-
ISC Stormcast For Tuesday, March 10th, 2026 https://isc.sans.edu/podcastdetail/9842, (Tue, Mar 10th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
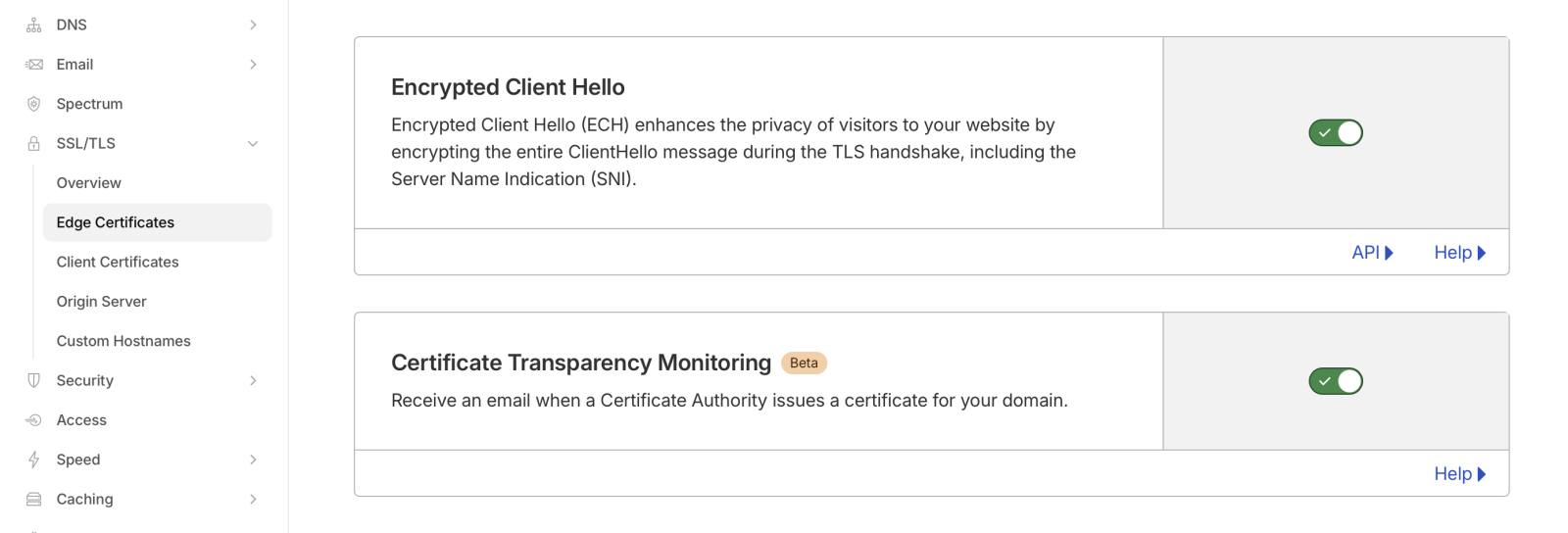
Encrypted Client Hello: Ready for Prime Time?, (Mon, Mar 9th)
Last week, two related RFCs were published: RFC 9848: Bootstrapping TLS Encrypted ClientHello with DNS Service Bindings RFC 9849: TLS Encrypted Client Hello These TLS extensions have been discussed quite a bit already, and Cloudflare, one of the early implementers and proponents, has been in use for a while. Amidst an increased concern about threats to privacy…
-
ISC Stormcast For Monday, March 9th, 2026 https://isc.sans.edu/podcastdetail/9840, (Mon, Mar 9th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
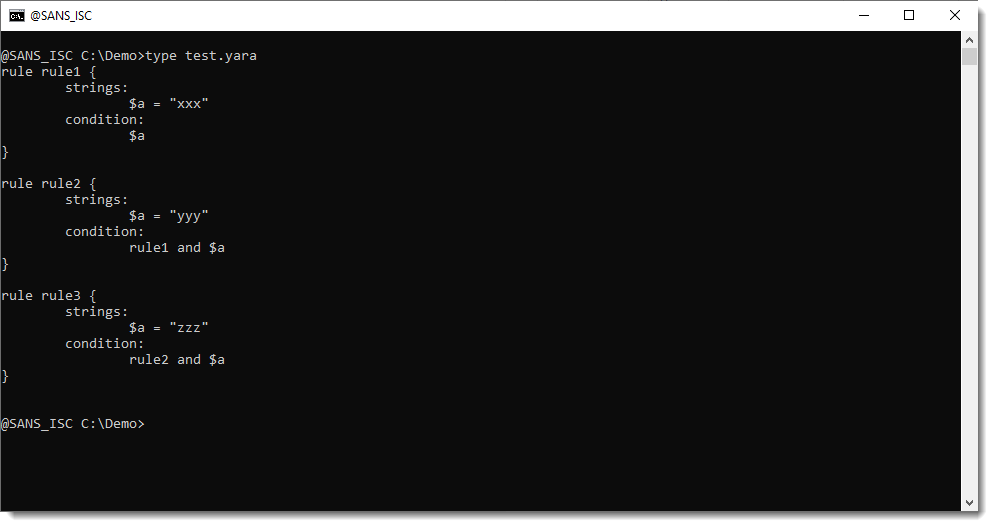
YARA-X 1.14.0 Release, (Sat, Mar 7th)
YARA-X’s 1.14.0 release brings 4 improvements and 2 bugfixes. One of the improvements is a new CLI command: deps. This command shows you the dependencies of rules. Here is an example. Rule rule1 has no dependencies, rule rule2 depends on rule rule1 and rule rule3 depends on rule rule2: Running the deps command on these rules…
-
ISC Stormcast For Friday, March 6th, 2026 https://isc.sans.edu/podcastdetail/9838, (Fri, Mar 6th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
ISC Stormcast For Thursday, March 5th, 2026 https://isc.sans.edu/podcastdetail/9836, (Thu, Mar 5th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
![Differentiating Between a Targeted Intrusion and an Automated Opportunistic Scanning [Guest Diary], (Wed, Mar 4th)](/wp-content/uploads/2026/03/Joseph_Gruen_Picture1-hmhPDl.png)
Differentiating Between a Targeted Intrusion and an Automated Opportunistic Scanning [Guest Diary], (Wed, Mar 4th)
[This is a Guest Diary by Joseph Gruen, an ISC intern as part of the SANS.edu BACS program] The internet is under constant, automated siege. Every publicly reachable IP address is probed continuously by bots and scanners hunting for anything that can be exploited or retrieved. It’s not because there is a specific target, but…
-
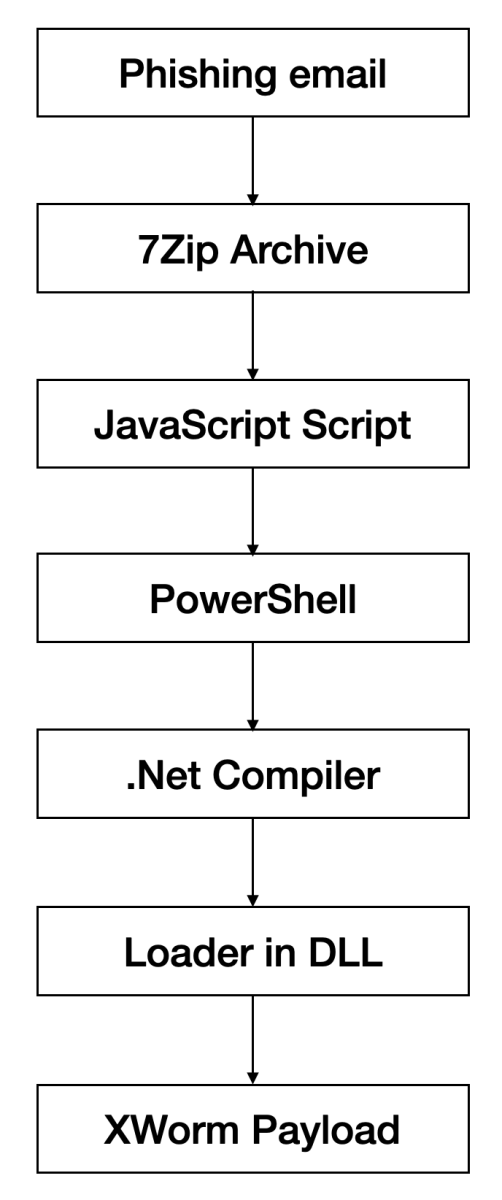
Want More XWorm?, (Wed, Mar 4th)
And another XWorm[1] wave in the wild! This malware family is not new and heavily spread but delivery techniques always evolve and deserve to be described to show you how threat actors can be imaginative! This time, we are facing another piece of multi-technology malware. Here is a quick overview: The Javascript is a classic obfuscated one: No need…
-
ISC Stormcast For Wednesday, March 4th, 2026 https://isc.sans.edu/podcastdetail/9834, (Wed, Mar 4th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
Bruteforce Scans for CrushFTP , (Tue, Mar 3rd)
CrushFTP is a Java-based open source file transfer system. It is offered for multiple operating systems. If you run a CrushFTP instance, you may remember that the software has had some serious vulnerabilities: CVE-2024-4040 (the template-injection flaw that let unauthenticated attackers escape the VFS sandbox and achieve RCE), CVE-2025-31161 (the auth-bypass that handed over the…

