-
ISC Stormcast For Friday, June 27th, 2025 https://isc.sans.edu/podcastdetail/9508, (Fri, Jun 27th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
ISC Stormcast For Thursday, June 26th, 2025 https://isc.sans.edu/podcastdetail/9506, (Thu, Jun 26th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
ISC Stormcast For Wednesday, June 25th, 2025 https://isc.sans.edu/podcastdetail/9504, (Wed, Jun 25th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
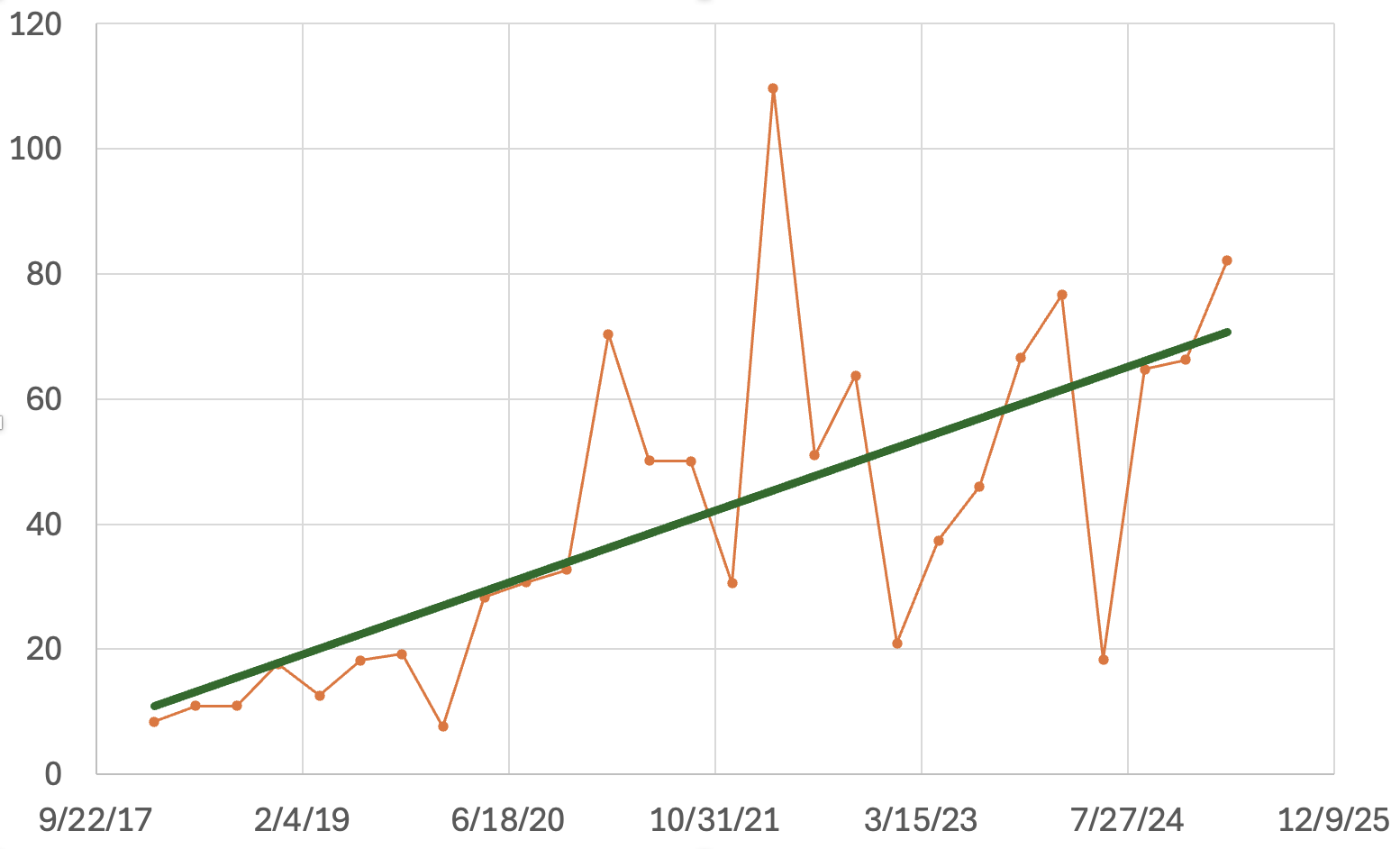
Quick Password Brute Forcing Evolution Statistics, (Tue, Jun 24th)
We have collected SSH and telnet honeypot data in various forms for about 10 years. Yesterday’s diaries, and looking at some new usernames attempted earlier today, made me wonder if botnets just add new usernames or remove old ones from their lists. So I pulled some data from our database to test this hypothesis. I…
-
ISC Stormcast For Tuesday, June 24th, 2025 https://isc.sans.edu/podcastdetail/9502, (Tue, Jun 24th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-

Scans for Ichano AtHome IP Cameras, (Mon, Jun 23rd)
Ichano’s “AtHome Camera” is a bit of a different approach to home surveillance cameras [1]. Instead of a hardware camera solution, this product is a software solution that turns existing devices like computers and tablets into webcams. The software implements features we know from similar IP camera devices. It enabled streaming of images and remote…
-
ISC Stormcast For Monday, June 23rd, 2025 https://isc.sans.edu/podcastdetail/9500, (Mon, Jun 23rd)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
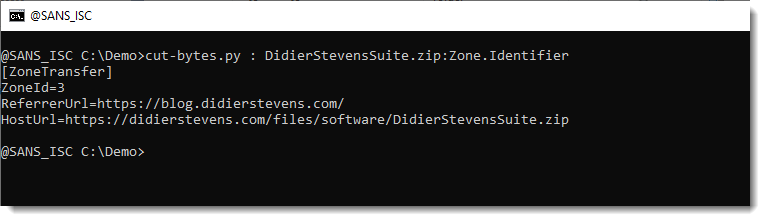
ADS & Python Tools, (Sat, Jun 21st)
Ehsaan Mavani talks about Alternate Data Streams (ADS) in diary entry “Alternate Data Streams ? Adversary Defense Evasion and Detection [Guest Diary]“. I’m taking this as an opportunity to remind you that Python tools on Windows and an NTFS disk, can access alternate data streams. Like my tool cut-bytes.py, here I use it to show…
-
ISC Stormcast For Friday, June 20th, 2025 https://isc.sans.edu/podcastdetail/9498, (Fri, Jun 20th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
![Don?t Make it Easier than it Already is?..Default Passwords [Guest Diary], (Wed, Jun 18th)](/wp-content/uploads/2025/06/Matthew_Paul_Picture1-rHFJBw.png)
Don?t Make it Easier than it Already is?..Default Passwords [Guest Diary], (Wed, Jun 18th)
[This is a Guest Diary by Matthew Paul, an ISC intern as part of the SANS.edu BACS program] Over the past few months, I’ve been working under a SANS Internet Storm Center (ISC) Sr. Handler as part of the SANS Degree Program ISC Internship. The first objective of the internship is setting up a forward-facing…

