-
ISC Stormcast For Wednesday, February 11th, 2026 https://isc.sans.edu/podcastdetail/9804, (Wed, Feb 11th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
Microsoft Patch Tuesday – January 2026, (Tue, Feb 10th)
Today’s patch Tuesday addresses 59 different vulnerabilities (plus two Chromium vulnerabilities affecting Microsoft Edge). While this is a lower-than-normal number, this includes six vulnerabilities that are already exploited. Three vulnerabilities have already been exploited and made public. In addition, five critical vulnerabilities are included in this patch Tuesday. Vulnerabilities of Interest: The three already exploited…
-
ISC Stormcast For Tuesday, February 10th, 2026 https://isc.sans.edu/podcastdetail/9802, (Tue, Feb 10th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
ISC Stormcast For Monday, February 9th, 2026 https://isc.sans.edu/podcastdetail/9800, (Mon, Feb 9th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
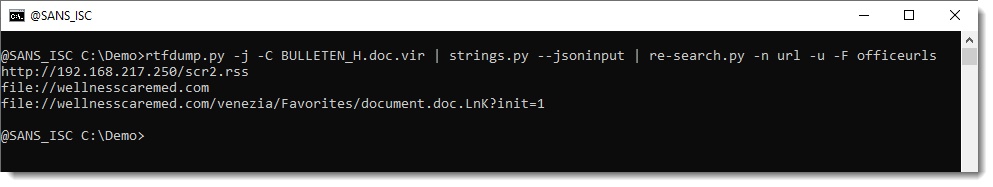
Quick Howto: Extract URLs from RTF files, (Mon, Feb 9th)
Malicious RTF (Rich Text Format) documents are back in the news with the exploitation of CVE-2026-21509 by APT28. The malicious RTF documents BULLETEN_H.doc and Consultation_Topics_Ukraine(Final).doc mentioned in the news are RTF files (despite their .doc extension, a common trick used by threat actors). Here is a quick tip to extract URLs from RTF files. Use the following…
-
YARA-X 1.13.0 Release, (Mon, Feb 9th)
YARA-X’s 1.13.0 release brings 4 improvements and 4 bugfixes. Didier Stevens Senior handler blog.DidierStevens.com (c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
ISC Stormcast For Friday, February 6th, 2026 https://isc.sans.edu/podcastdetail/9798, (Fri, Feb 6th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-
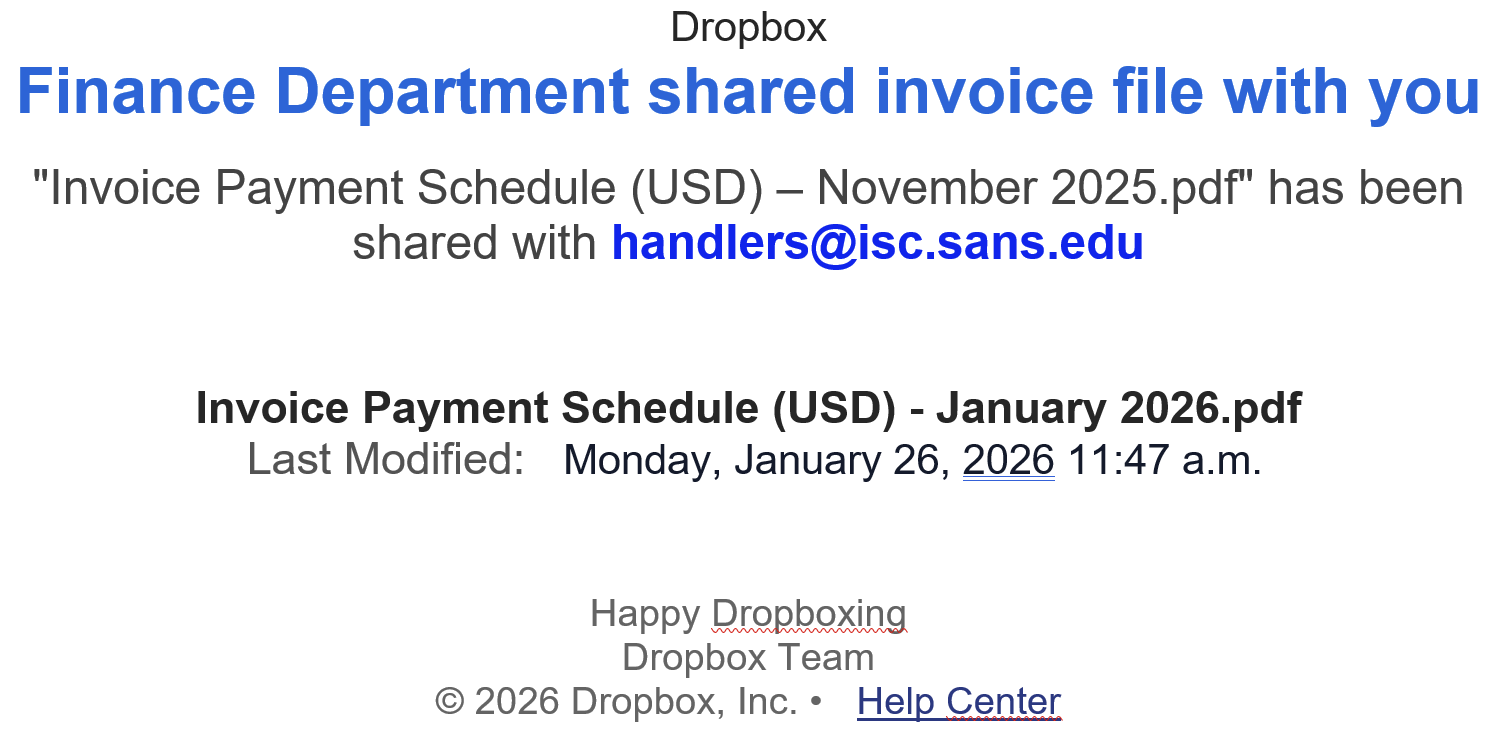
Broken Phishing URLs, (Thu, Feb 5th)
For a few days, many phishing emails that landed into my mailbox contain strange URLs. They are classic emails asking you to open a document, verify your pending emails, … But the format of the URLs is broken! In a URL, parameters are extra pieces of information added after a question mark (?) to tell…
-
ISC Stormcast For Thursday, February 5th, 2026 https://isc.sans.edu/podcastdetail/9796, (Thu, Feb 5th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
-

Malicious Script Delivering More Maliciousness, (Wed, Feb 4th)
Today, I received an interesting email with a malicious attachment. When I had a look at the automatic scan results, it seemed to be a malicious script to create a Chrome Injector to steal data. Because InfoStealers are very common these days, it looked “legit” but there was something different. The .bat file looks to…

