-
Researchers Scanning the Internet, (Tue, May 20th)
We have been using our data to identify researchers scanning the internet for a few years. Currently, we are tracking 36 groups performing such scans, and our data feed of the IP addresses used contains around 33k addresses [1]. Of course, no clear definition of when a scan is inappropriate exists. Some consider any scan…
-
ISC Stormcast For Tuesday, May 20th, 2025 https://isc.sans.edu/podcastdetail/9458, (Tue, May 20th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
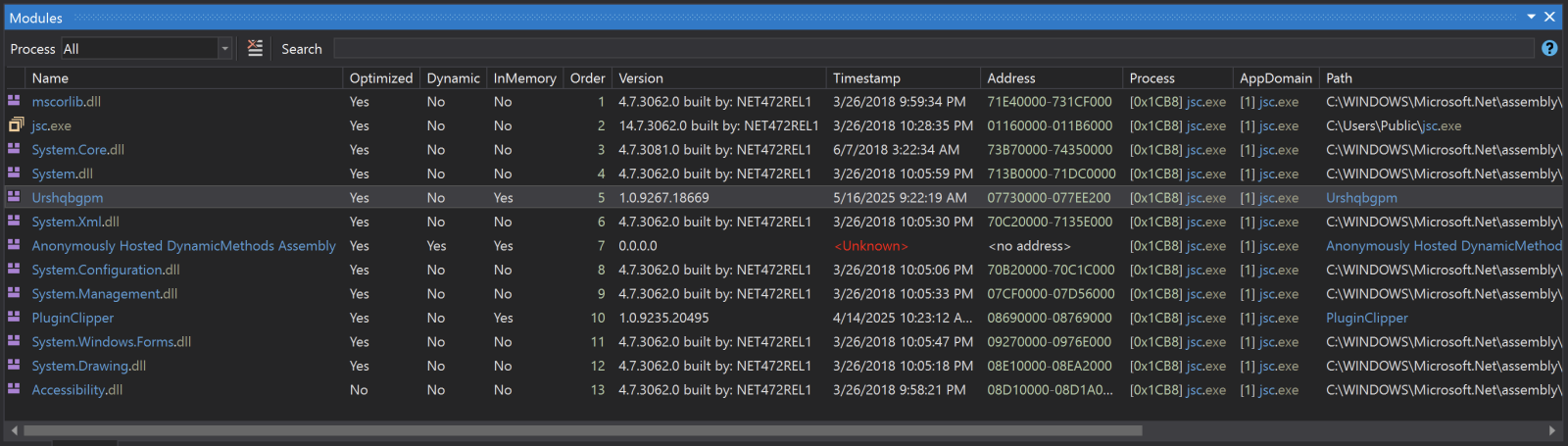
RAT Dropped By Two Layers of AutoIT Code, (Mon, May 19th)
Like .Net, AutoIT[1] remains a popular language for years in the malware ecosystem. It’s a simple language that can interact with all the components of the Windows operating system. I regularly discover AutoIT3 binaries (yes, it can be compiled). This weekend, I found a malware delivered through a double layer of AutoIT code! The initial file…
-
ISC Stormcast For Monday, May 19th, 2025 https://isc.sans.edu/podcastdetail/9456, (Mon, May 19th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
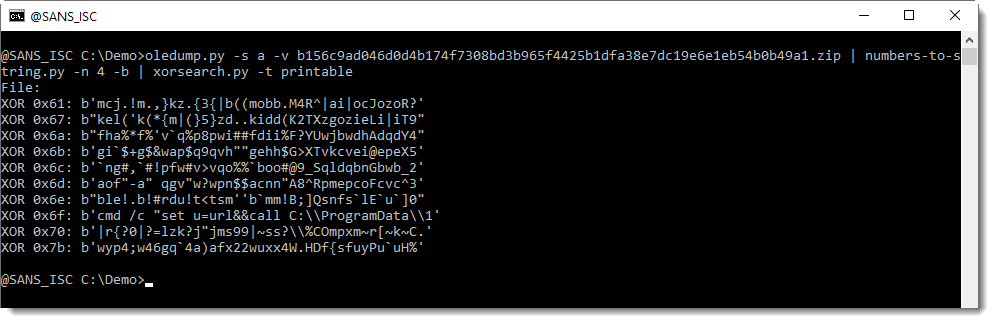
xorsearch.py: Python Functions, (Sat, May 17th)
A couple years ago I published tool xorsearch.py for this diary entry: “Small Challenge: A Simple Word Maldoc – Part 4“. It could be used to search for XOR-encoded text: This was a beta version, and its user interface was subject to change. The version I released recently is a rewrite, and option -t no…
-
ISC Stormcast For Friday, May 16th, 2025 https://isc.sans.edu/podcastdetail/9454, (Fri, May 16th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
ISC Stormcast For Thursday, May 15th, 2025 https://isc.sans.edu/podcastdetail/9452, (Thu, May 15th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
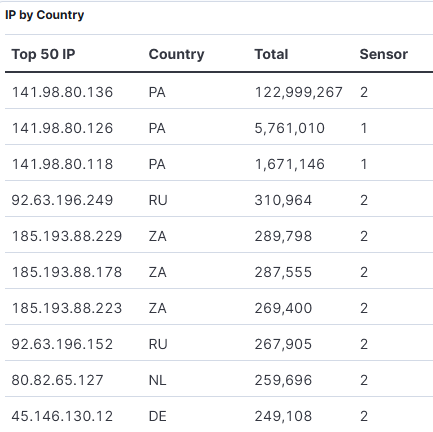
Web Scanning SonicWall for CVE-2021-20016 – Update, (Wed, May 14th)
I published on the 29 Apr 2025 a diary [1] on scanning activity looking for SonicWall and since this publication this activity has grown 10-fold. Over the past 14 days, several BACS students have reported activity related to SonicWall scans all related for the same 2 URLs [4][5] previously mentioned in my last diary. My…
-
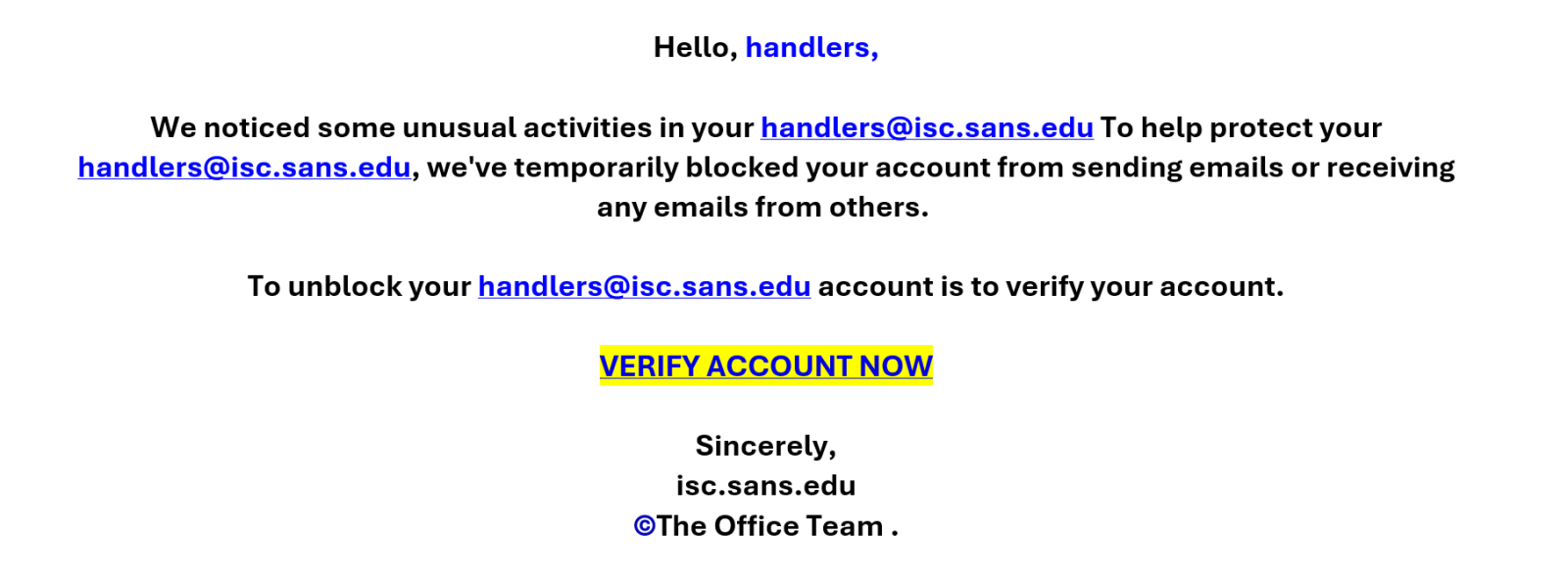
Another day, another phishing campaign abusing google.com open redirects, (Wed, May 14th)
A couple of weeks ago, I came across a phishing campaign that highlights a recurring issue with open redirect vulnerabilities in well-known and trusted services. The phishing message that was delivered to us, here at the ISC, was a variation on the “we blocked your account to keep it safe, to unblock it, login at…
-
ISC Stormcast For Wednesday, May 14th, 2025 https://isc.sans.edu/podcastdetail/9450, (Wed, May 14th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.

