-
ISC Stormcast For Monday, January 12th, 2026 https://isc.sans.edu/podcastdetail/9762, (Mon, Jan 12th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
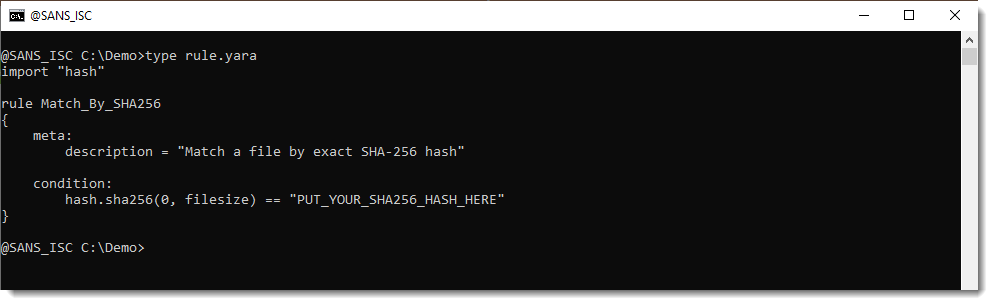
YARA-X 1.11.0 Release: Hash Function Warnings, (Sun, Jan 11th)
YARA-X’s 1.11.0 release brings a new feature: hash function warnings. When you write a YARA rule to match a cryptographic hash (either the full file content or a part of it), what’s actually going on are string comparisons: Function hash.sha256 returns a string (the hexadecimal SHA256 hash it calculated) and that is compared to a…
-
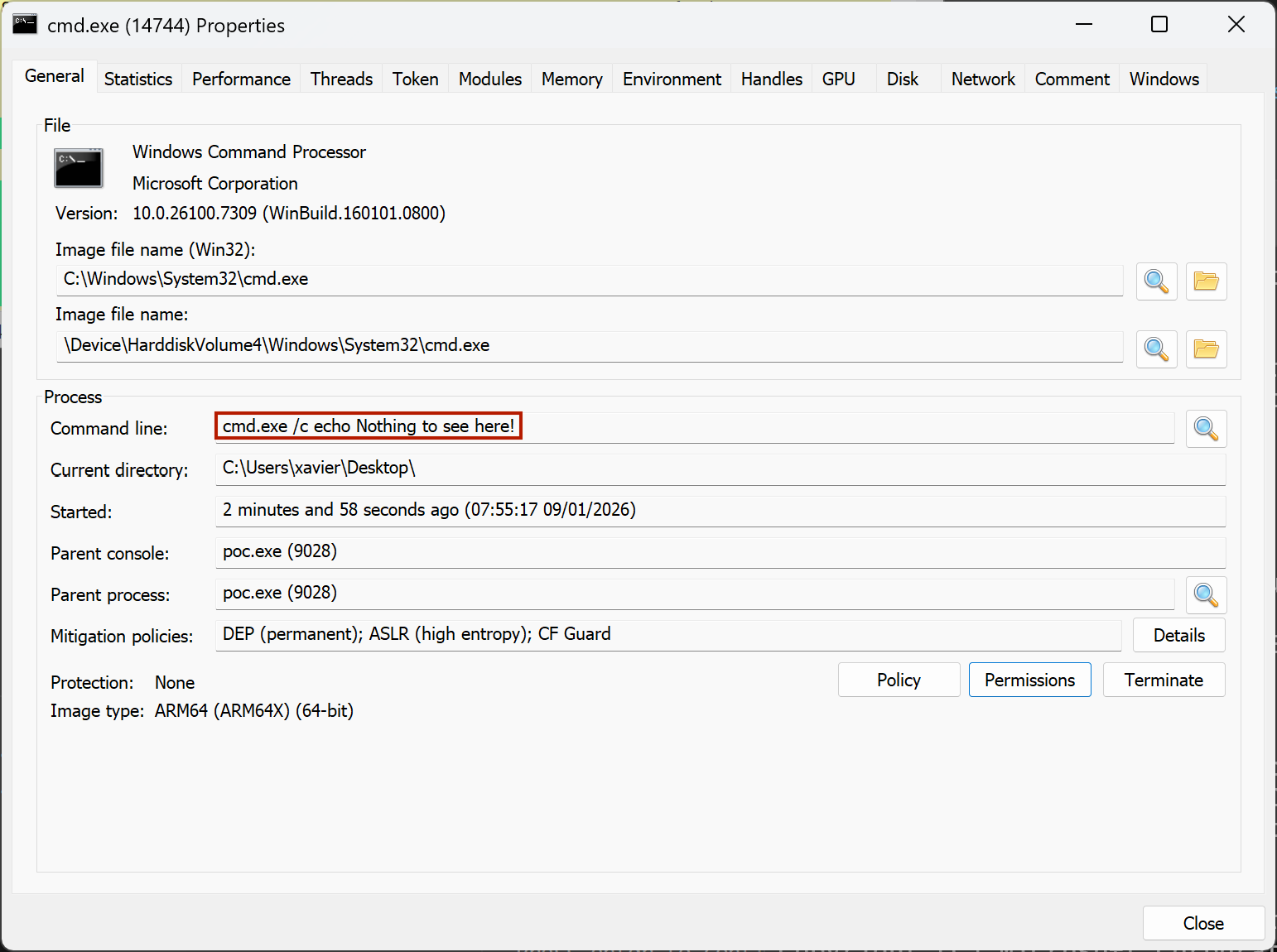
Malicious Process Environment Block Manipulation, (Fri, Jan 9th)
Reverse engineers must have a good understanding of the environment where malware are executed (read: the operating system). In a previous diary, I talked about malicious code that could be executed when loading a DLL[1]. Today, I’ll show you how a malware can hide suspicious information related to created processes. The API call CreateProcess() is…
-
ISC Stormcast For Friday, January 9th, 2026 https://isc.sans.edu/podcastdetail/9760, (Fri, Jan 9th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
ISC Stormcast For Thursday, January 8th, 2026 https://isc.sans.edu/podcastdetail/9758, (Thu, Jan 8th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
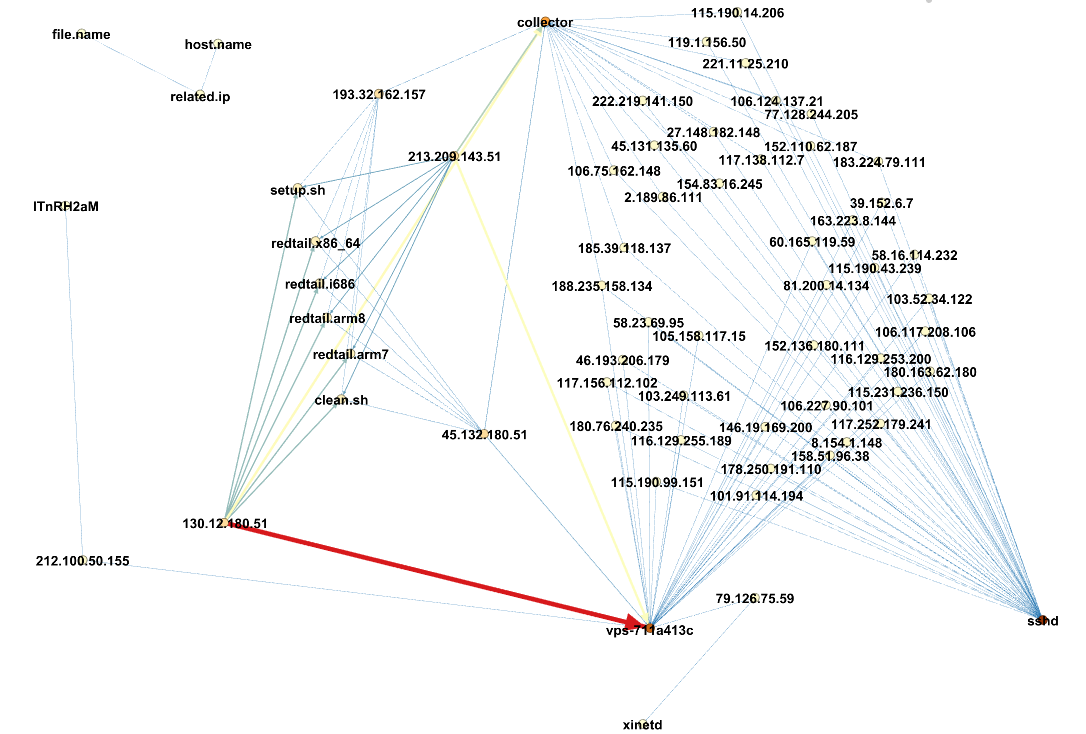
Analysis using Gephi with DShield Sensor Data, (Wed, Jan 7th)
I’m always looking for new ways of manipulating the data captured by my DShield sensor [1]. This time I used Gephi [2] and Graphiz [3] a popular and powerful tool for visualizing and exploring relationships between nodes, to examine the relationship between the source IP, filename and which sensor got a copy of the file.…
-
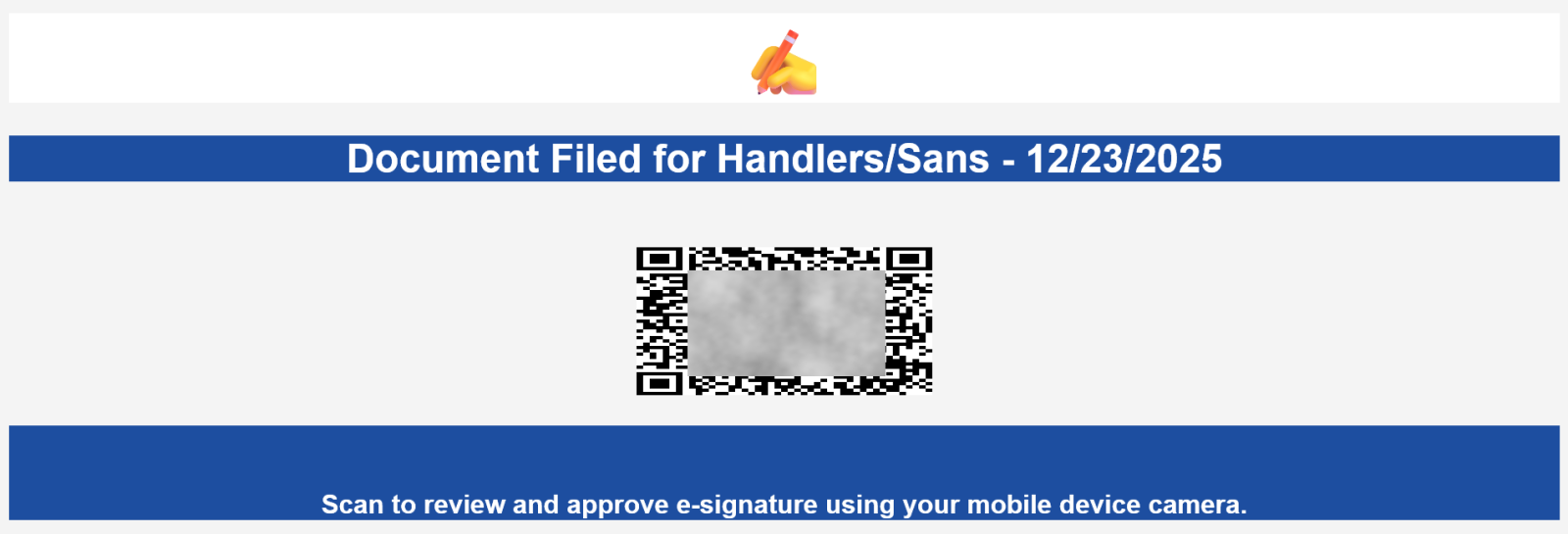
A phishing campaign with QR codes rendered using an HTML table, (Wed, Jan 7th)
Malicious use of QR codes has long been ubiquitous, both in the real world as well as in electronic communication. This is hardly surprising given that a scan of a QR code can lead one to a phishing page as easily as clicking a link in an e-mail. No more surprising is that vendors of…
-
ISC Stormcast For Wednesday, January 7th, 2026 https://isc.sans.edu/podcastdetail/9756, (Wed, Jan 7th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
Tool Review: Tailsnitch, (Tue, Jan 6th)
In yesterday’s podcast, I mentioned “tailsnitch”, a new tool to audit Tailscale configurations. Tailscale is an easy-to-use overlay to Wireguard. It is probably best compared to STUN servers in VoIP in that it allows devices behind NAT to connect directly to each other. Tailscale just helps negotiate the setup, and once the connection is established,…
-
ISC Stormcast For Tuesday, January 6th, 2026 https://isc.sans.edu/podcastdetail/9754, (Tue, Jan 6th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.

