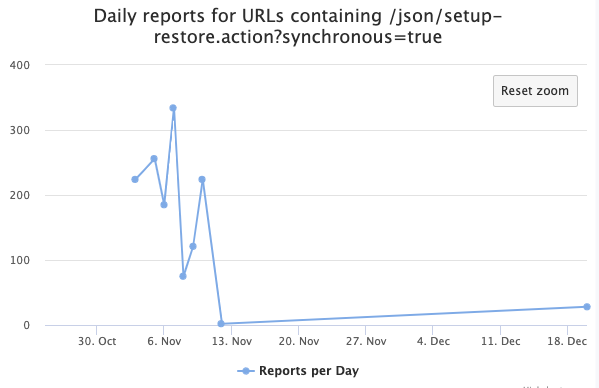
Today, exploit attempts for %%cve:2023-22518%% cross the “significant” threshold for our “First Seen URLs” list. The URL being accessed, “/json/setup-restore.action?synchronous=true“, can be used to bypass authentication [1]. Due to a failure to properly control access to this path, the attacker can execute the “setup-restore” feature, which restores the database using attacker-supplied data and can lead to system command execution.
Attacks for the vulnerability started early in November, shortly after the vulnerability was announced. At the time, the attacks were more targeted to specific hosts. Now we are seeing more widespread scans typical for attackers trying to “clean up” instances earlier attacks may have missed.
One IP address has been particularly active: %%ip:128.199.91.64%%. This IP address, hosted with Digital Ocean, appears to specialize in Confluence vulnerabilities, with sporadic activity back to October 2023.
Interestingly, and somewhat concerning, the IP address is associated with the hostname repo.walnut.asia based on DNS and hostnames in certificates offered by the system. On port 443, a Jira instance is responding. This may indicate that the system itself is compromised. Walnut.asia is an employee health/wellness company, according to their website. I will be reaching out to notify them.
[1] https://blog.projectdiscovery.io/atlassian-confluence-auth-bypass/
—
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.