-
ISC Stormcast For Wednesday, August 13th, 2025 https://isc.sans.edu/podcastdetail/9568, (Wed, Aug 13th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
Microsoft August 2025 Patch Tuesday, (Tue, Aug 12th)
This month’s Microsoft patch update addresses a total of 111 vulnerabilities, with 17 classified as critical. Among these, one vulnerability was disclosed prior to the patch release, marking it as a zero-day. While none of the vulnerabilities have been exploited in the wild, the critical ones pose significant risks, including remote code execution and elevation…
-
ISC Stormcast For Tuesday, August 12th, 2025 https://isc.sans.edu/podcastdetail/9566, (Tue, Aug 12th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
ISC Stormcast For Monday, August 11th, 2025 https://isc.sans.edu/podcastdetail/9564, (Mon, Aug 11th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
Google Paid Ads for Fake Tesla Websites, (Sun, Aug 10th)
In recent media events, Tesla has demoed progressively more sophisticated versions of its Optimus robots. The sales pitch is pretty simple: “Current AI” is fun, but what we really need is not something to create more funny kitten pictures. We need AI to load and empty dishwashers, fold laundry, and mow lawns. But the robot…
-
ISC Stormcast For Friday, August 8th, 2025 https://isc.sans.edu/podcastdetail/9562, (Fri, Aug 8th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
ISC Stormcast For Thursday, August 7th, 2025 https://isc.sans.edu/podcastdetail/9560, (Thu, Aug 7th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
![Mass Internet Scanning from ASN 43350 [Guest Diary], (Thu, Aug 7th)](/wp-content/uploads/2025/08/Duncan_Woosley_pic1-8XV3Eu.png)
Mass Internet Scanning from ASN 43350 [Guest Diary], (Thu, Aug 7th)
[This is a Guest Diary by Duncan Woosley, an ISC intern as part of the SANS.edu BACS program] During the last three months I’ve had a DShield sensor online and collecting data from a deployment in AWS. This week I did some statistical analysis of the last three months of data and found surprising result.…
-
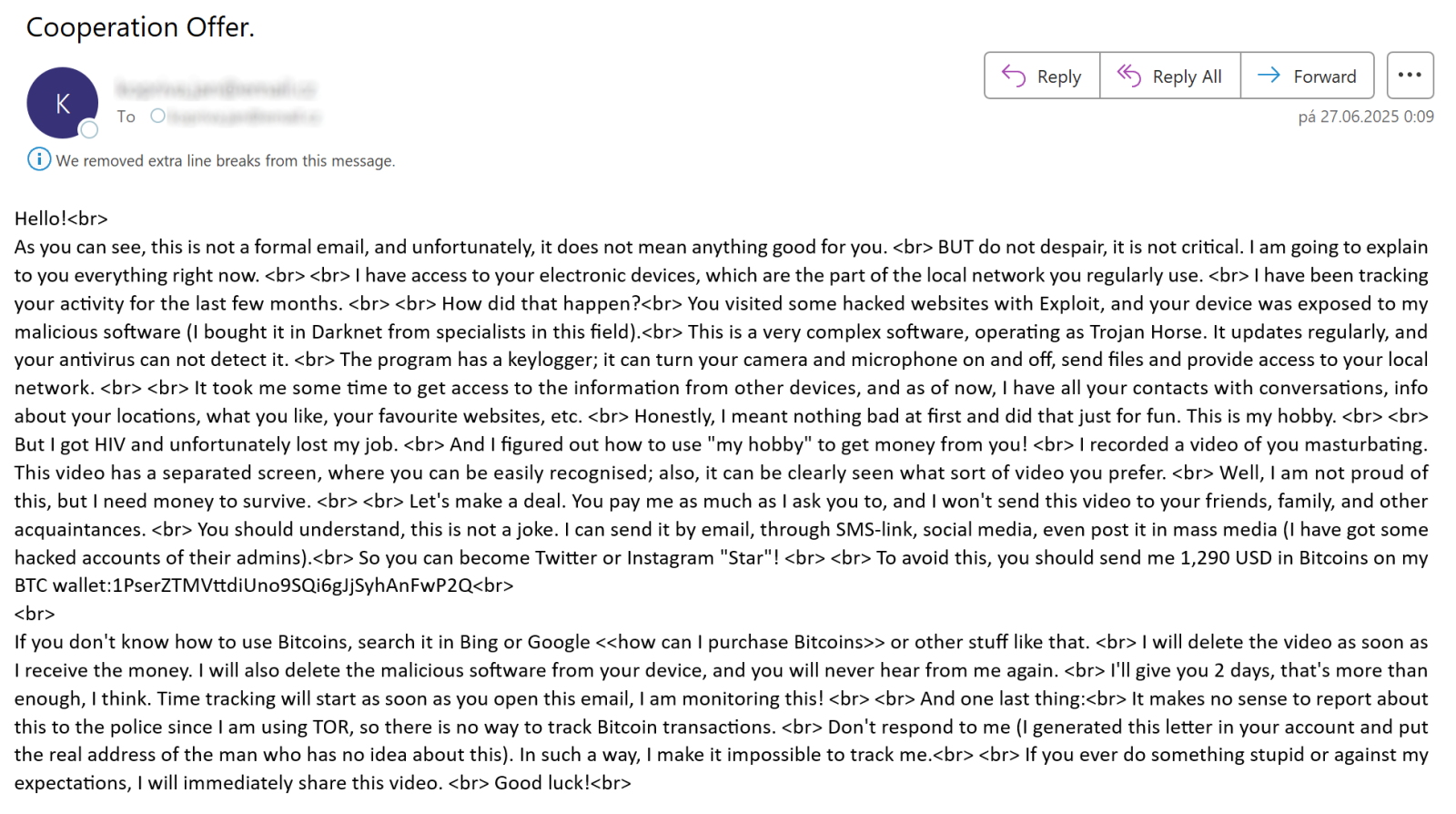
Do sextortion scams still work in 2025?, (Wed, Aug 6th)
Sextortion e-mails have been with us for quite a while, and these days, most security professionals tend to think of them more in terms of an “e-mail background noise” rather than as if they posed any serious threat. Given that their existence is reasonably well-known even among general public, this viewpoint would seem to be…
-
ISC Stormcast For Wednesday, August 6th, 2025 https://isc.sans.edu/podcastdetail/9558, (Wed, Aug 6th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.

